Participants and instructors of information security training launched a software tool designed to bypass deep packet inspection (DPI). SymTCP is an open source tool for detecting subtle discrepancies between two TCP implementations.
On their official GitHub page, SymTCP developers mention that this tool can be used to find the differences between a server and the DPI, exploiting this information to bypass this deep packet inspection process.
According to the participants of the information security training, this inspection can be of great help in preventing anomalous behaviors and some variants of cyberattack, such as buffer overflow or Man-inThe-Middle (MiTM) attacks, mainly in business environments. In addition, this activity can also be applied for monitoring and configuring censorship blocks at Internet service provider (ISP) level.
The instructors of this information security training, taught in the University Of California’s Computer Science Department, also published a PDF demonstrating how to bypass these DPI mechanisms, regardless of their application in the target system.
The report mentions that these DPI systems employ simplified machine states of network stacks that are not exact copies of the final hosts; users can abuse these discrepancies by fragmenting or manipulating packages.
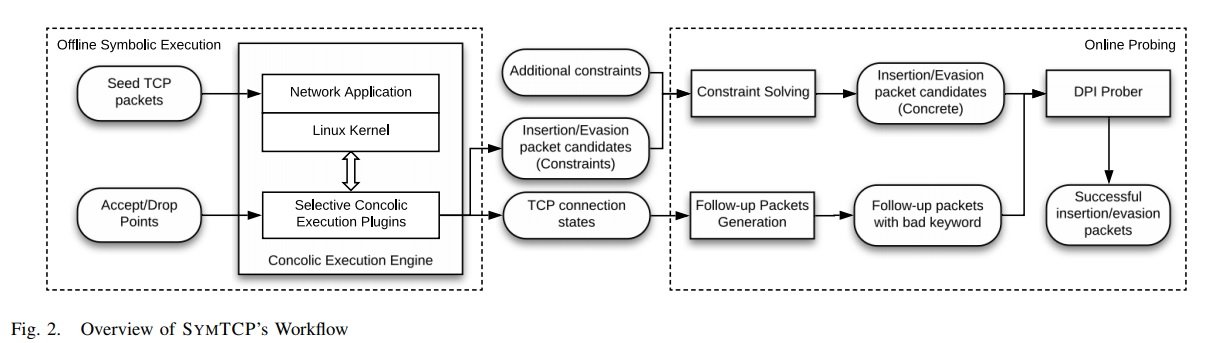
The tool uses “symbolic execution” in the TCP implementation of a server. As a result, execution paths labeled as ‘accept’ or ‘discard’ are collected in packet inspection. The DPI system is then verified against the generated packet streams to determine which ones are processed in the same way by the DPI process and the server, only if there are any.
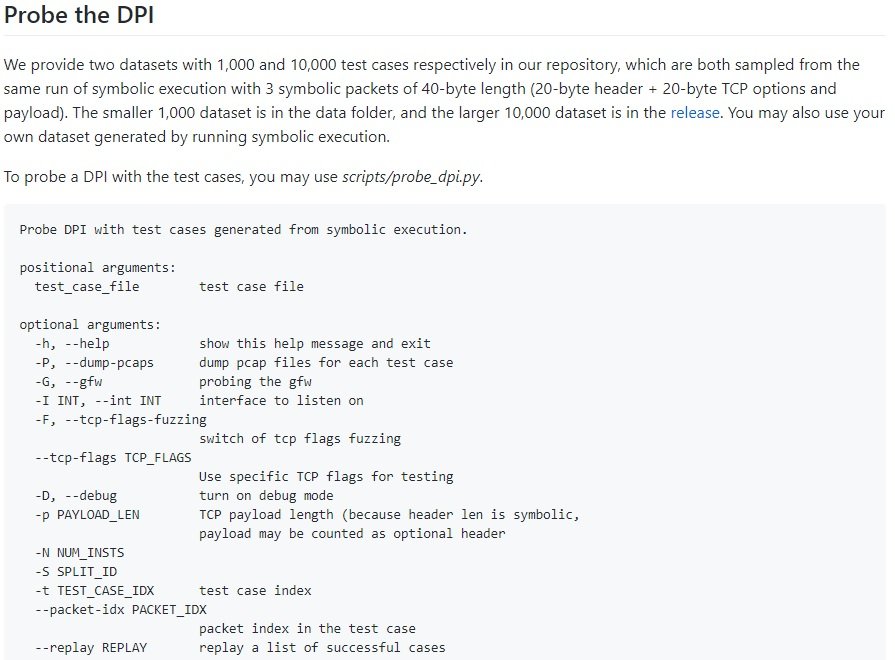
In case of discrepancies, SymTCP can create packages capable of reaching central elements in the code responsible for accepting or discarding requests, sending the middlebox DPI checks. According to the developers, “the automatically identified packets are fed by the middlebox DPI to determine if a discrepancy is introduced and the middlebox can be circumvented”.
According to the International Institute of Cyber Security (IICS) methods revealed above require the manual execution of malicious packages, thus increasing the workload and level of knowledge and skills. Moreover, this project automates the process effectively, minimizing the workload for researchers.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











