According to data destruction experts, Citrix has been rolling out critical updates for its enterprise customers without publicly notifying what these improvements are. Reports indicate that these updates fix multiple security vulnerabilities present in Citrix ShareFile, a content collaboration platform.
The security notice was leaked by Dimitri van de Giessen, an ethical hacker and systems engineer. Starting today, this alert will be publicly available today on Citrix’s official website.
Citrix ShareFile is an enterprise-level file sharing solution. Employees using this system can securely exchange sensitive and proprietary business data. Data destruction experts mention that this software provides a secure on-premises cloud environment for data storage with auditing capabilities and compliance controls. For example, a company can remotely block or erase data from potentially compromised mobile devices (such as theft or loss).
Identified vulnerabilities (CVE-2020-7473, CVE-2020-8982, and CVE-2020-8983) specifically affect customer-managed Citrix ShareFile storage zone controllers, a component that stores corporate data behind the firewall.
Data destruction experts say that if exploited, these vulnerabilities could allow an unauthenticated threat actor to compromise the storage zone controller and access sensitive ShareFile documents and folders.
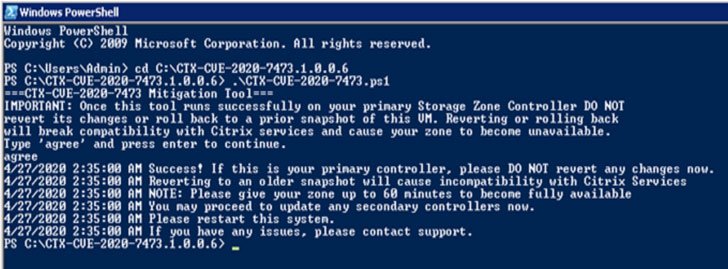
To fix these flaws, the company launched a mitigation tool that must be run on the primary storage zone controller and then on any secondary controller: “Once the tool runs successfully in its primary zone, you MUST NOT roll back any changes. Reversing the changes will make your zone unavailable,” the security alert mentions.
In addition to the on-premises solution, cloud versions of ShareFile storage zone controllers were also affected, but the company is already troubleshooting these flaws, so no additional user action is required.
Finally, although not many technical details about the underlying vulnerabilities are known, an update inspection revealed that at least one of these flaws could have resided in an old toolkit ASP.net that Citrix Sharefile used.
The outdated 9-year version of AjaxControlToolkit that is allegedly included with the affected versions of ShareFile software contains remote code execution and directory traversal vulnerabilities. These flaws were first revealed in 2015.
For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











