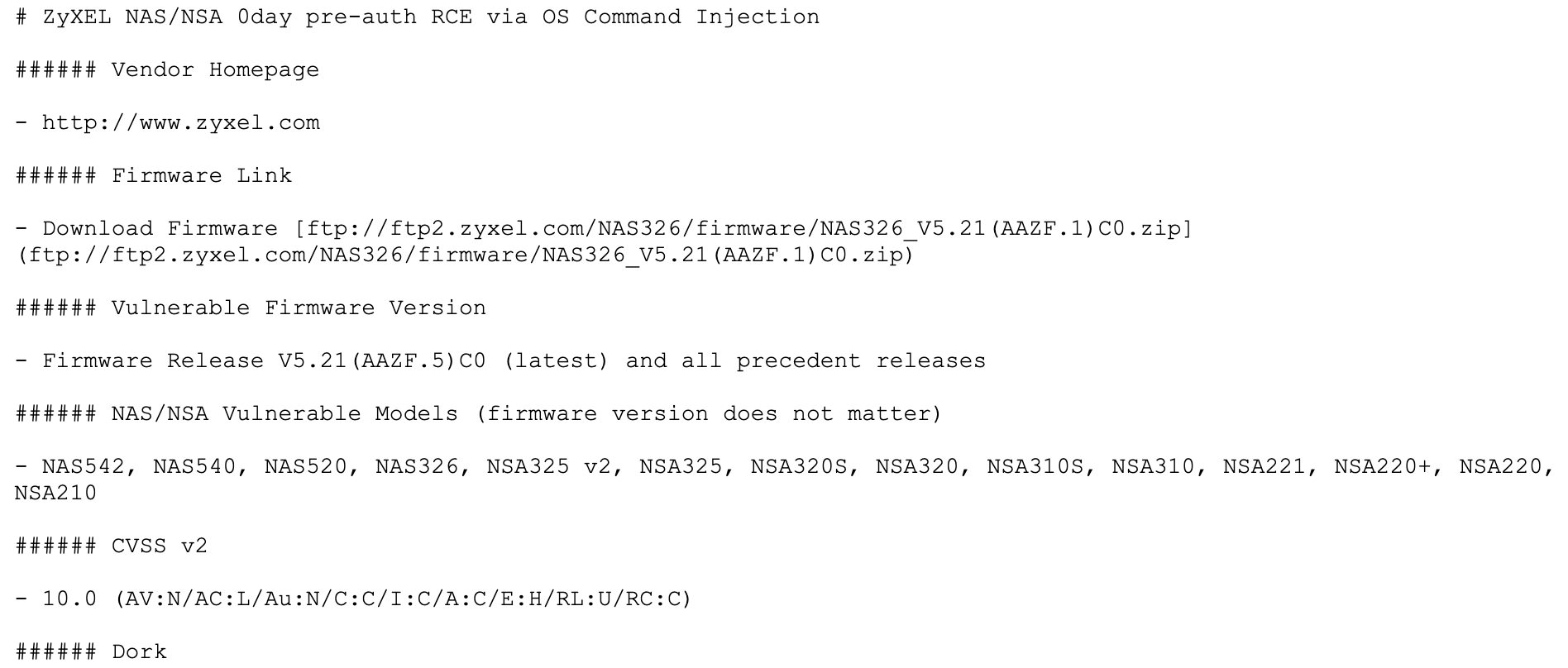
Zyxel, a network hardware manufacturer, has just released an update to fix a critical vulnerability in multiple network attached storage (NAS) devices that would allow you to take remote control of affected devices. The flaw was reported by network security specialists from KrebsOnSecurity, who claim that an exploit to abuse this flaw was for sale on an illegal hacking forum.
The affected Taiwan-based firm is dedicated to the manufacture of network devices such as WiFi, NAS products and hardware firewalls. While these kinds of vulnerabilities are a problem for the Internet of Things (IoT) device industry in general, this case is particularly troubling because threat actors could abuse this flaw to deploy ransomware on a large scale.
When the flaw was reported to Zyxel, a snippet of the code for exploitation was leaked, allowing a hacker to remotely compromise a wide variety of Zyxel NAS products without the need for interaction from affected device administrators.
SOURCE: KerbsOnSecurity
According to network security specialists, the exploit vendor, under the pseudonym “500mhz”, is a hacker recognized in various forums frequented by cybercriminals and specializes in selling zero-day exploits, highly coveted on the hacking black market.
Although the manufacturer initially did not respond to the vulnerability report, a Zyxel representative eventually issued a statement acknowledging the existence of the zero-day vulnerability, listing products vulnerable to exploitation. Vulnerable devices include NAS542, NAS540, NAS520, NAS326, NSA325 v2, NSA325, NSA320S, NSA320, NSA310S, NSA310, NSA221, and more. Even though the firm works to develop a fix, multiple vulnerable devices have stopped receiving support, so they won’t be able to be patched. The company only advised the managers of the products without support not to expose them on the public Internet, as mentioned by the network security specialists.
The International Institute of Cyber Security (IICS) mentions that, due to the triviality of exploiting this flaw, a threat actor could compromise an affected device by simply injecting two characters into the username field of the web control interface of these devices, plus it is highly likely that the vulnerability is present in other Zyxel developments.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











