Recently Gianluca Pacchiella, researcher and specialist of a cyber security course published a blog post referring to CVE-2020-9544, a zero-day vulnerability involving the D-Link router DSL-2640B. “I did a security assessment on my old router, as I switched Internet service providers, so I installed a new one,” Pacchiella says.
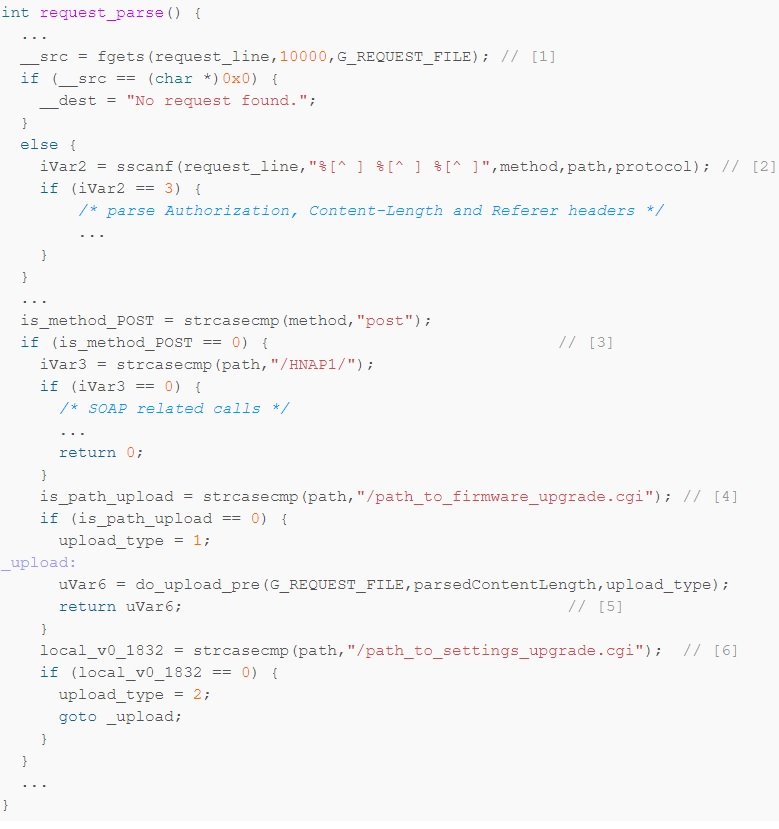
In a very short way, the expert mentions how he detected the security issue, in addition to making some modifications to the device code: “I started by removing all code that is not strictly necessary; in the second line, for example, I extracted method, path and protocol“, mentions the cyber security course specialist.
After parsing a couple of possible headers, the code checks whether the request is a POST and, if the path corresponds to a specific string, loads the firmware and the function returns; the same applies for updating router settings.
According to the cyber security course specialist, this is a significant security threat, as a threat actor with access to the same subnet could access the vulnerable device’s management web interface and install its own version of the firmware without major setbacks. Pacchiella claims that it decided to disclose the vulnerability for any D-Link router user to access this information, as the risk of exploitation is really high.
The researcher adds that he sent his report to the company, although he has not received any response. D-Link’s lack of response is worrying, as the potential exploitation of this vulnerability is trivial. In addition, Pacchiella states that correcting the flaw would be a relatively simple process, indicating that the company simply has not wanted to act.
This is not the first time that D-Link equipment users have pointed to company negligence, so multiple members of the cybersecurity community have recommended stopping using their products.
For more information on recently encountered security flaws, exploits, cyberattacks, and malware analysis, you can visit the official website of the International Institute of Cyber Security (IICS), as well as the official sites of tech companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











