The main aim of hacker is to compromise any machine and to steal the confidential information from the system. Most of the Hackers takes precaution while performing illegal activities and always try to hide themselves from being caught. Once the system is compromised hacker always install some backdoor on compromised system to maintain access. Today we will show on how we can check if your linux server is hacked or Not?
Symptoms of a compromised server.
Every hacker leaves some evidences, this is up to the IT Administrator to find out the left behind evidences. If your server is hacked, it will definitely behave one day or other in some or the other manner. There are few things we can quickly run on our linux box to find whether linux system was hacked or not. Follow below steps quickly to audit your linux box:
Check Current Login
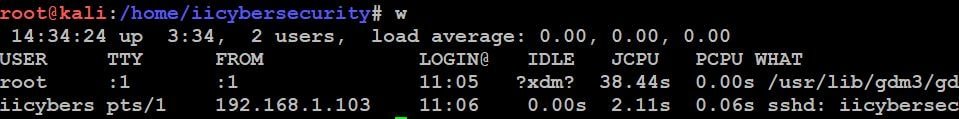
Step 1: First we have to check, who is logged into the server by using this “w” command. This will show the output of login details with the user, IP, and time.
Check Last Login
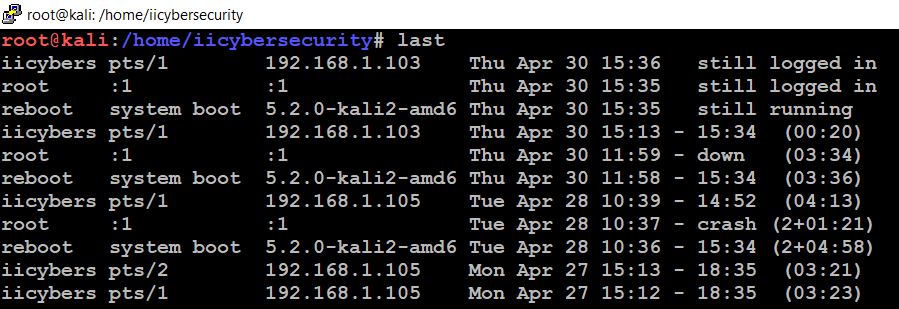
Step 2: Linux servers record the login details with the IP address. To know who logged in to server, use this command “last” that will show us the login details with IP address, time.
Check Command History
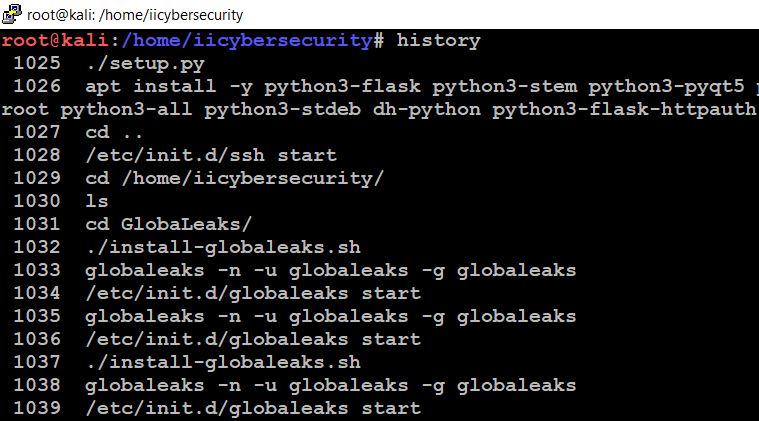
Step 3: Linux stores the commands in history, which we use in the terminal. By issuing history command we can see the list of commands executed by user in the terminal.
Check CPU Processes
Step 4: Most of the hacker run a process to get backdoor to system and this backdoor process might can consume CPU, we can use “top” command to check the list of high processes.
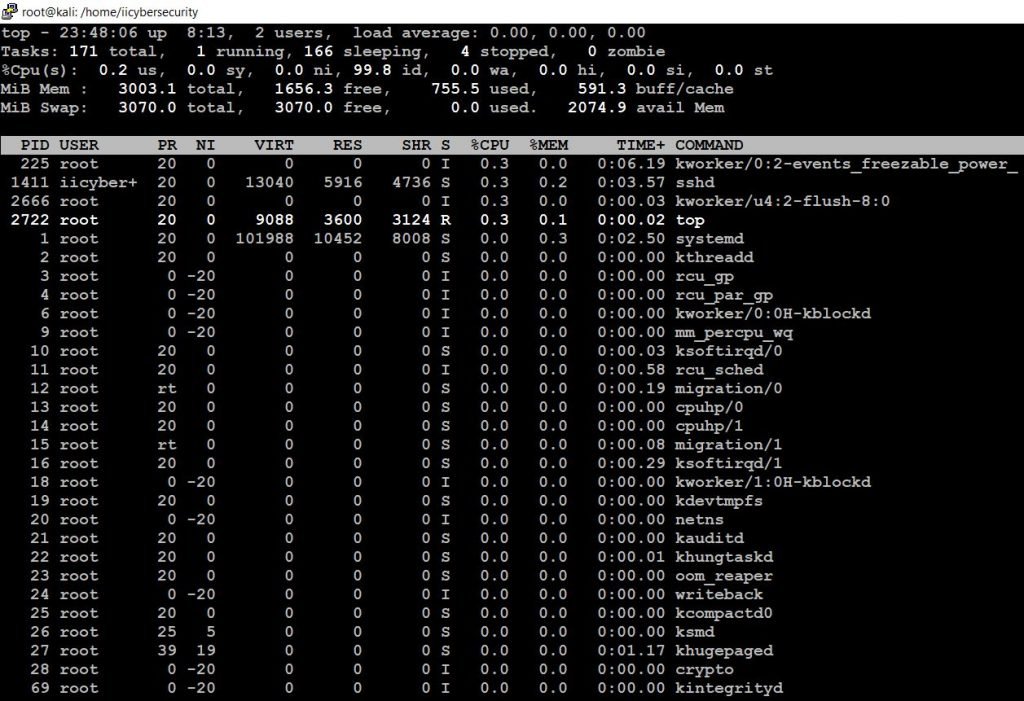
Here, we have to identify the currently running highest process in linux kernel and now we can also use this command “strace”.
Strace is used to trace the system calls and signals. which will interpret and records the system calls made by the process. We use this command for debugging and troubleshooting in linux operating system.
First we have to install this package “apt install strace”. After installing strace we can use this command to debug “strace -d -p <PID Number>”
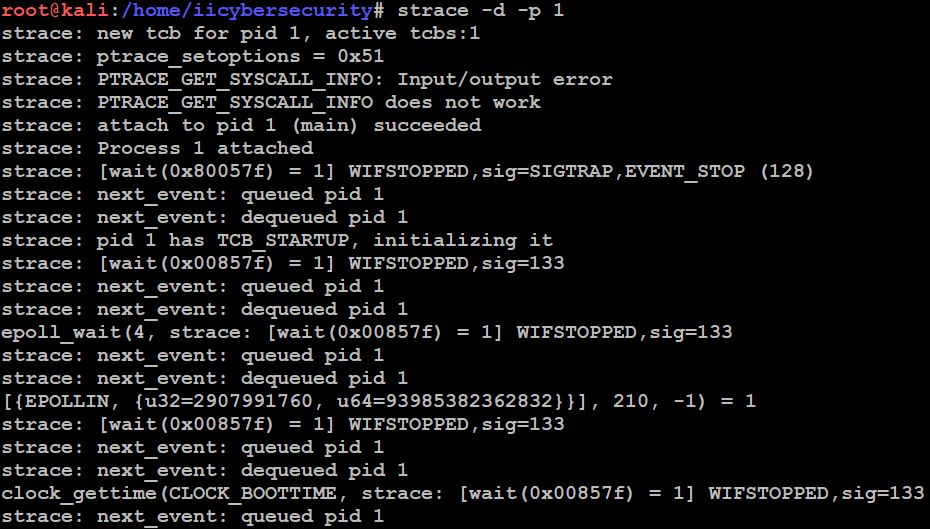
Check System Processes
Step 5: Now we have to check the system processes running. Use this command “ps auxf” to get more information on processes running.
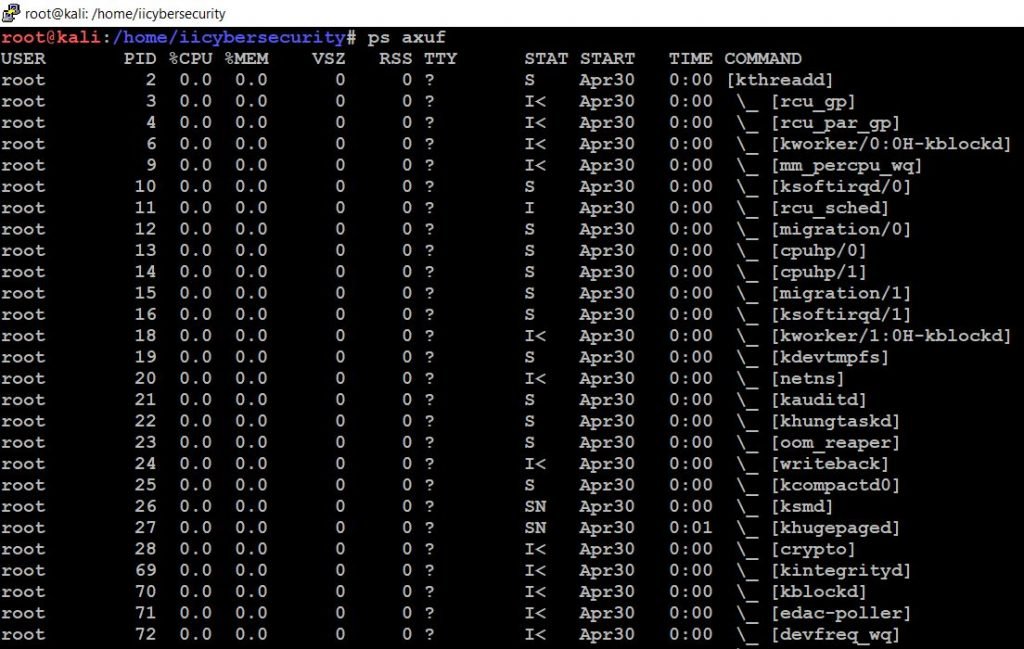
We can kill the process by using this command “kill -9 <PID>”
Check Network Trafiic
Step 6: Now, we have to check the network traffic by using the command “iftop” this will provides us details about the sending and receiving the network data along with the source and destination.
First, we have to install the package by using this command “apt install iftop”. The output will be displayed in this way
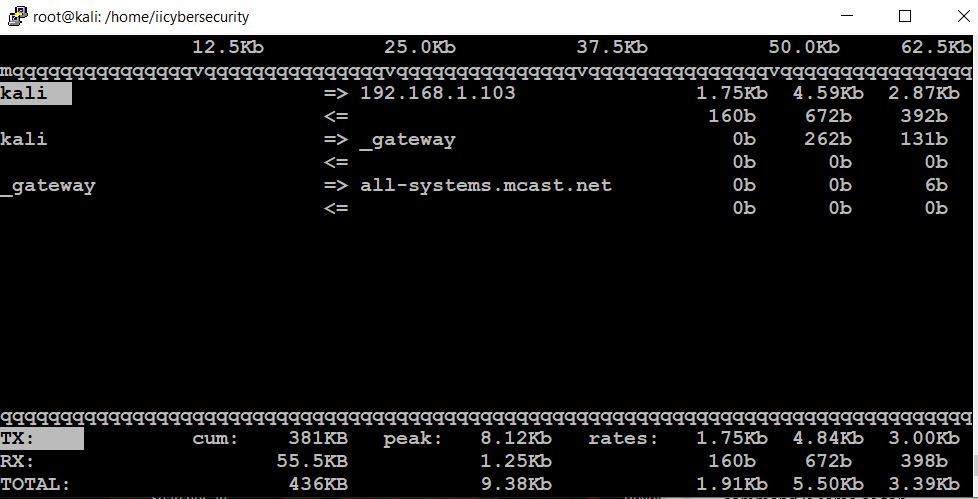
Check Listening Ports
Step 7: Hacker installs backdoor programs if he has compromised the Linux server. And all the backdoor run in the background, which can be identified using open ports. We can use command “netstat -plunt”. This command will list out all network connections in our system.
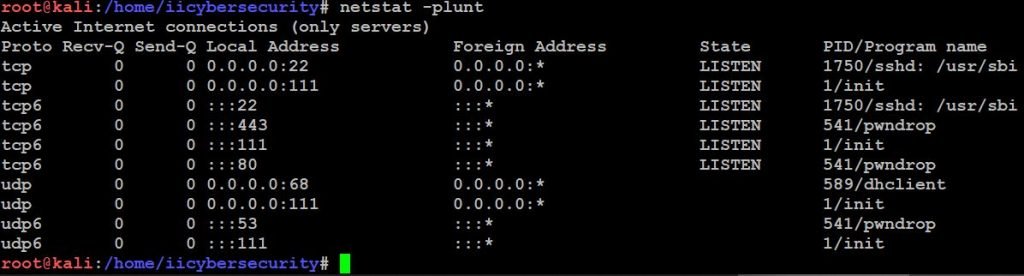
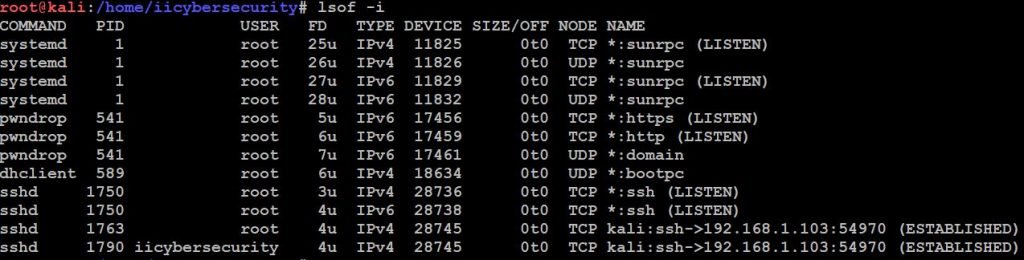
- We can also use this command “lsof -I” this will list out all open file in our system and we can check that file is opened by which process.
- Lsof : list of open files
- -I : select IPV files
- we can also use this to list out the process “lsof -p“
Check Rootkit
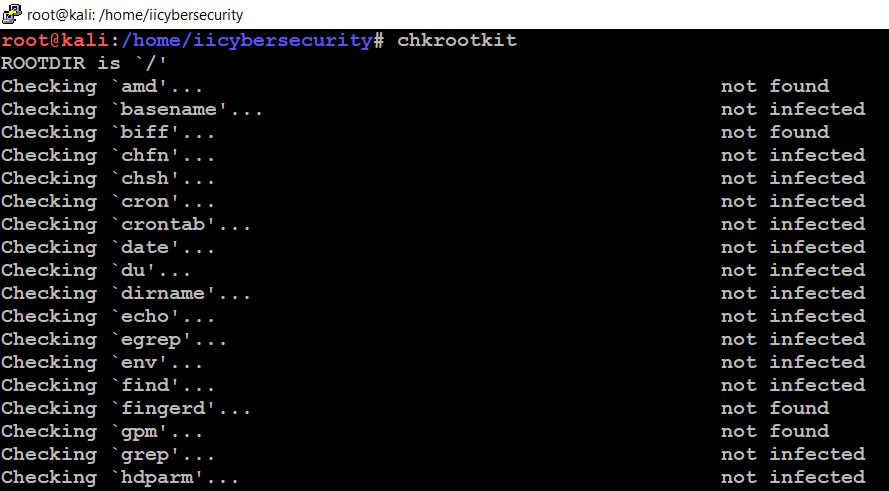
Step 8: Now, we can check any rootkit installed on the server or not. First we have to install the rootkit package by using the command “apt install chrootkit”.
After installing the package type this command “chrootkit”. This will debug any rootkit is injected to our system files.
Conclusion
So we studied basic commands to audit our linux system and to find out whether our linux server is compromised or not. There are many more tools available to audit your system in one go, which we will take up in upcoming posts.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











