Introduction
Finding target on internet for penetration testing involves searching internet using google or using Google Hacking/Dorking. There are google hacking queries available on internet, according to ethical hacking researcher of International Institute of Cyber Security it is the main source of passive attacks on internet. This whole process of finding target on internet using GHDB is automated using python based framework named as Katana framework.
This tool can be used in open penetration testing. Katana framework tool is completely built on python language. In this tool, we have five different modules like Google Hacking Database, SCADA, TOR, Proxy and, Bitly. All these modules collect different types of sensitive information.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel version: 5.2.0
Installation Steps
- Use command to clone the file git clone https://github.com/adnane-X-tebbaa/Katana.
root@kali:/home/iicybersecurity# git clone https://github.com/adnane-X-tebbaa/Katana Cloning into 'Katana'... remote: Enumerating objects: 109, done. remote: Counting objects: 100% (109/109), done. remote: Compressing objects: 100% (109/109), done. remote: Total 262 (delta 47), reused 0 (delta 0), pack-reused 153 Receiving objects: 100% (262/262), 2.45 MiB | 180.00 KiB/s, done. Resolving deltas: 100% (93/93), done.
- Use cd command to enter into the directory
- cd Katana/
root@kali:/home/iicybersecurity# cd Katana/ root@kali:/home/iicybersecurity/Katana#
- Now, use command to install the requirements pip3 install -r requirements.txt.
root@kali:/home/iicybersecurity/Katana# pip3 install -r requirments.txt Requirement already satisfied: requests in /usr/local/lib/python3.7/dist-packages (from -r requirments.txt (line 1)) (2.20.0) Collecting proxybroker (from -r requirments.txt (line 2)) Cache entry deserialization failed, entry ignored Downloading https://files.pythonhosted.org/packages/27/bd/7ffee9acbf97ab702f373678a9ac61aefbd59710b1544cf6c6a31d114203/proxybroker-0.3.2-py3-none-any.whl (1.6MB) 100% |████████████████████████████████| 1.6MB 94kB/s Requirement already satisfied: google in /usr/local/lib/python3.7/dist-packages (from -r requirments.txt (line 3)) (2.0.3) Requirement already satisfied: termcolor in /usr/lib/python3/dist-packages (from -r requirments.txt (line 4)) (1.1.0) Collecting txtorcon (from -r requirments.txt (line 5)) Downloading https://files.pythonhosted.org/packages/4e/36/910a6991534847eda30e99a7c363cd2bbe6710fc05a2d54c9abe22507ffe/txtorcon-19.1.0-py2.py3-none-any.whl (341kB) 100% |████████████████████████████████| 348kB 199kB/s Requirement already satisfied: colorama in /usr/local/lib/python3.7/dist-packages (from -r requirments.txt (line 6)) (0.4.1) Requirement already satisfied: bs4 in /usr/local/lib/python3.7/dist-packages (from -r requirments.txt (line 7)) (0.0.1) Collecting StringGenerator (from -r requirments.txt (line 8)) Downloading https://files.pythonhosted.org/packages/55/11/2a8a4497c249a7d19e32bbd9035390a77775cd065ad46ea4b24676da4574/StringGenerator-0.3.3.tar.gz Requirement already satisfied: chardet<3.1.0,>=3.0.2 in /usr/lib/python3/dist-packages (from requests->-r requirments.txt (line 1)) (3.0.4) Requirement already satisfied: urllib3<1.25,>=1.21.1 in /usr/local/lib/python3.7/dist-packages (from requests->-r requirments.txt (line 1)) (1.24.3) Requirement already satisfied: idna<2.8,>=2.5 in /usr/local/lib/python3.7/dist-packages (from requests->-r requirments.txt (line 1)) (2.7) Requirement already satisfied: certifi>=2017.4.17 in /usr/local/lib/python3.7/dist-packages (from requests->-r requirments.txt (line 1)) (2019.9.11) Requirement already satisfied: aiodns>=2.0.0 in /usr/lib/python3/dist-packages (from proxybroker->-r requirments.txt (line 2)) (2.0.0) Collecting attrs==19.1.0 (from proxybroker->-r requirments.txt (line 2)) Downloading https://files.pythonhosted.org/packages/23/96/d828354fa2dbdf216eaa7b7de0db692f12c234f7ef888cc14980ef40d1d2/attrs-19.1.0-py2.py3-none-any.whl Collecting aiohttp>=3.5.4 (from proxybroker->-r requirments.txt (line 2)) ============================================================================================================SNIP================================================================================================================= Downloading https://files.pythonhosted.org/packages/98/3f/e53dea9face4115abfb796f398bf74747a0d294537b12935d1bbf697c11a/multidict-4.7.5-cp37-cp37m-manylinux1_x86_64.whl (149kB) 100% |████████████████████████████████| 153kB 146kB/s Requirement already satisfied: setuptools in /usr/lib/python3/dist-packages (from zope.interface>=3.6.1->txtorcon->-r requirments.txt (line 5)) (41.0.1) Requirement already satisfied: PyHamcrest>=1.9.0 in /usr/local/lib/python3.7/dist-packages (from Twisted[tls]>=15.5.0->txtorcon->-r requirments.txt (line 5)) (2.0.2) Requirement already satisfied: constantly>=15.1 in /usr/local/lib/python3.7/dist-packages (from Twisted[tls]>=15.5.0->txtorcon->-r requirments.txt (line 5)) (15.1.0) Requirement already satisfied: hyperlink>=17.1.1 in /usr/local/lib/python3.7/dist-packages (from Twisted[tls]>=15.5.0->txtorcon->-r requirments.txt (line 5)) (19.0.0) Requirement already satisfied: pyopenssl>=16.0.0; extra == "tls" in /usr/lib/python3/dist-packages (from Twisted[tls]>=15.5.0->txtorcon->-r requirments.txt (line 5)) (19.0.0) Requirement already satisfied: service-identity>=18.1.0; extra == "tls" in /usr/local/lib/python3.7/dist-packages (from Twisted[tls]>=15.5.0->txtorcon->-r requirments.txt (line 5)) (18.1.0) Requirement already satisfied: six in /usr/lib/python3/dist-packages (from automat->txtorcon->-r requirments.txt (line 5)) (1.12.0) Requirement already satisfied: pyasn1 in /usr/local/lib/python3.7/dist-packages (from service-identity>=18.1.0; extra == "tls"->Twisted[tls]>=15.5.0->txtorcon->-r requirments.txt (line 5)) (0.4.7) Requirement already satisfied: pyasn1-modules in /usr/lib/python3/dist-packages (from service-identity>=18.1.0; extra == "tls"->Twisted[tls]>=15.5.0->txtorcon->-r requirments.txt (line 5)) (0.2.1) Building wheels for collected packages: StringGenerator Running setup.py bdist_wheel for StringGenerator ... done Stored in directory: /root/.cache/pip/wheels/63/2d/f9/dd7bf4a6fab18af351ef29aac6418a5989faceefbd809cc661 Successfully built StringGenerator automat 20.2.0 has requirement attrs>=19.2.0, but you'll have attrs 19.1.0 which is incompatible. Installing collected packages: attrs, multidict, yarl, async-timeout, aiohttp, proxybroker, txtorcon, StringGenerator Found existing installation: attrs 19.3.0 Uninstalling attrs-19.3.0: Successfully uninstalled attrs-19.3.0 Successfully installed StringGenerator-0.3.3 aiohttp-3.6.2 async-timeout-3.0.1 attrs-19.1.0 multidict-4.7.5 proxybroker-0.3.2 txtorcon-19.1.0 yarl-1.4.2
- Now, use command python3 katana-ds.py to execute the tool
root@kali:/home/iicybersecurity/Katana# python3 katana-ds.py|,........T_________________________________________________________ |G|o|o|g|l|e|||O________________________________________________________/ R V1.5 |Katana Dork Scanner (Katana-DS) coded by adnane tebbaa please use -h to see help
- Next, use command to find help options python3 katana-ds.py -h.
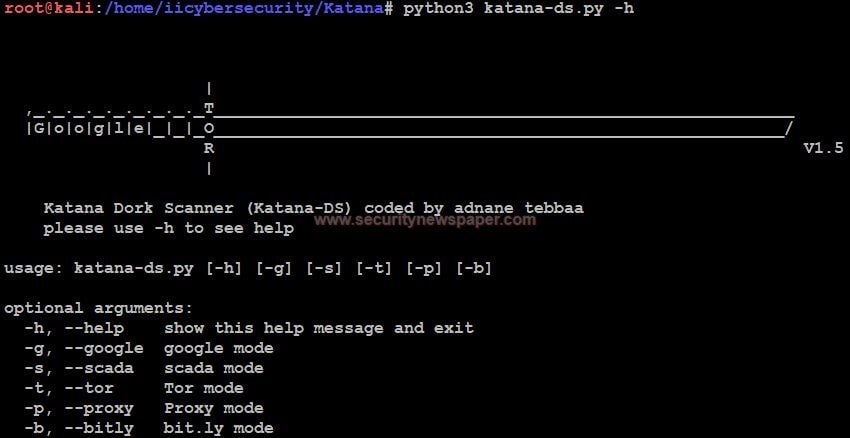
Google mode
In google mode, we have a tool called dork scanner. This tool is used to collect the vulnerable URLs using Google database.
When we use this google mode it asks users to enter DORK and TLD (Top Level Domain)
- Now, enter php?id=1 in the Dork option and enter com in the TLD option.
- We can also search for the required TLD, it is located in tld.txt file in the katana directory.
- After entering this query the dork scanner list out the URLs, which ends with this query
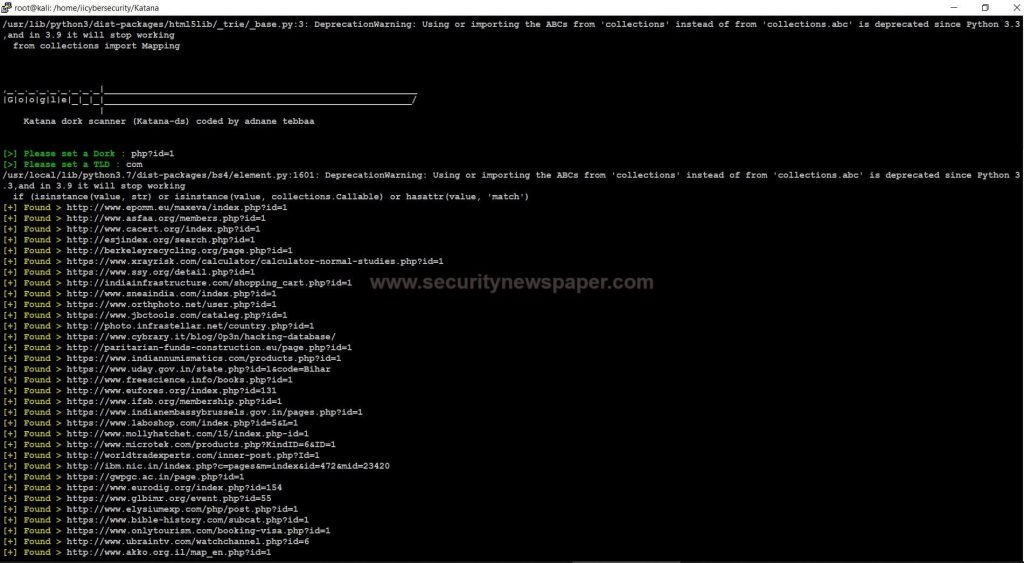
- Here we got the URLs with the entered DORK.
- Now, let’s open any URL and check whether we can find any webpage.
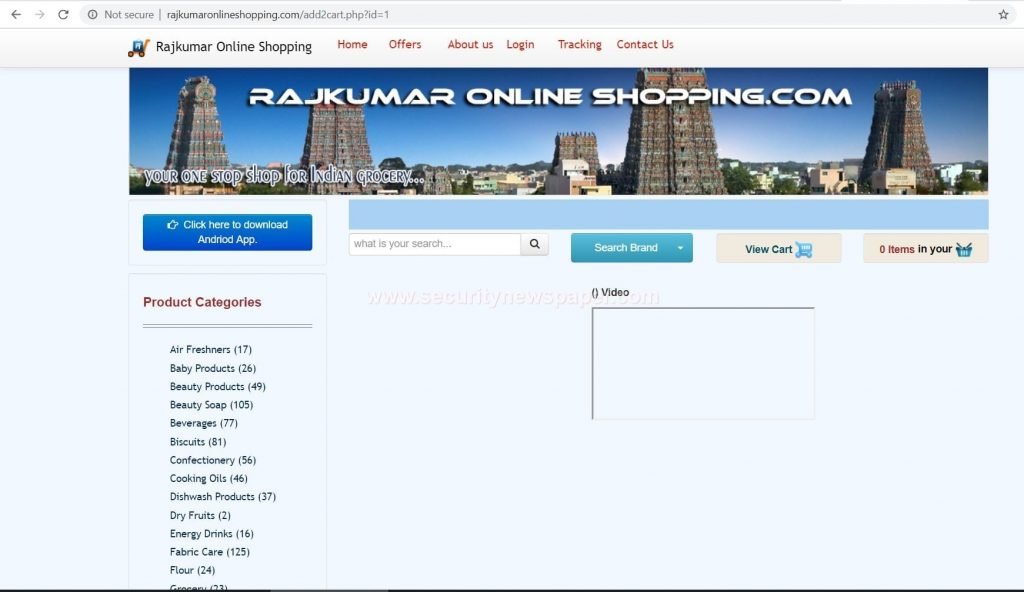
- As an example we found a page with the DORK, which can be used further to do testing.
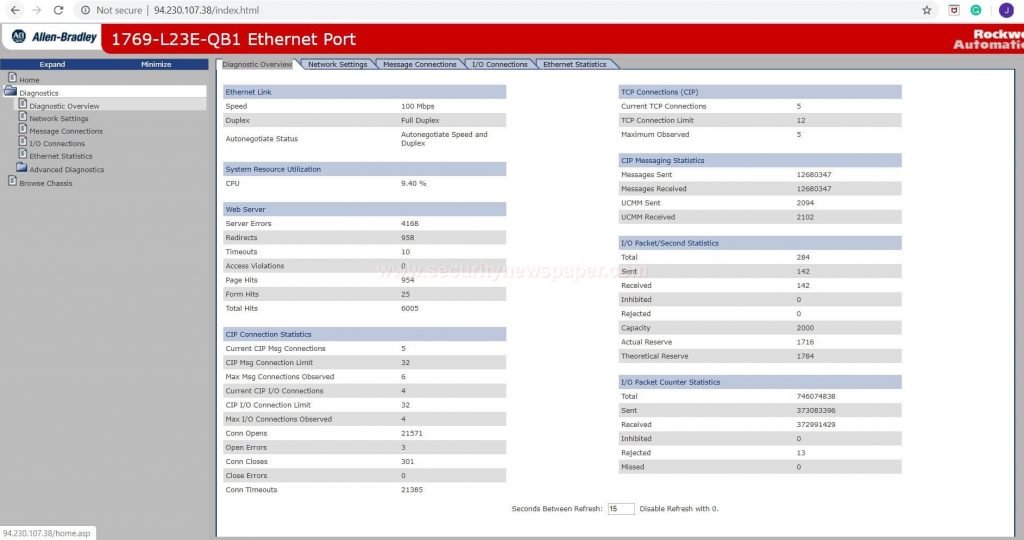
SCADA mode
SCADA mode is a supervisory control and data acquisition. This SCADA mostly used in industries to monitor automated machines.
- In this scada mode we have to enter the TLD. After that it list out the URLs
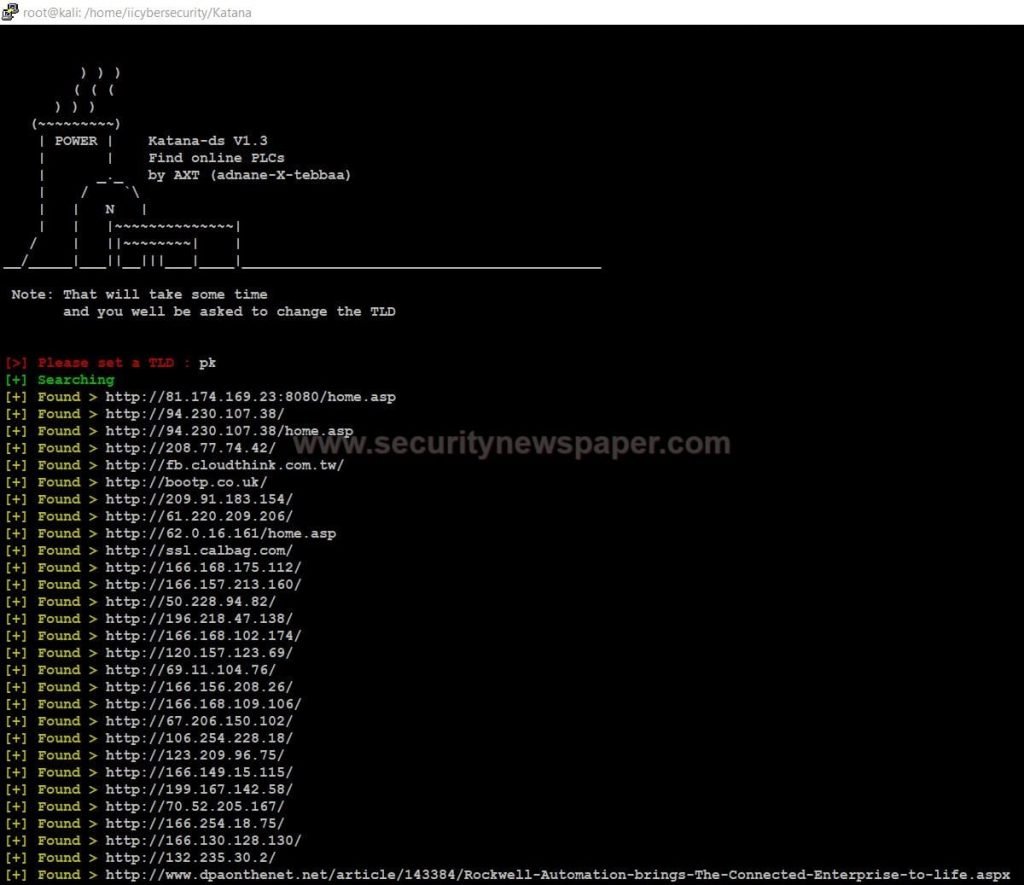
- Here, we got the URLs.
- Now, let’s open any URL from this, to check the web page.
- We found on open device on internet
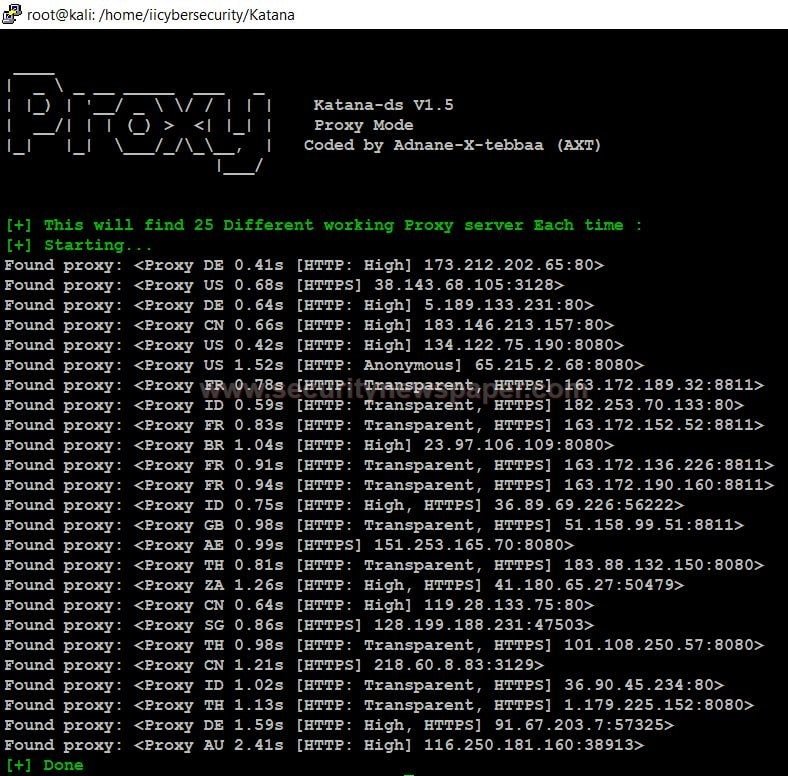
Proxy mode
What is a proxy server?
A proxy server is used to hide our IP address which performing scan.
- In the proxy mode, it will list out the 25 different working proxy.
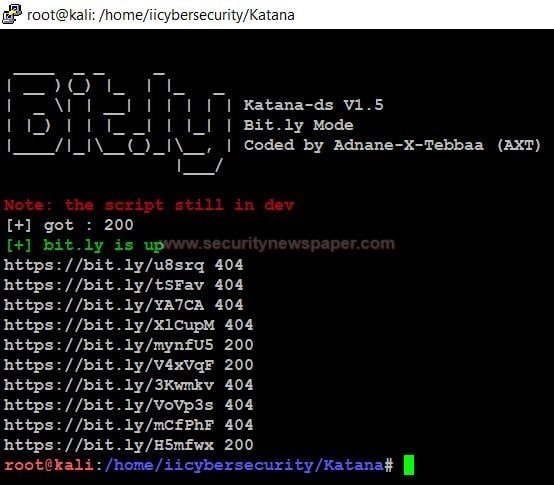
Bitly mode
Bitly is used for URL shorter. When we perform this test. We get 10 bitly links, if we open these links in our browser it may redirect to any web page.
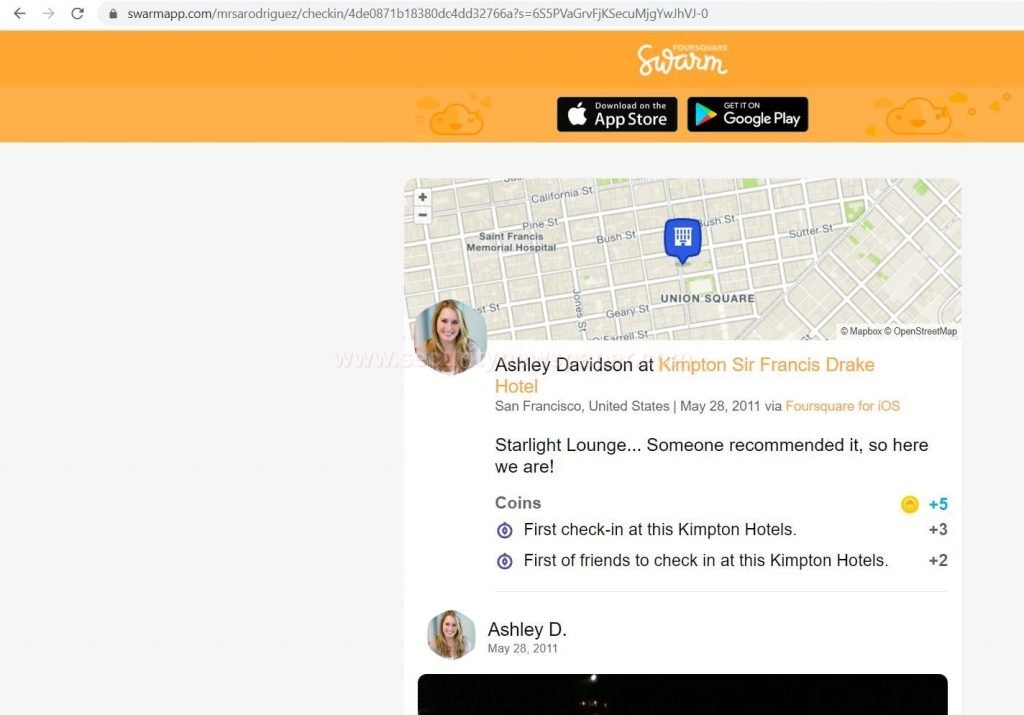
- Now, lets open the URL, which has a code 200. To check whether link redirects to any webpage or not.
Conclusion
This tool automate the complete process of finding the target on internet using GHDB, which can help researcher in doing their public research.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











