Researchers from vpnMentor have released a report on two critical vulnerabilities in Cyberoam firewall and VPN solutions. The flaws affect the company’s “email quarantine system”, to which threat actors could access without authentication.
The first of these flaws was reported in December 2019, while the second vulnerability was reported to vpnMentor by an anonymous ethical hacker in January 2020. By analyzing these security issues, vpnMentor discovered a third vulnerability affecting Cyberoam products. The flaws could be exploited by sending a malicious request that would allow hackers to execute arbitrary commands.
Indian-based Cyberoam was founded in 1999 and currently has 550 employees worldwide, working for more than 65,000 customers and 5,000 technology and software partners in 120 different countries.
The main problem is two vulnerabilities that affect how an email is released from the quarantine process on a Cyberoam device. The two flaws could be exploited by hackers to access compromised computers and facilitate the exploitation of Cyberoam firewall deployment. In addition, during the review of these flaws, experts discovered that the company’s solutions support default passwords, which was also reported as a security issue.
- The first flaw allows access to any Cyberoam device by exploiting the email quarantine release system. Multiple banks and private organizations employ Cyberoam solutions, so they could be exposed to these attacks
- The second report refers to a remote code pre-execution vulnerability and was discovered when implementing the security patch for the first flaw
By exploiting these security flaws, threat actors could access any Cyberoam security appliance via the firewall operating system web interface. These flaws exist due to a flaw in the way the service configured user account accesses on devices. Its exploitation does not require authentication and all attackers require is to know the IP address of the target device, in addition to a reliable shell.
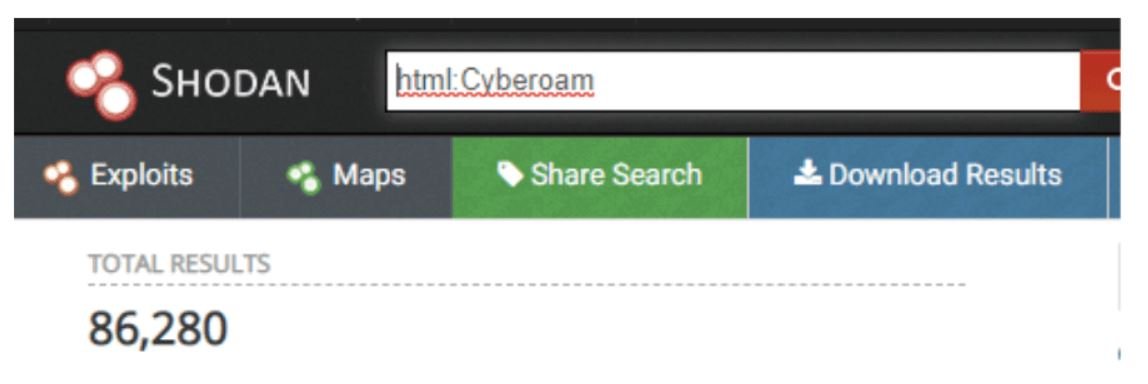
If attackers were able to remotely access the CyberoamOS shell, they could access any file on the server and maintain network-wide monitoring. When scanning using Shodan, experts detected at least 170,000 firewall implementations vulnerable to this attack. Of these, at least 86,000 IP addresses belong to Cyberoam devices, although the number of exposed deployments of this company could be much larger.
Like other flaws discovered in security software solutions, successful exploitation of these vulnerabilities could lead to scenarios such as theft of sensitive information, network hijacking, and malware packet manipulation to make them look legitimate. In addition, experts believe the flaw could be present in Cyberoam implementations launched over the past eight years.
The vulnerability has already been resolved. However, Cyberoam could still face subsequent cyberattack campaigns in search of other security flaws in the affected products, as it is a behavior associated with large groups of threat actors.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











