Introduction
Finding vulnerabilities in any website involves running so many tools and further analyzing the output. There are many paid tool available online, but how it sounds when you don’t have to pay for running a tool and that too by finding out the vulnerabilities in a website using one command. Coming to the rapidscan tool, we can use this tool to find out the vulnerabilities on a target website.
In this tool, we have different types of scanners like (Nmap, DNS recon, wafw00f, uniscan, sslyze, fierce, lbd, the harvester, DNSWalk, Golismero, Nikto, Dmitry, XSSer, etc). It performs an automatic scan using all the tools and generates the final report of the vulnerabilities. This is open source tool to find vulnerabilities in a website and it is used by researchers of International Institute of Cyber Security to perform quick scan on target websites used in labs.
Environment
- OS: Kali Linux 2019.3 64bit
- Kernel version: 5.2.0
Installation Steps
- Use this command to clone the project.
- git clone https://github.com/skavngr/rapidscan
root@kali:/home/iicybersecurity/rapidscan# git clone https://github.com/skavngr/rapidscan Cloning into 'rapidscan'… remote: Enumerating objects: 22, done. remote: Counting objects: 100% (22/22), done. remote: Compressing objects: 100% (20/20), done. remote: Total 474 (delta 10), reused 8 (delta 2), pack-reused 452 Receiving objects: 100% (474/474), 2.39 MiB | 1.49 MiB/s, done. Resolving deltas: 100% (275/275), done.
- Use the cd command to enter into rapidscan directory
root@kali:/home/iicybersecurity/rapidscan# cd rapidscan/ root@kali:/home/iicybersecurity/rapidscan/rapidscan#
- Now, use this command to find the help option of the tool
- ./rapidscan.py –help
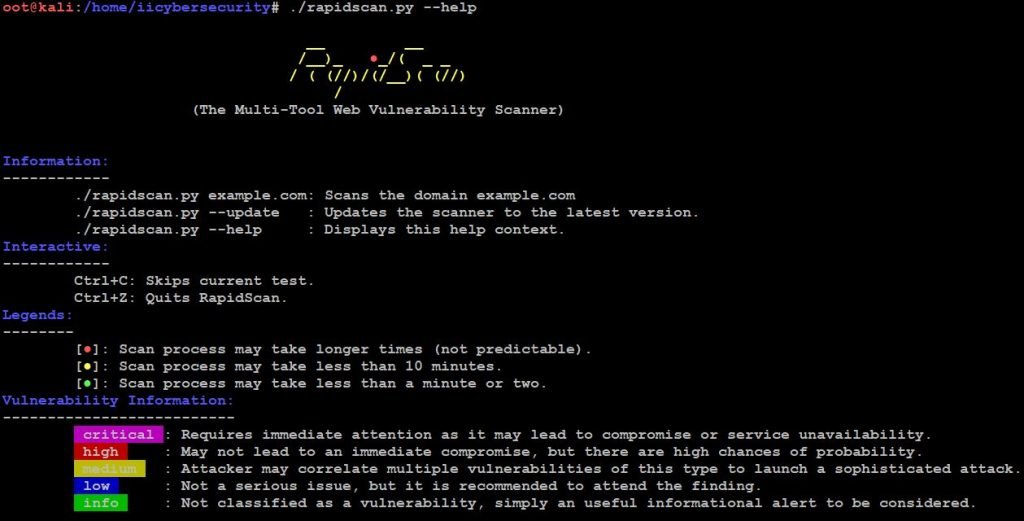
- Use this command to update the tools in the rapid scan.
- ./rapidscan.py –update
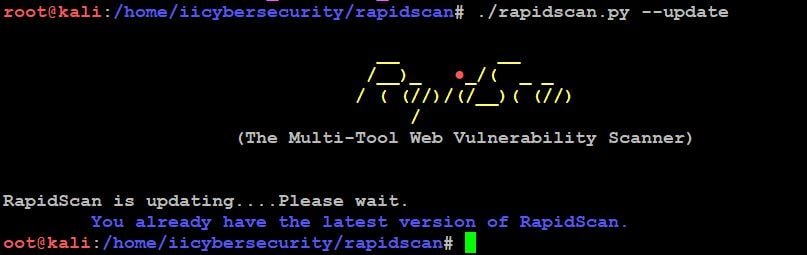
- Tool is already updated.
- Now, we will scan on DVWA web application:
- For testing, we will run DVWA as victim web server:
- For downloading DVWA iso go to: https://www.vulnhub.com/entry/damn-vulnerable-web-application-dvwa-107,43/
- After downloading iso, open iso in virtual box or vmware workstation. Then start iso.
- For getting DVWA ip type ifconfig, In our case IP was 192.168.1.105
- Now, use this command ./rapidscan.py http://192.168.1.105/
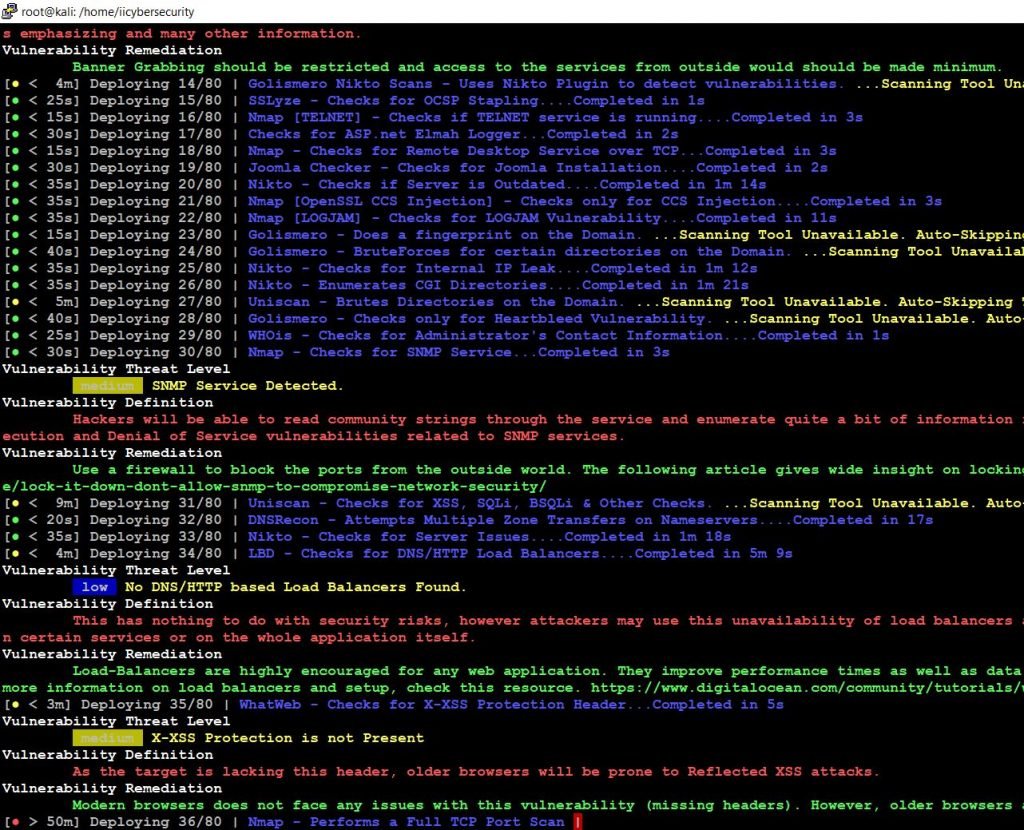
- It starts scanning the domain with all the tools which are available in the rapid scan. Once scanning domain website is done, it will list the vulnerability found in the website, with threat level parameters.
- If the vulnerability is “critical” it shows in “pink”
- If the vulnerability is “high” it shows in “red”
- If the vulnerability is “medium” it shows in “yellow”
- If the vulnerability is “low” it shows in “blue”
- If it’s not a vulnerability it shows in “green”
- After completion of scan, it generates a Vulnerability report., we can see in the below picture.
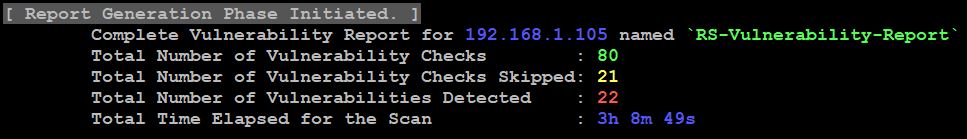
- Now, use the cat command to check the vulnerabilities.
- cat RS-Vulnerability-Report
- In the report, we have different scanners output with different vulnerabilities, open ports and available plugins in the domain.
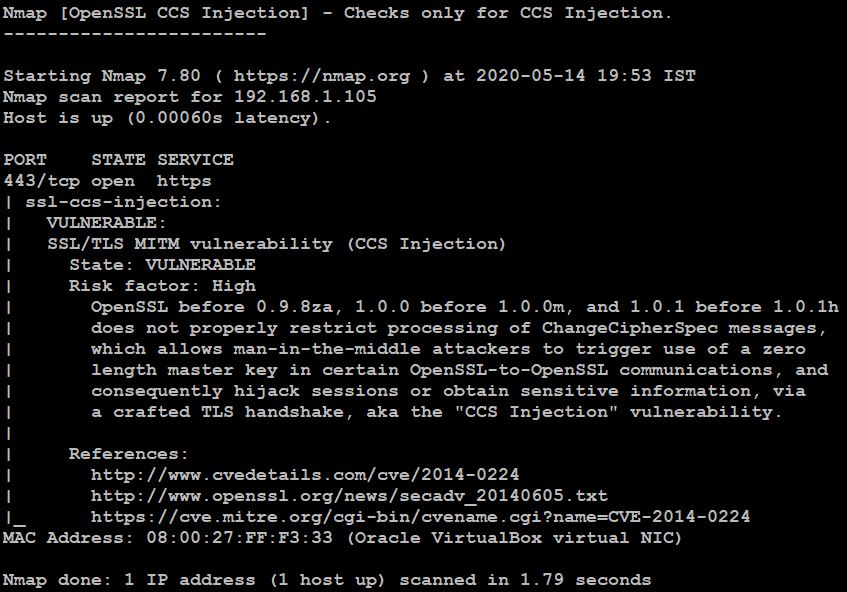
- In the above picture, we found a vulnerability, CSS (Cascading style sheet) Injection. CSS is used in webpages to change the text style, table size, and other options on a webpage.
- Now, CSS Injection is a client-side attack, here hacker can inject malicious code in the webpages.
CVE-2014-0224: CSS Injection Vulnerability in open SSL (Secure Socket Layer) before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h the ChangeCipherSpec Message doesn’t work properly. This allows the attacker to perform a man in the middle attack, this allows to start of zero-length key and in few cases, OpenSSL – to – OpenSSL communication that can hijack the session or gain other sensitive information through TLS handshake. trigger
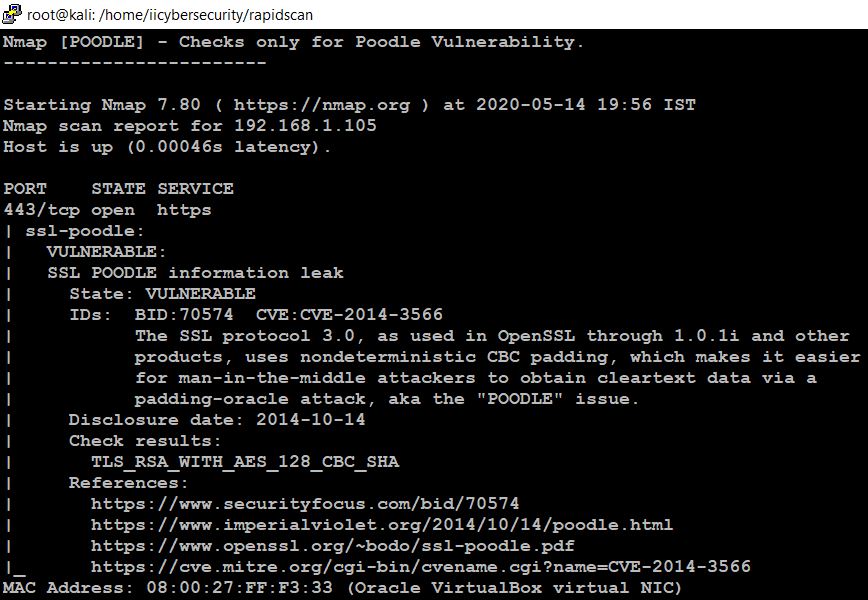
CVE-2014-3566: The OpenSSL uses SSL Protocol 3.0 through 1.0.1i and other products use nondeterministic CBC padding, so this makes easy to perform a man in the middle attack. Using a padding-oracle attack, the hacker can gain plain text data.
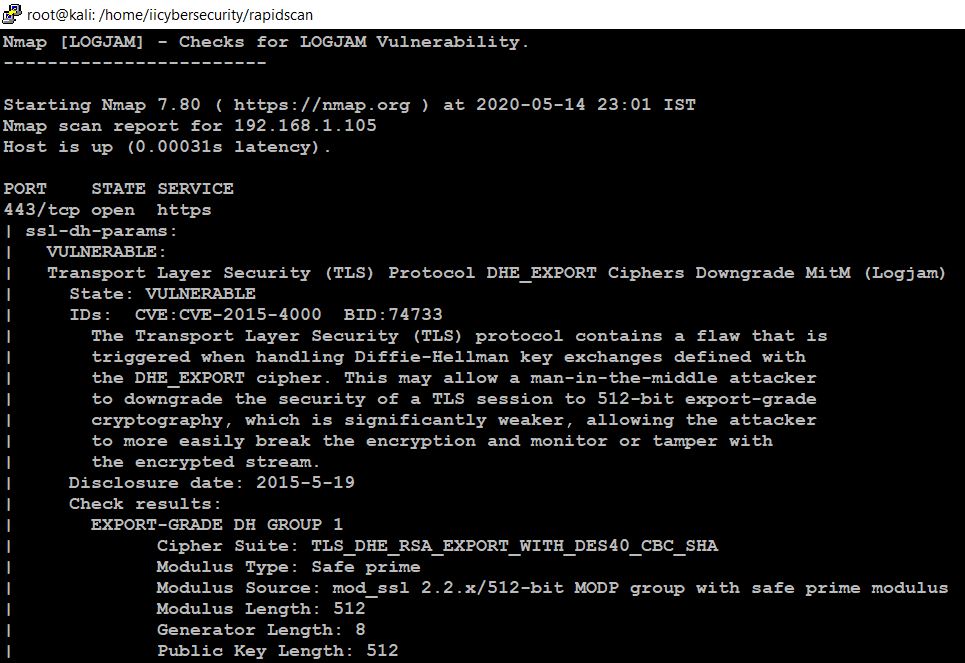
CVE-2015-4000: The Logjam issue is a security vulnerability. The TLS protocol 1.2 and previously DHE_EXPORT cipher suite is not enabled on the client but it enabled on the server, that does not carry DHE_EXPORT correctly, this allows a man in the middle attack, The Attacker can conduct a cipher-downgrade attack by rewriting a ClientHello with DHE in the same way to the server.
Conclusion
We found the high level vulnerabilities in a web application by using this tool and most of the penetration testers can this tool for results in a less time.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











