According to NinTechNet experts, developers of Visual Composer, a WordPress plugin with more than 80,000 currently active installations, announced the remediation of multiple vulnerabilities that would allow cross-site scripting (XSS) attacks to be deployed and firewall bypassed. Experts in a cyber security course mention that the flaws were in versions 25.0 and later, although they could also be found in some implementations of version 26.0.
XSS Vulnerability
Administrators can configure the plugin from the “Settings” page in the backend. Among the three available tabs, “CSS, HTML, and JavaScript”, which can be accessed in the “/wp-admin/admin.php?page?vcv-global-css-js” tabs, it allows you to inject CSS, JavaScript, or HTML code into each header or footer of the page:
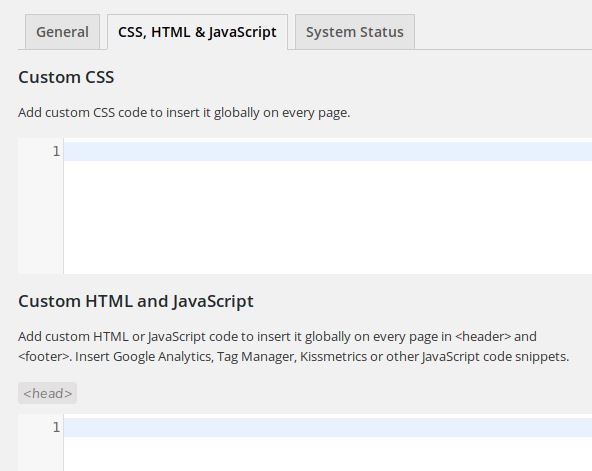
Like the third tab (System Status), it is loaded by calling the addSubmenuPage method from the script shown below:
“visualcomposer/visualcomposer/Modules/Settings/Traits/SubMenu.php”
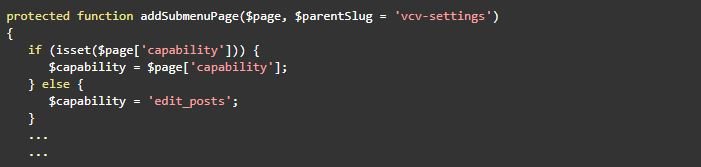
According to the experts in the cyber security course, then an optional user capability is expected as an argument. If it doesn’t occur, users who can edit posts will be restricted to default access, a capability available to low-privileged users, such as taxpayers. When you call addSubmenuPage to configure the tab, the addPage method in the script “visualcomposer/visualcomposer/Modules/Settings/Pages/CssJsSettings.php” does not pass a capability:
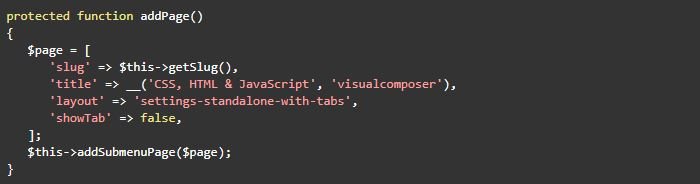
A contributing user can access the tab and inject JavaScript code into each page and website publication, both in the backend and in the interface:
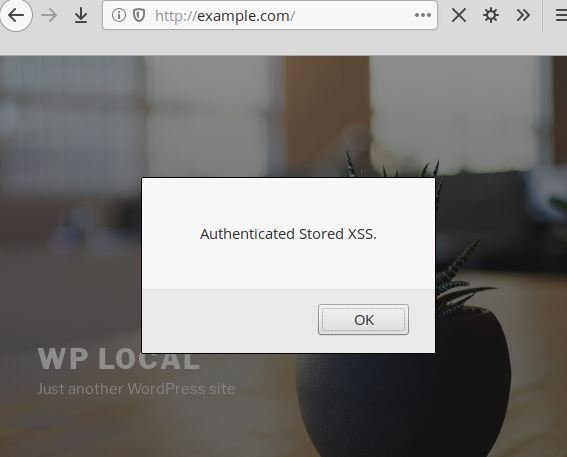
If users edit a post, they can also inject JavaScript code that applies to all users who can access the editor, including contributors and authors, unlike the WordPress editor, which only allows administrators and editors to insert JavaScript code.
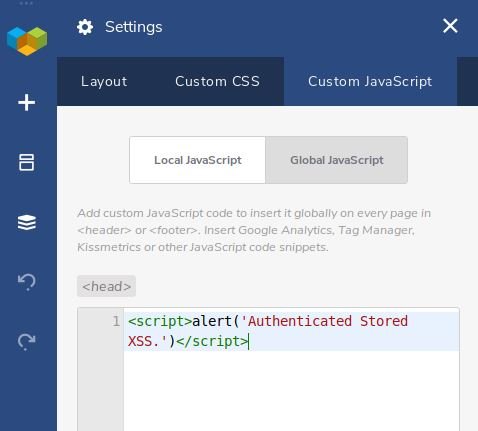
When contributing users save their post, it is saved as a “draft” because they do not have permission to post. However, JavaScript code is injected and executed immediately, on every page and post in the WordPress backend and site interface, the cyber security course specialists mention.
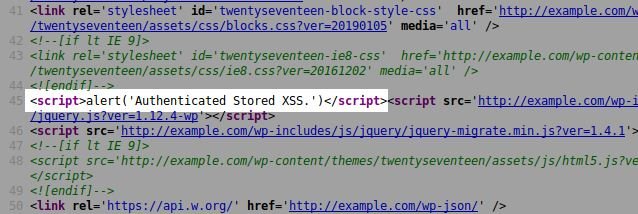
Bypass the firewall
When users save a post, the payload sent by Visual Composer is heavily obfuscated, so you can bypass the web application firewall and security plugins. The following is an example of the small payload used in the image above and sent via the VCv-admin-ajax AJAX action:
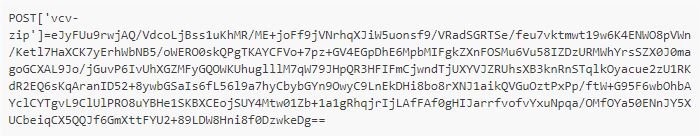
It is JSON-encoded, compressed into ZLIB and eventually encoded based 64.La decoding occurs in the parseRequest method of the following script:
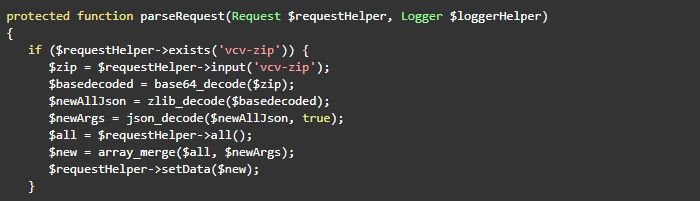
visualcomposer/visualcomposer/Modules/System/Ajax/Controller.php.
For security, users are recommended to upgrade to the latest version of Visual Composer, as well as verify their firewall settings. For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











