Introduction
There are many instances where you want to extract something from the screenshots or pictures. Hackers uses some of these techniques to extract data from images. Now, we list out the sensitive data inside the picture or a screenshot using a tool called Shotlooter. Its a recon tool and we will use this tool to find out the sensitive data in pictures using tesseract OCR (optical character recognition).
Tesseract is an OCR engine for the various operating systems. The shotlooter uses this tesseract to find out the sensitive data that might be passwords, Credit card numbers, API keys, etc. Using this tool, it will be easy to find out the sensitive data from a large database of images.
Environment
- OS: Kali Linux 2019.3 64bit
- Kernel version: 5.2.0
Installation Steps
- Use this command to install the system dependencies sudo apt install libsm6 libxext6 libxrender-dev tesseract-ocr -y
root@kali:/home/iicybersecurity# sudo apt install libsm6 libxext6 libxrender-dev tesseract-ocr -y Reading package lists... Done Building dependency tree Reading state information... Done libsm6 is already the newest version (2:1.2.3-1). libsm6 set to manually installed. libxext6 is already the newest version (2:1.3.3-1+b2). libxext6 set to manually installed. libxrender-dev is already the newest version (1:0.9.10-1). libxrender-dev set to manually installed. The following additional packages will be installed: liblept5 libtesseract4 tesseract-ocr-eng tesseract-ocr-osd The following NEW packages will be installed: liblept5 libtesseract4 tesseract-ocr tesseract-ocr-eng tesseract-ocr-osd 0 upgraded, 5 newly installed, 0 to remove and 1569 not upgraded. Need to get 7,197 kB of archives. =============================================================================================================SNIP================================================================================================================ Setting up tesseract-ocr-eng (1:4.00~git30-7274cfa-1) ... Setting up liblept5:amd64 (1.79.0-1) ... Setting up libtesseract4:amd64 (4.1.1-2) ... Setting up tesseract-ocr-osd (1:4.00~git30-7274cfa-1) ... Setting up tesseract-ocr (4.1.1-2) ... Processing triggers for man-db (2.8.6.1-1) ... Processing triggers for libc-bin (2.30-4) ... Scanning processes... Scanning linux images...
- Use this command to clone the project.
- git clone https://github.com/utkusen/shotlooter
root@kali:/home/iicybersecurity# git clone https://github.com/utkusen/shotlooter Cloning into 'shotlooter'... remote: Enumerating objects: 52, done. remote: Counting objects: 100% (52/52), done. remote: Compressing objects: 100% (49/49), done. remote: Total 52 (delta 21), reused 20 (delta 1), pack-reused 0 Receiving objects: 100% (52/52), 948.56 KiB | 707.00 KiB/s, done. Resolving deltas: 100% (21/21), done.
- Use the cd command to enter into shotlooter directory.
root@kali:/home/iicybersecurity# cd shotlooter/ root@kali:/home/iicybersecurity/shotlooter#
- Use this command to install the requirements, pip3 install -r requirements.txt
root@kali:/home/iicybersecurity/shotlooter# pip3 install -r requirements.txt Requirement already satisfied: requests in /usr/local/lib/python3.8/dist-packages (from -r requirements.txt (line 1)) (2.23.0) Requirement already satisfied: beautifulsoup4 in /usr/local/lib/python3.8/dist-packages (from -r requirements.txt (line 2)) (4.8.2) Requirement already satisfied: Pillow in /usr/lib/python3/dist-packages (from -r requirements.txt (line 3)) (6.2.1) Collecting pytesseract Downloading pytesseract-0.3.4.tar.gz (13 kB) Requirement already satisfied: numpy in /usr/lib/python3/dist-packages (from -r requirements.txt (line 5)) (1.17.4) Collecting imutils Downloading imutils-0.5.3.tar.gz (17 kB) Collecting opencv-python-headless Downloading opencv_python_headless-4.2.0.34-cp38-cp38-manylinux1_x86_64.whl (21.6 MB) |████████████████████████████████| 21.6 MB 165 kB/s ==============================================================================================================SNIP=============================================================================================================== Stored in directory: /root/.cache/pip/wheels/c8/d6/0f/b0c3892b70c59f0d202f8619a449f7d14cb839a0af2f943869 Successfully built pytesseract imutils Installing collected packages: pytesseract, imutils, opencv-python-headless Successfully installed imutils-0.5.3 opencv-python-headless-4.2.0.34 pytesseract
- Now, use this command to find help option
- python3 shotlooter.py -h
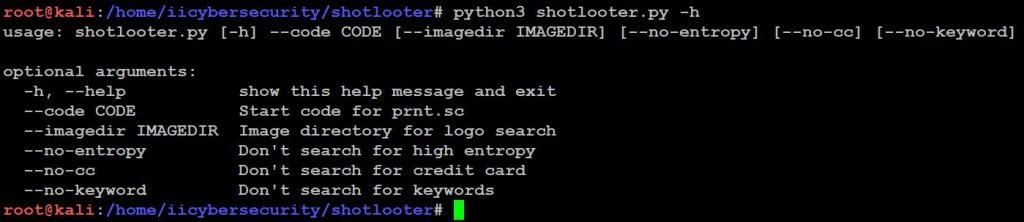
- Now, use this command to find the sensitive information python3 shotlooter.py –code sjgmm1
- After using this command, it starts scanning all the data which is stored in the database like (API keys, private_key, smtp_pass, access key, mongodb+srv etc) and we can also specify by adding this option like –no-cc, –no-keyword and, –no-entropy
root@kali:/home/iicybersecurity/shotlooter# python3 shotlooter.py --code sjgmm1 Analyzing: sjgmm2 Analyzing: sjgmm3 Analyzing: sjgmm4 Analyzing: sjgmm5 Analyzing: sjgmm6 Analyzing: sjgmm7 Analyzing: sjgmm8 Analyzing: sjgmm9 Analyzing: sjgmma Analyzing: sjgmmb Analyzing: sjgmmc Analyzing: sjgmmd Analyzing: sjgmme Analyzing: sjgmmf Analyzing: sjgmmg Analyzing: sjgmmh Analyzing: sjgmmi Analyzing: sjgmmj Analyzing: sjgmmk Analyzing: sjgmml Analyzing: sjgmmm /usr/lib/python3/dist-packages/PIL/Image.py:988: UserWarning: Palette images with Transparency expressed in bytes should be converted to RGBA images warnings.warn( Analyzing: sjgmmn Analyzing: sjgmmo Analyzing: sjgmmp Analyzing: sjgmmq Analyzing: sjgmmr Analyzing: sjgmms Analyzing: sjgmmt Analyzing: sjgmmu
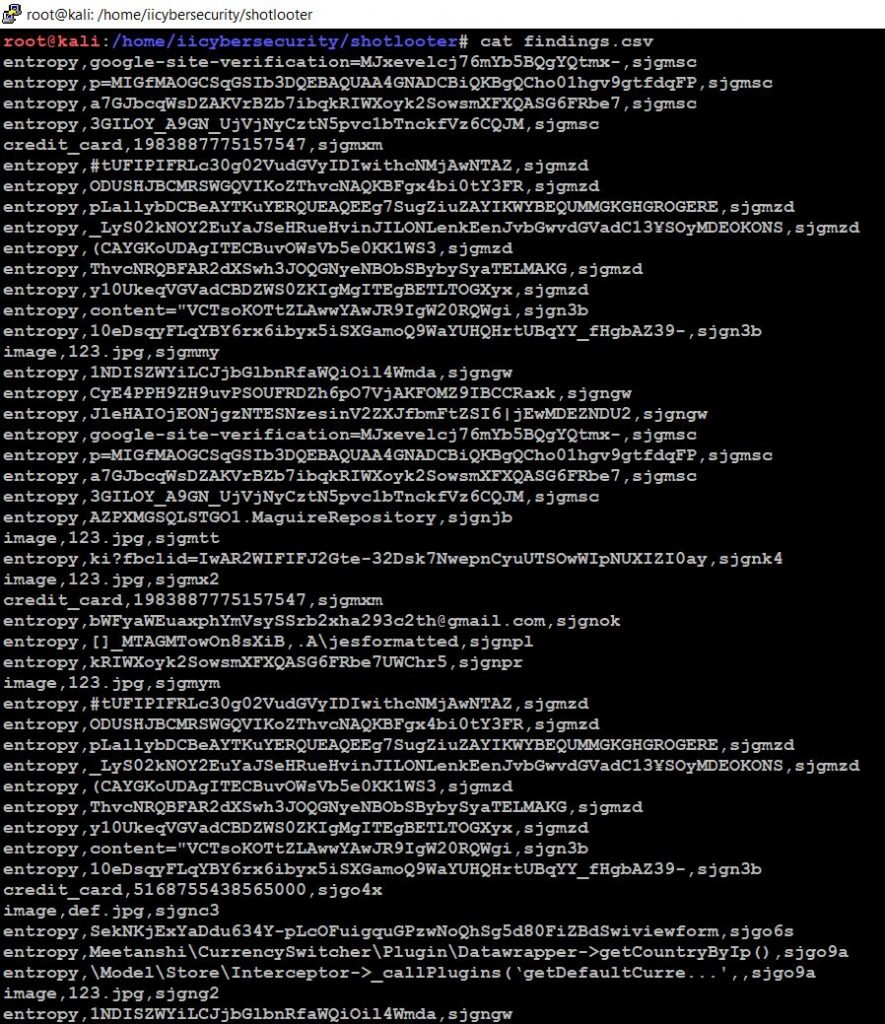
- After scanning it stores two different files findings.csv and output.
- In the findings.csv file it contains all the high entropy (API Keys) and in the output directory it contains all the sensitive images
- Now, use cat command to view the data in findings.csv
- cat findings.csv
- Now, use cd command to enter into output directory to view the sensitive images.
root@kali:/home/iicybersecurity/shotlooter# cd output/ root@kali:/home/iicybersecurity/shotlooter/output# ls placeholder sjgmtt.png sjgmym.png sjgn3b.png sjgng2.png sjgniq.png sjgnok.png sjgnsx.png sjgo9a.png sjgoj8.png sjgoza.png sjgmmy.png sjgmx2.png sjgmzd.png sjgn4.png sjgngw.png sjgnjb.png sjgnpl.png sjgo4x.png sjgofb.png sjgoks.png sjgmsc.png sjgmxm.png sjgn28.png sjgnc3.png sjgnh2.png sjgnk4.png sjgnpr.png sjgo6s.png sjgoho.png sjgokz.png
- Now, open the file to verify the sensitive data.
- sjgngw.png
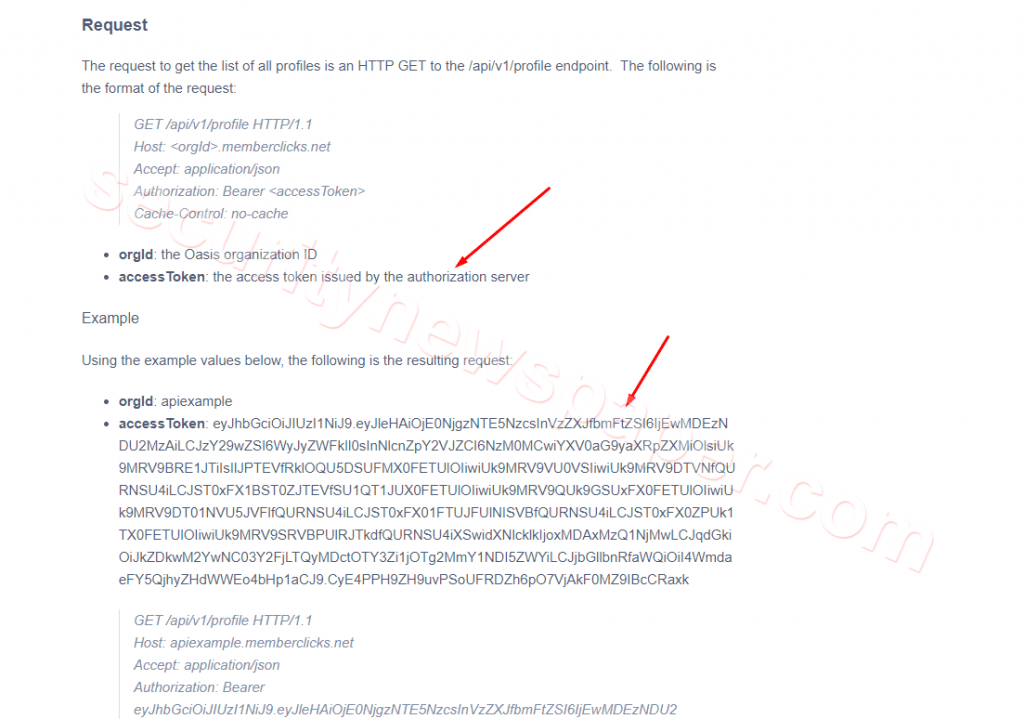
- In the above picture, we see access token by the authorization server
- Now, Open the other picture
- sjgnok.png
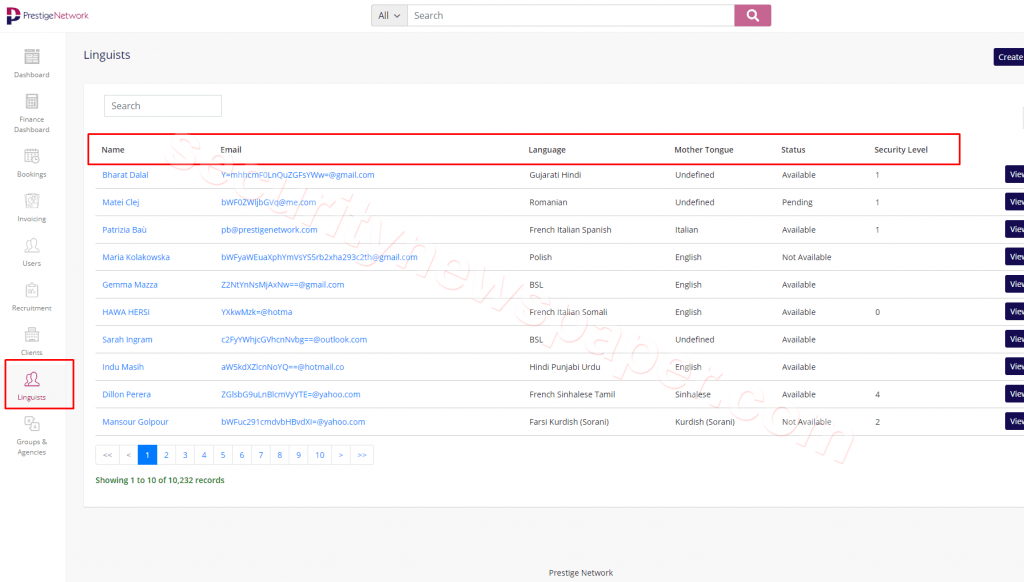
- In the above picture we see Email IDs.
Conclusion
- We saw how easy to retrieve the sensitive information from the high database. You can also test with your custom images to extract sensitive data from screenshots.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











