Introduction
For hacking any website or web application, information gathering phase about the target is must. Hackers use different tools for collecting unique information about the target. Web killer is another information-gathering tool with nice options to scan the target. In this tool, we have all the option to perform information gathering and this tool is completely built on the python programming language.
Environment
- OS: Ubuntu 18.04.4, 64 bit
- Kernel version: 5.3.0-45-generic
Installation Steps
- Use this command to clone the file. git clone https://github.com/ultrasecurity/webkiller
root@ubuntu-VirtualBox:/home/iicybersecurity# git clone https://github.com/ultrasecurity/webkiller Cloning into 'webkiller'… remote: Enumerating objects: 3, done. remote: Counting objects: 100% (3/3), done. remote: Compressing objects: 100% (3/3), done. remote: Total 160 (delta 0), reused 0 (delta 0), pack-reused 157 Receiving objects: 100% (160/160), 97.63 KiB | 254.00 KiB/s, done. Resolving deltas: 100% (56/56), done.
- Use the cd command to enter into the webkiller directory.
- cd webkiller/
root@ubuntu-VirtualBox:/home/iicybersecurity# cd webkiller/ root@ubuntu-VirtualBox:/home/iicybersecurity/webkiller#
- Next, use this command to install the requirements.txt
- pip3 install -r requirement.txt
- Now, use this command to launch the tool
- python3 webkiller.py
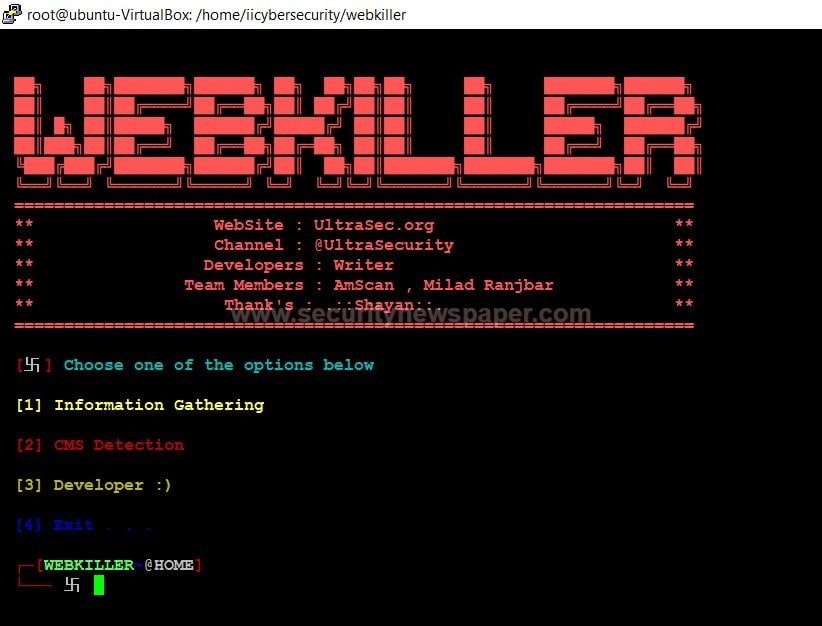
- Here we see the 3 options, Information gathering, CMS Detection, and Developer. Choose the required option.
Information Gathering
Information Gathering is just like collecting information about the target it can be a web application or a network, which are publicly available on the internet.
- In the information gathering, we have 14 options.
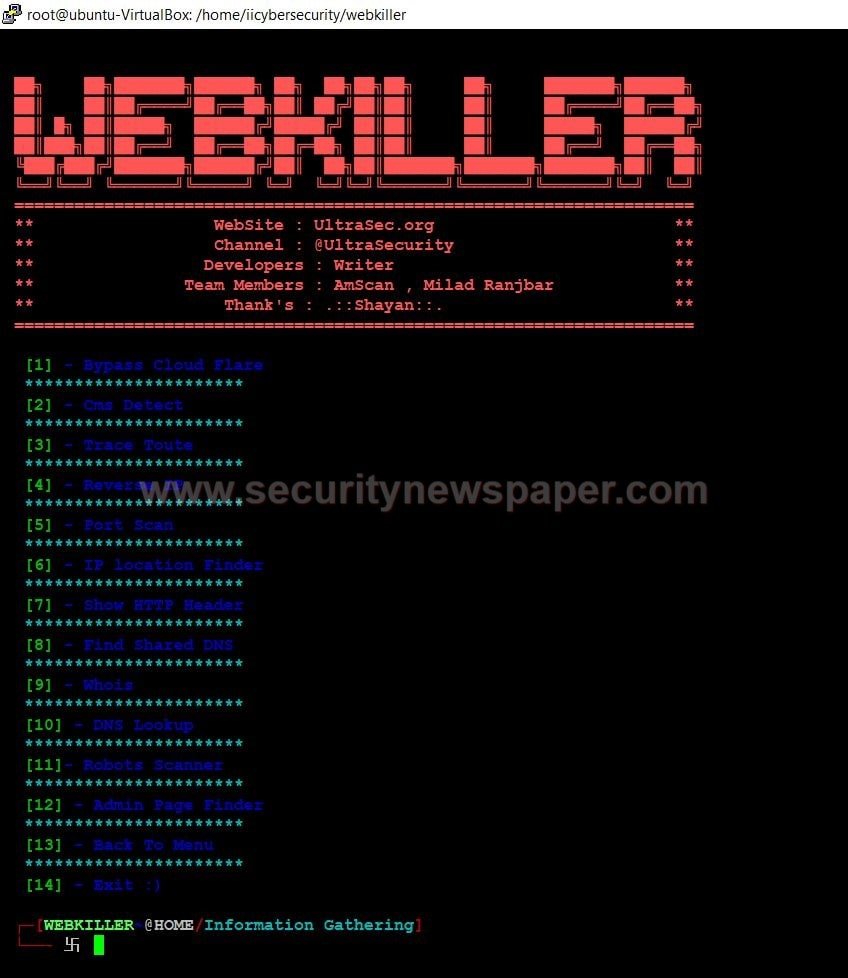
- Now, we will show some unique option.
Bypass Cloud Flare
Cloud Flare acts as a reverse proxy between the website and website users. These are the countries where cloud Flare services are available.
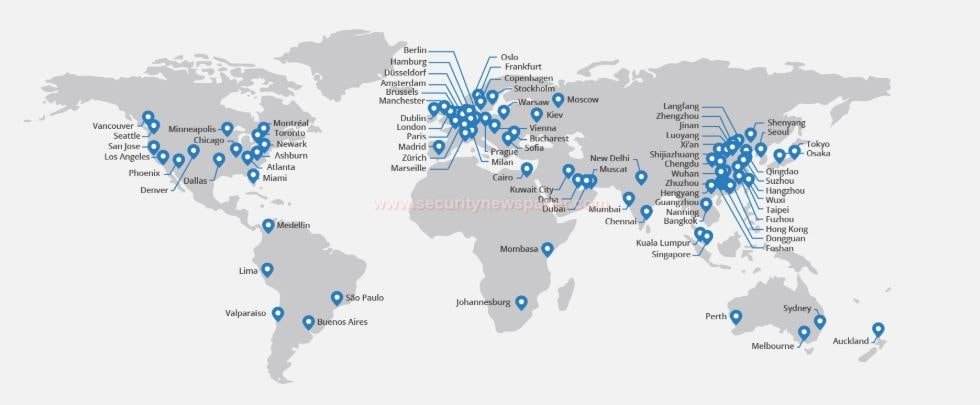
So, most of the websites are using cloud flare services.
- Choose option 1, select cloud flare and enter the domain name.
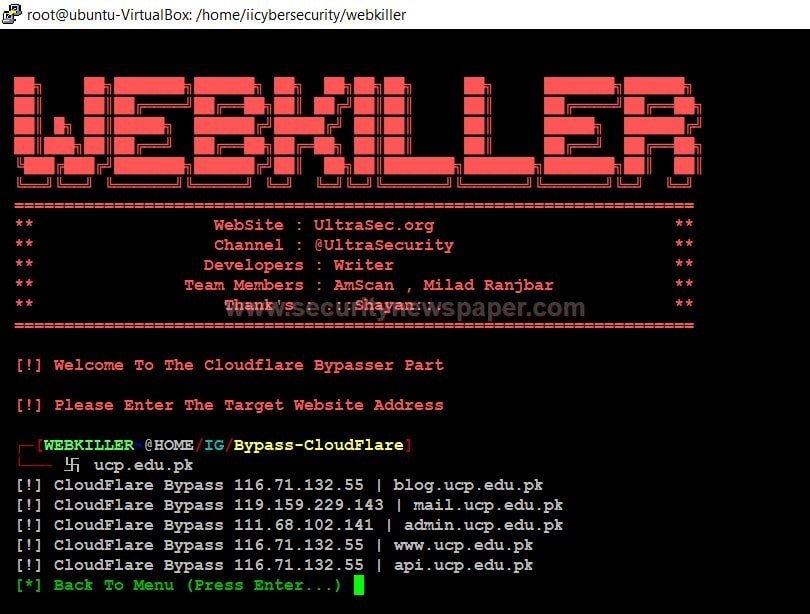
- Here we got the URLs about the targeted website.
- Now, open the URL in our browser. To check whether the URL takes us working.
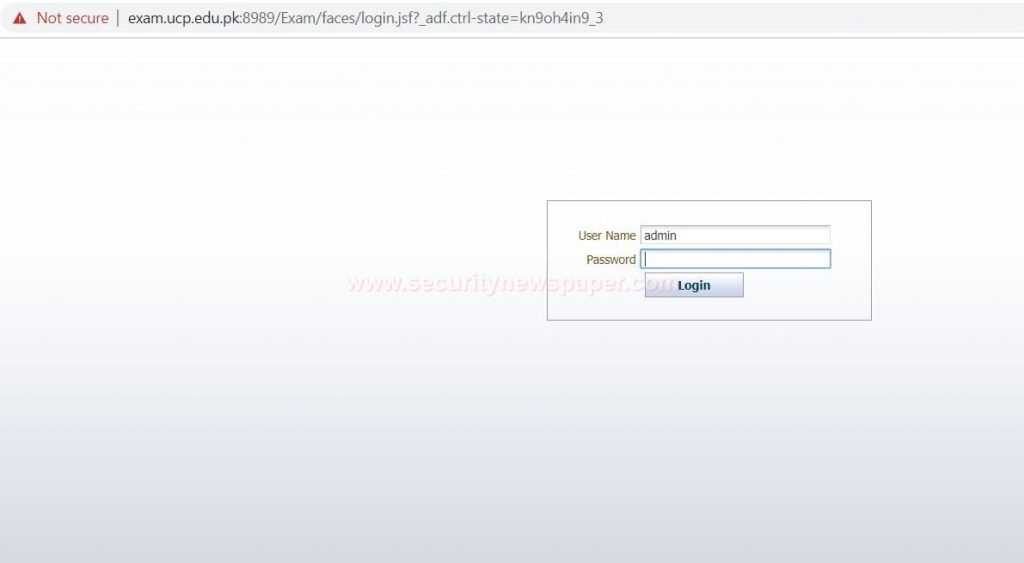
- Here, we got the admin’s page of website.
Port Scan
The port scan is to check open ports in a domain/IP.
- Choose option 5, to start the port scan.
- For scanning the domain/IP, this webkiller is using the Nmap tool.
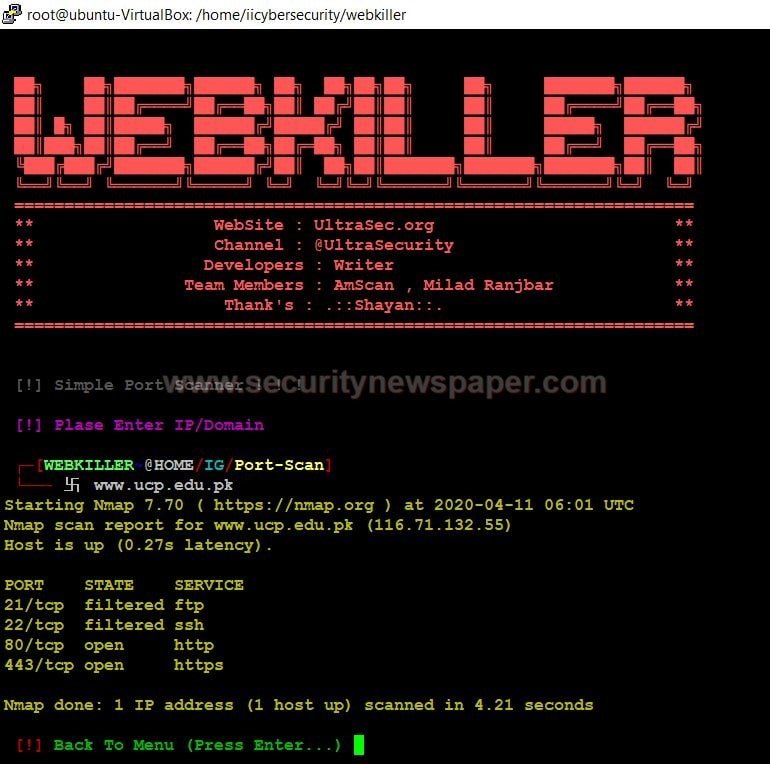
- Here, we see the ports, state and service on the target domain.
Trace Toute
Trace Toute is a tool that records the data packet traveling from host computer to destination via the internet.
- Now, choose option 3 for Trace Toute
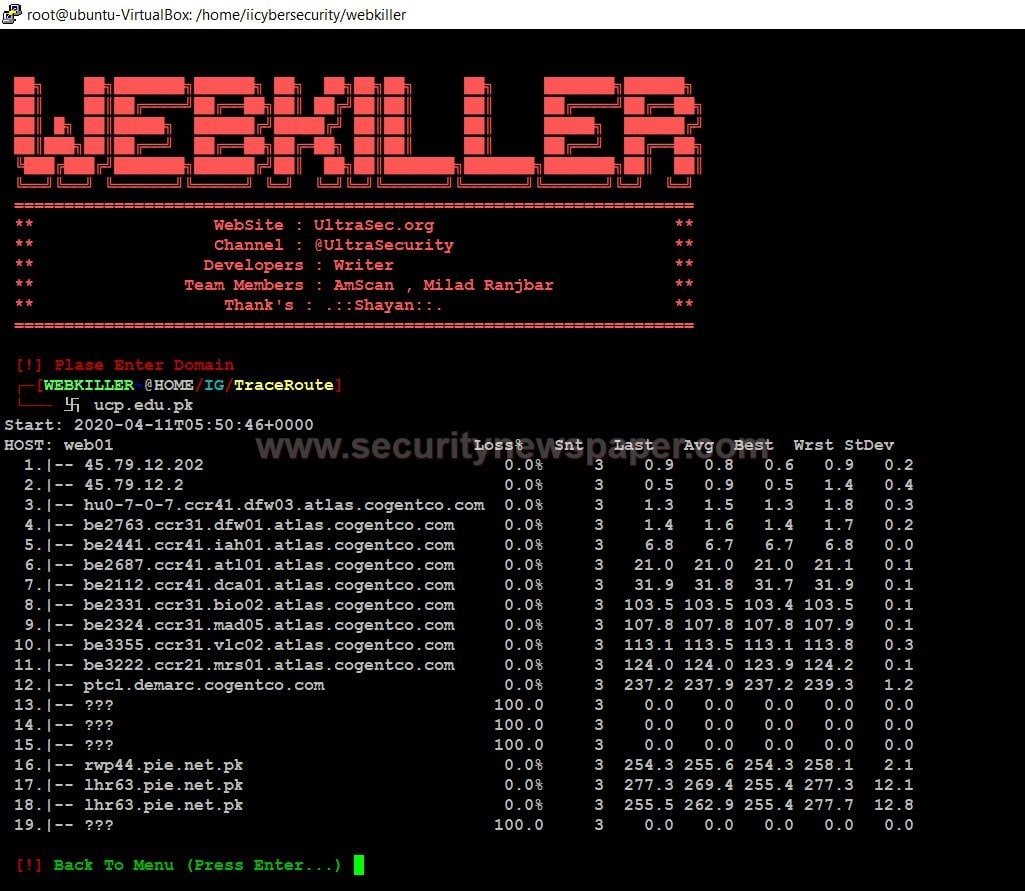
- Here, we see the packets and the average time on each hop.
CMS Detection
In the webkiller we have an option called CMS Detection. The main aim of this is to detect the target website CMS (content management system).
- Choose option 2 and select option 1 for WordPress.
- Select option 1 for plugins
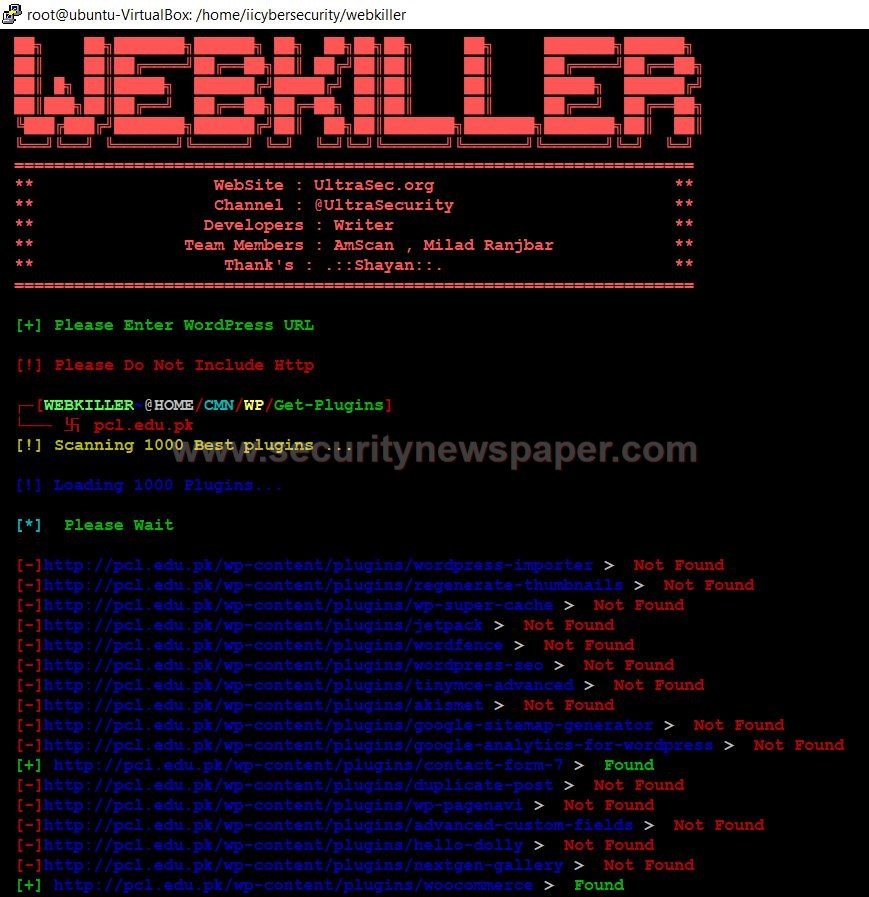
- In the above picture, we can see two URLs. Open this URLs in the browser and let’s check whether we get any information.
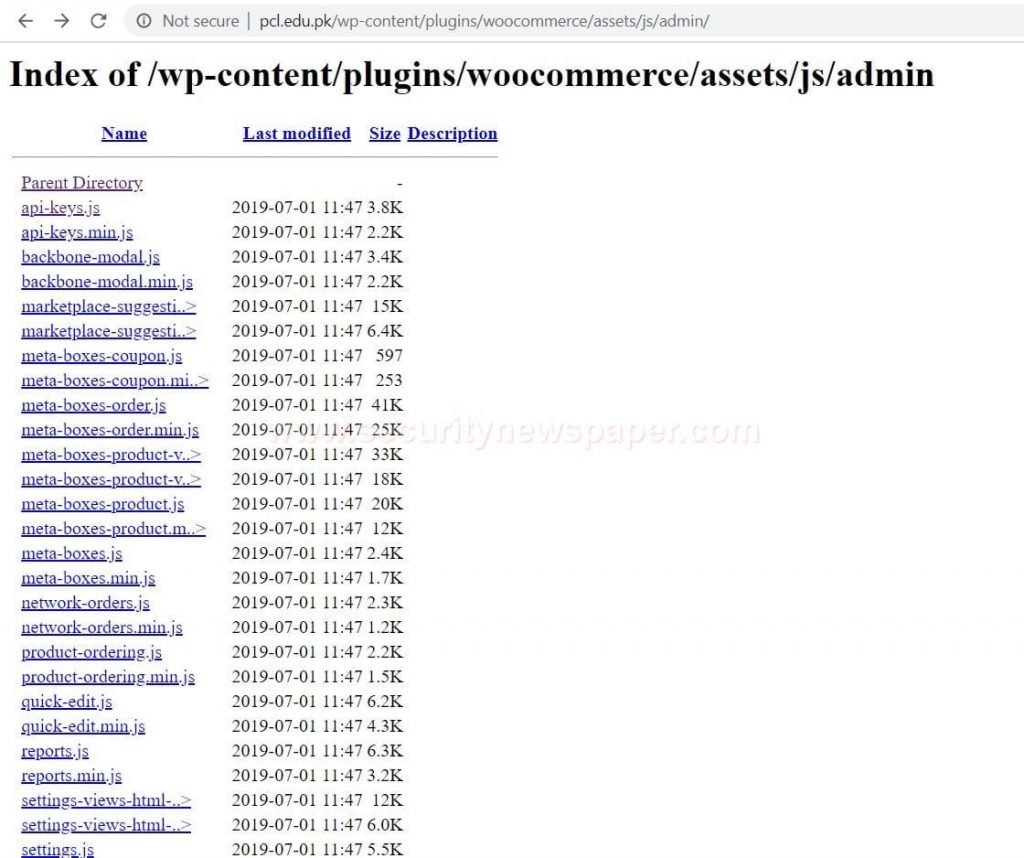
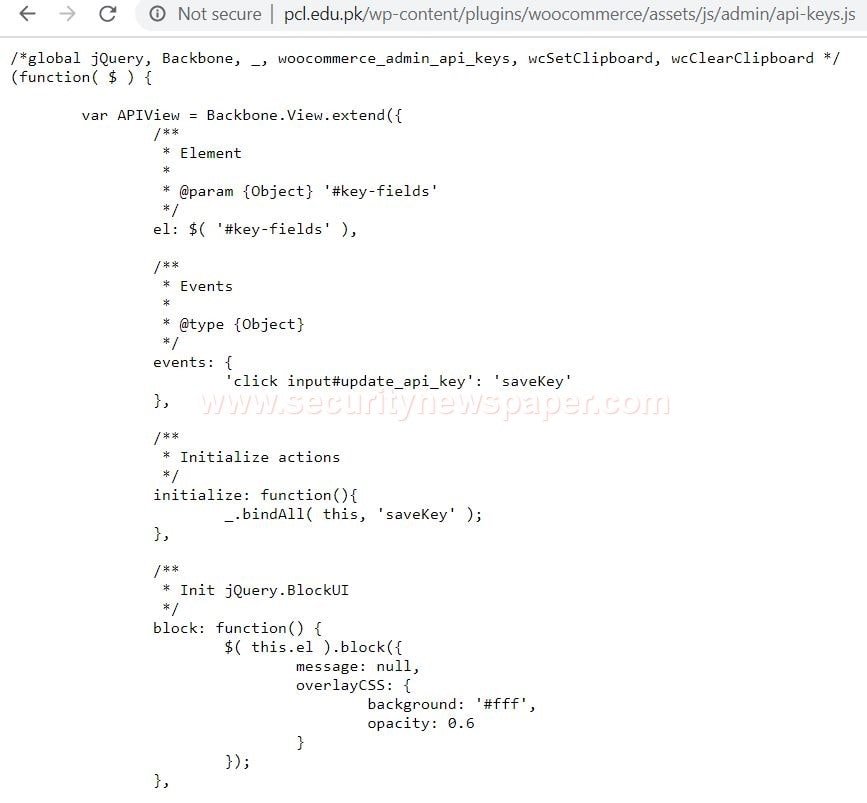
- Here, we can see the admin’s data. Now let me open the API-keys.js and check whether we find any information in these folders.
Conclusion
Information gathering phase is very important phase of doing pentesting, this tool is easy to use and can be used to craft further attacks.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











