Technology upgrade is most common factor to complete daily tasks in minimal time. Most up gradation is done to secure internal/ external networks. We usually find QR codes everywhere. From buying groceries to making payments or another methods of signing into the online accounts. According to ethical hacking researcher of international institute of cyber security QR codes can also be biggest risk if used unknowingly.
Whatsapp Web is very popular among its users. Recently we have shown how QRLJacking can be used to access any Whatsapp account. Today we will show you another tool used in creating malicious QRL codes with some existing payloads.
Qrlgen is used to generate generic malformed QRL codes. Qrlgen comes handy while testing QRL’s code scanners or how application handle QRL code data. Custom wordlist are also used to create QRLcodes.
- For testing we are using Kali Linux 2019.1 amd64.
- Before installing must ensure python3 is installed.
- For installing type sudo apt-get update && sudo apt-get install python3
- Then install sudo apt-get install python3-pip
- Type git clone https://github.com/h0nus/QRGen.git
root@kali:~/Downloads# git clone https://github.com/h0nus/QRGen.git
Cloning into 'QRGen'…
remote: Enumerating objects: 86, done.
remote: Counting objects: 100% (86/86), done.
remote: Compressing objects: 100% (78/78), done.
remote: Total 86 (delta 26), reused 4 (delta 1), pack-reused 0
Unpacking objects: 100% (86/86), done.
- Type cd QRGen && type ls
root@kali:~/Downloads# cd QRGen/
root@kali:~/Downloads/QRGen#
root@kali:~/Downloads/QRGen# ls
demo.gif qrgen.py README.md requirements.txt words
- Type pip3 install -r requirements.txt
root@kali:~/Downloads/QRGen# pip3 install -r requirements.txt
Collecting qrcode (from -r requirements.txt (line 1))
Downloading https://files.pythonhosted.org/packages/42/87/4a3a77e59ab7493d64da1f69bf1c2e899a4cf81e51b2baa855e8cc8115be/qrcode-6.1-py2.py3-none-any.whl
Requirement already satisfied: Pillow in /usr/lib/python3/dist-packages (from -r requirements.txt (line 2)) (5.3.0)
Collecting argparse (from -r requirements.txt (line 3))
Downloading https://files.pythonhosted.org/packages/f2/94/3af39d34be01a24a6e65433d19e107099374224905f1e0cc6bbe1fd22a2f/argparse-1.4.0-py2.py3-none-any.whl
Requirement already satisfied: six in /usr/lib/python3/dist-packages (from qrcode->-r requirements.txt (line 1)) (1.12.0)
Installing collected packages: qrcode, argparse
Successfully installed argparse-1.4.0 qrcode-6.1
- Type python3 qrgen.py
root@kali:~/Downloads/QRGen# python3 qrgen.py
e88 88e 888 88e e88'Y88
d888 888b 888 888D d888 'Y ,e e, 888 8e
C8888 8888D 888 88" C8888 eeee d88 88b 888 88b
Y888 888P 888 b, Y888 888P 888 , 888 888
"88 88" 888 88b, "88 88" "YeeP" 888 888
b
8b, QRGen ~ v0.1 ~ by h0nususage: qrgen.py -l [number]
usage: qrgen.py -w [/path/to/custom/wordlist]
Payload lists:
0 : SQL Injections
1 : XSS
2 : Command Injection
3 : Format String
4 : XXE
5 : String Fuzzing
6 : SSI Injection
7 : LFI / Directory Traversal
Tool to generate Malformed QRCodes for fuzzing QRCode parsers/reader
optional arguments:
-h, --help show this help message and exit
Options for QRGen:
--list {0,1,2,3,4,5,6,7}, -l {0,1,2,3,4,5,6,7}
Set wordlist to use
--wordlist WORDLIST, -w WORDLIST
Use a custom wordlist
Pay attention everywhere, even in the dumbest spot
- Type python3 qrgen.py –list 1
root@kali:~/Downloads/QRGen# python3 qrgen.py --list 1
e88 88e 888 88e e88'Y88
d888 888b 888 888D d888 'Y ,e e, 888 8e
C8888 8888D 888 88" C8888 eeee d88 88b 888 88b
Y888 888P 888 b, Y888 888P 888 , 888 888
"88 88" 888 88b, "88 88" "YeeP" 888 888
b
8b, QRGen ~ v0.1 ~ by h0nusPayload path exist, continuing…
Path already cleared or deleted..
Generated 113 payloads!
Opening last generated payload…
Thanks for using QRGen, made by H0nus..
root@kali:~/Downloads/QRGen#

- Above query has generated malformed QRL code. This qrl code can be used to handle QRL code data.
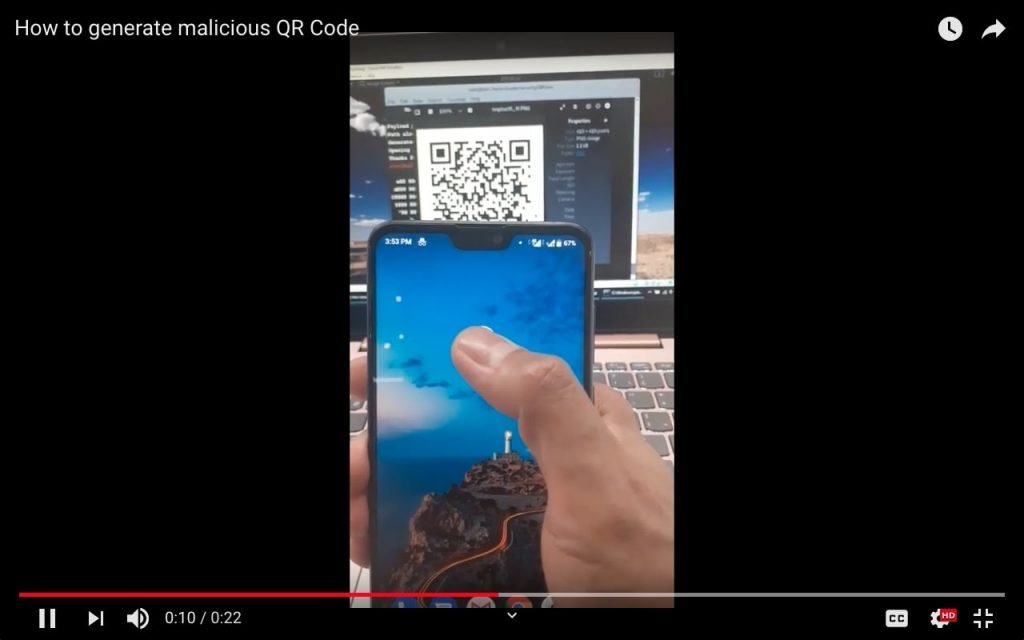
- We can use any QR reading app in mobile to test malicious QR code, as shown below in video:
- We can also read QR code using an online qrl code reader.
https://webqr.com/index.html is used to decrypt qrl code. - We found XSS code in the QRL code.
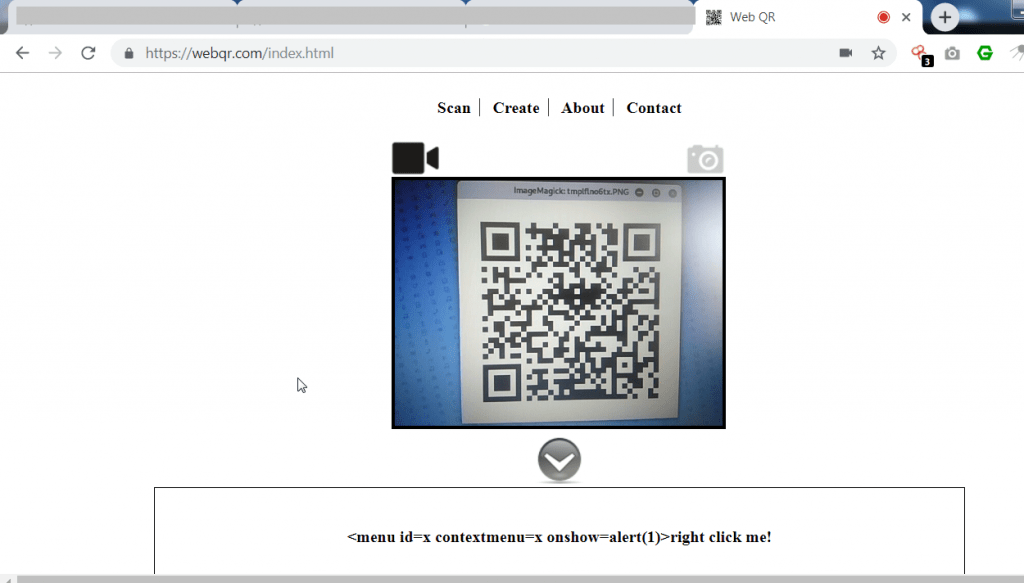
- Above code relates cross site scripting attacks of showing an alert when user tries clicks with right button of mouse it will show an alert message.
- You can create more malform QRL codes with other payloads. Qrlgen uses pre-stored images to generate malformed QRL code.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.