What is Windows Power Shell?
Power Shell is a command-line shell and scripting language. The power shell is built in .Net framework. All system administrators use Windows power shell. We can use this power shell in windows, Mac and Linux (pwsh) operating systems. It will allow us to access the data stores using a cmdlet.
What is cmdlet?
Cmdlet is used to perform an operation in power shell like (Get, Add, Set, Update). In power shell there are 200 cmdlets.
What is RedRabbit Tool?
RedRabbit tools is used to collect the target information and can be used by #RedTeam to conduct ethical hacking. In this we have different types of options like (Quick Recon, Scan Subnet, Clipboard Logger, Network Scanner, DNS Resolver, Brute Force ZIP, Brute WinRM, Test Extraction Connection and show Local Firewall Deny Rules) and also we have OSINT (Open source investigation) options in this are (find subdomains, Daily PasteBin, Scan Azure Resource and Scan Socials for Usernames).

Installation of RedRabbit
- Directly download the RedRabbit zip file in your windows machine and extract the file.
- Use this link to download the RedRabbit zip file. https://github.com/securethelogs/RedRabbit/archive/master.zip.
- First time, when we ran this tool. We got an error that “execution policy is restricted“.
- To resolve this issue, we opened windows PowerShell as administrator and executed this command Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope LocalMachine
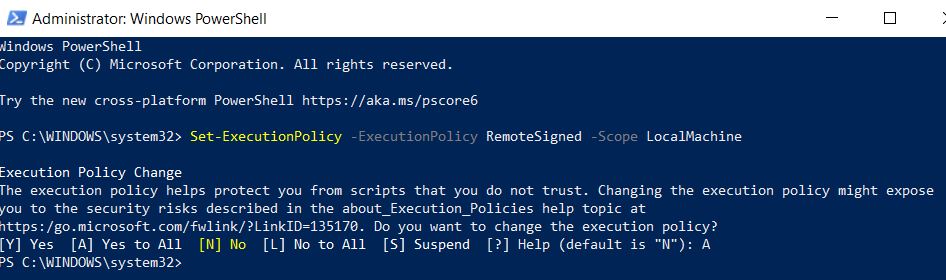
- Now select the option [A] Yes to All
- Change the directory using cd RedRabbit-master command
- Now run the tool .\redrabbit.ps1
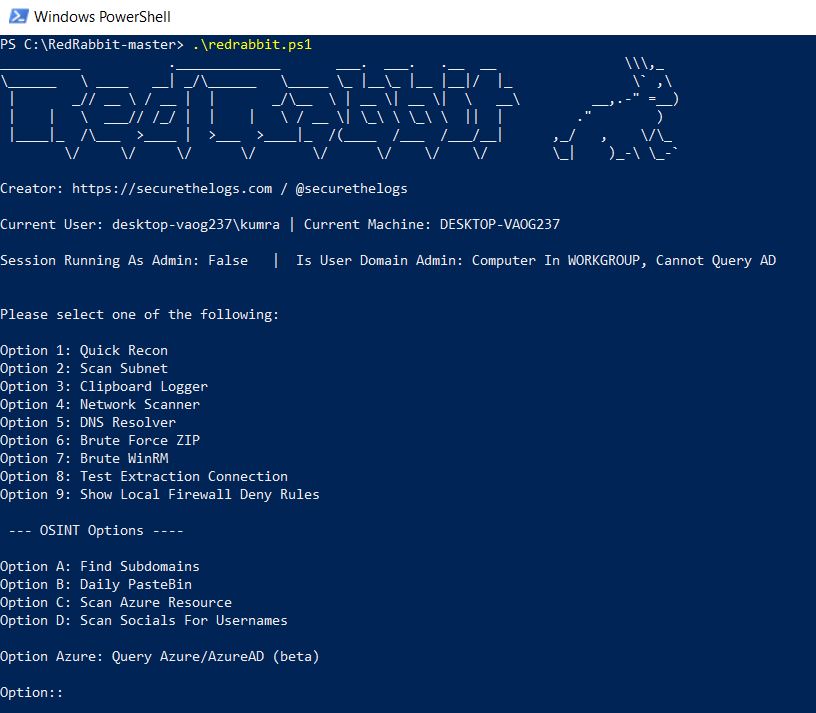
Executing Redrabbit Tool
- In RedRabbit we can see different types of options. In this, we will show you some options.
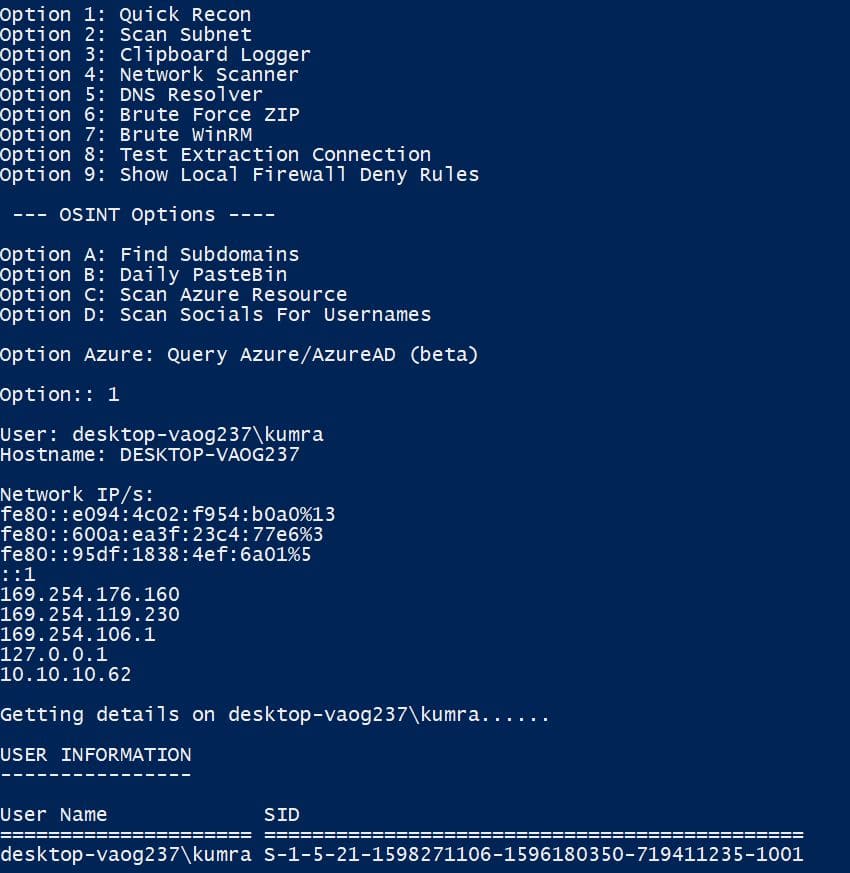
Quick Recon
- In Quick Recon will display complete details about your system like (User/Host Name, Network Details, User information, Privileges Information, Local admin Information and Members, Local User Information, Program information (Files), Internet Access test and complete Firewall Information).
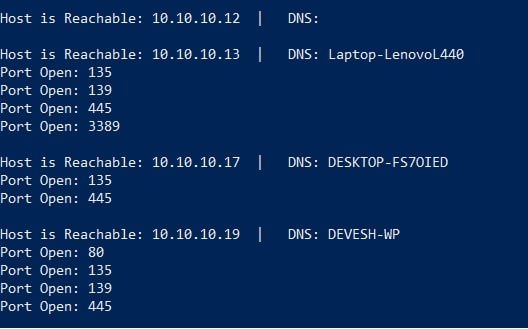
Scan Subnet
This tool scans all IP’s which are connected to the LAN (Local Area Network) and display open ports of each and every IP.
Clipboard logger
- This is very important option and the concept behind it can also be used by malware writers to copy content of clipboard like password, Credit card number, CVV and others things of the target.
- This tool copies each and every thing that is copied to clipboard. Let’s see the execution steps:
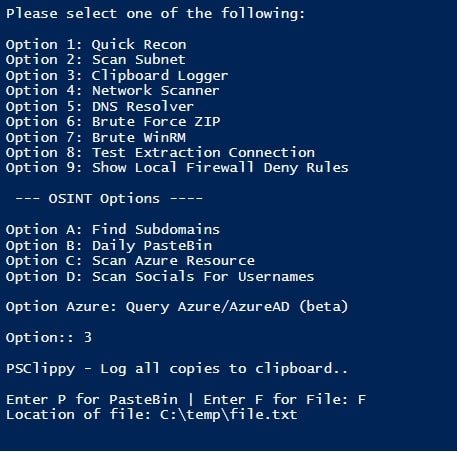
- Select option 3, it will ask you to choose the option P (Pastebin) or F (File). Enter the Letter “F”
- Now, it asks you to enter the location of file. Here we created a folder called temp in C: Drive and created a text file named file.txt. Complete path of file is c:\temp\file.txt
- Enter C:\temp\file.txt in the location of the file path.
- Now go to google and search for sample credit card numbers, we will take a sample credit card number and copy it using Crtl + C and check whether we have captured the content of clipboard to a file or not.
- After copying credit card number. Open the C:\temp folder, file.txt will have all the clipboard data.
- Now lets open the “file.txt” file. To check the information is captured or not as shown below:
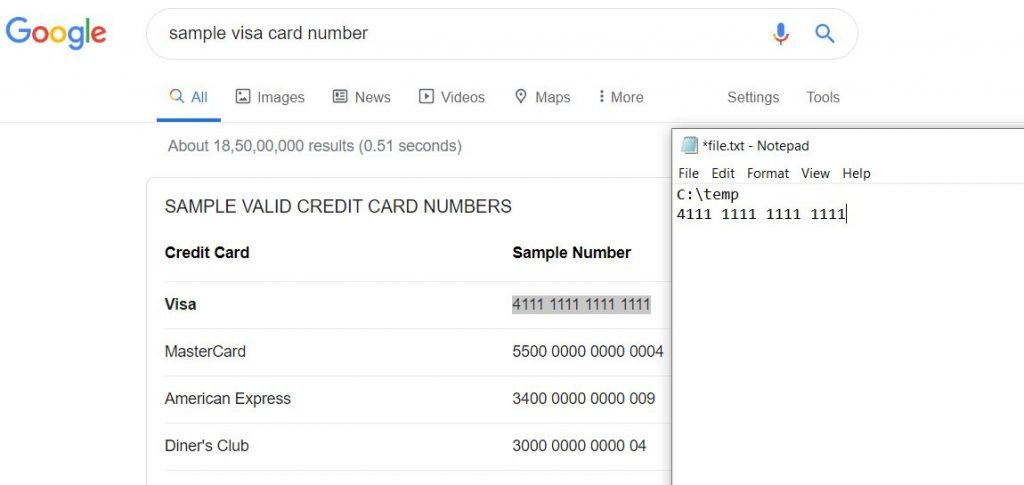
- Yes, we can see the information, which we have captured .
- It is very dangers tool, because if this tool installed in your target system. Attacker can easily capture all the clipboard details of the target.
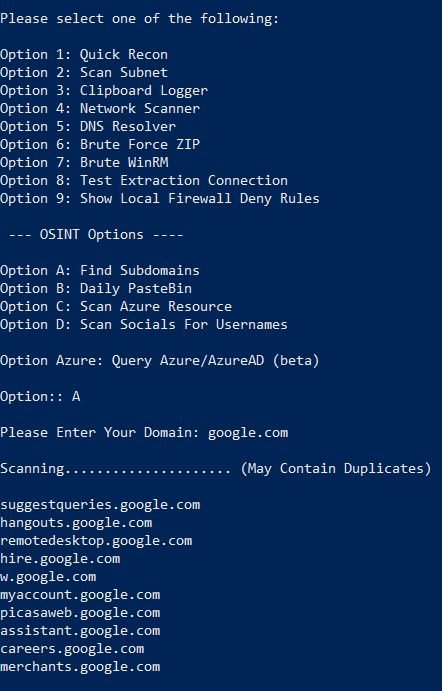
OSINT (open source investigation)
- Select an option “A”. This will capture all the sub domains of the target domain.
Conclusion
We can use this tool for the first stage of penetration testing. To capture some unique information about the target.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











