A team of vulnerability assessment specialists has revealed the finding of a serious security flaw present in most Android versions. Apparently, exploiting this flaw would allow a malware variant to impersonate some legitimate applications, which would expose users to malicious activities such as spying or password and other sensitive details theft.
The flaw was discovered by researchers from Norway-based cybersecurity firm Promon. Known as Strandhogg 2.0 (a Nordic term used to refer to violent attacks), this vulnerability is identical to another flaw found before and is present on any Android device running version 9.0 and earlier.
Vulnerability assessment experts mention that hackers should trick victims with fake login pages to exploit the vulnerability. Using this flaw, threat actors could also take control of the permissions of other applications and divert sensitive information from the victim, including contacts, images and real-time location data, among other details.
The vulnerability works by abusing the Android system’s multitasking system, which controls all applications recently opened by the user of a mobile device. To successfully complete an attack, hackers require the victim to download a malicious application that poses as a legitimate product. Once installed, the malicious app could hijack the legitimate service to inject malicious code.
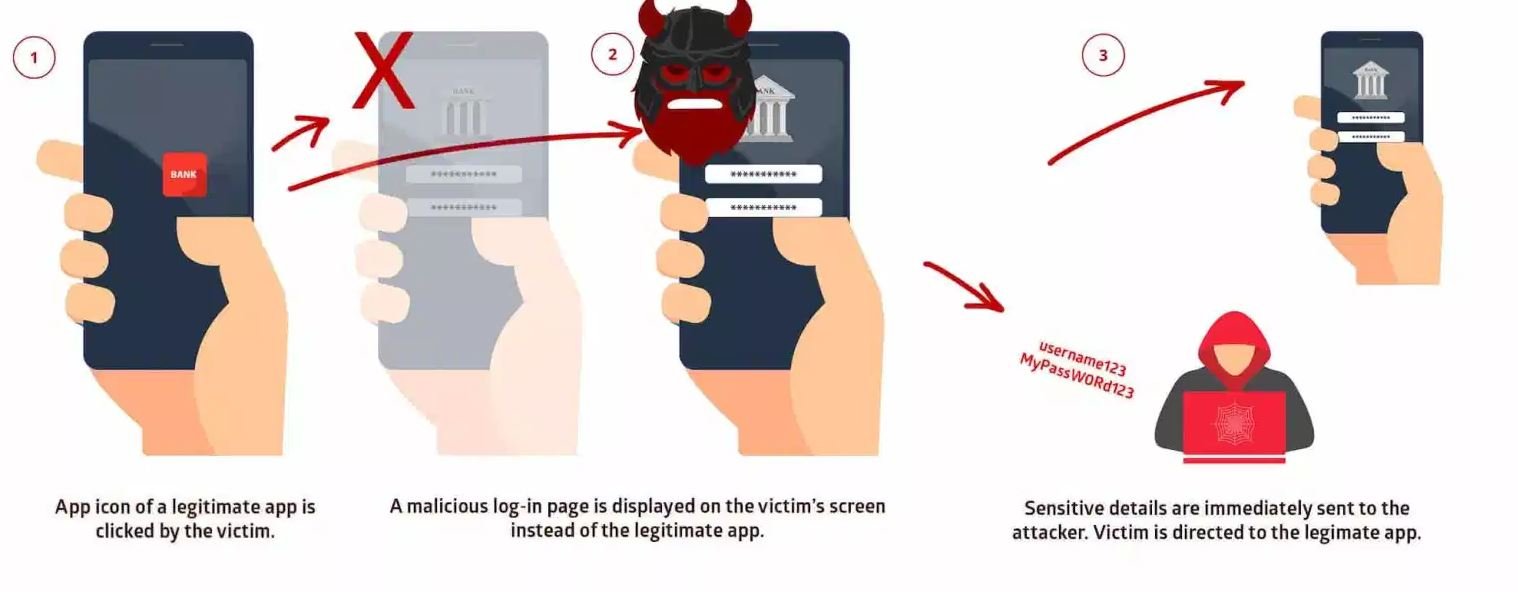
When a victim enters their password in the fake login window, their passwords are diverted to the servers controlled by the hackers. Finally, the legitimate application starts as if nothing had happened.
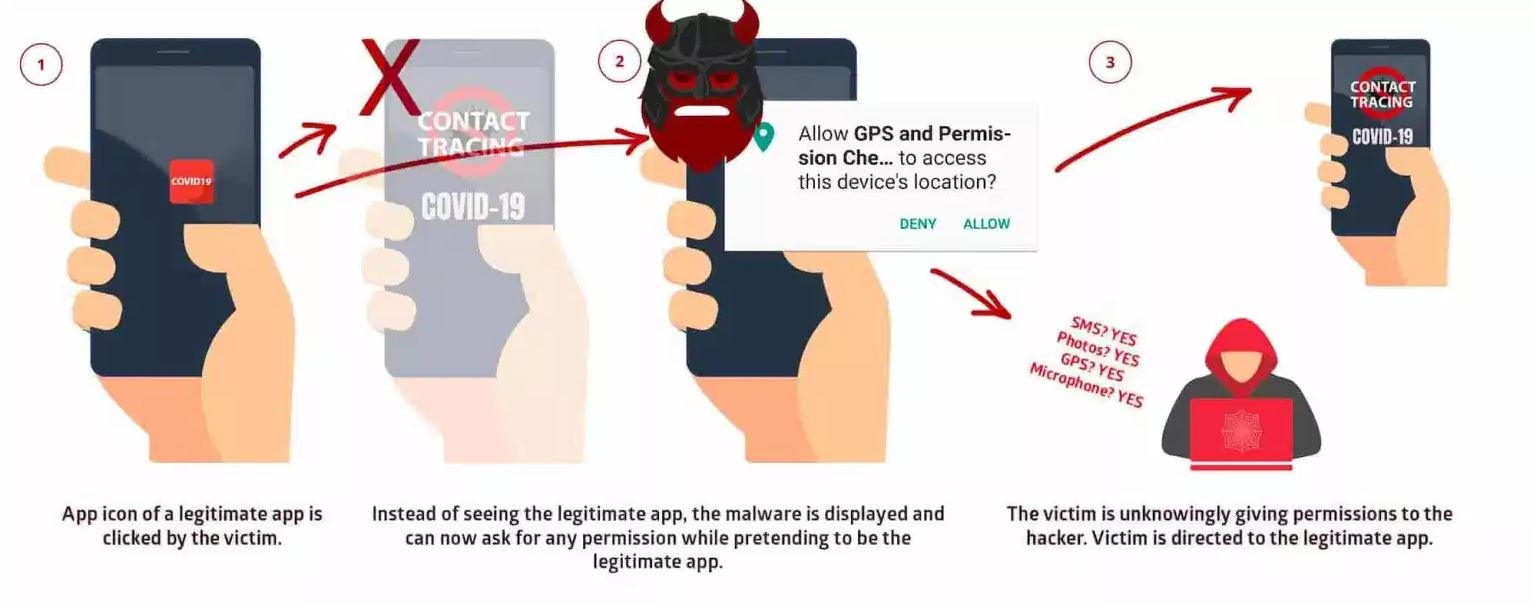
Researchers believe this flaw could be much more dangerous than the first version, as it is almost undetectable to any mobile device user. Although the flaw exists in millions of devices, experts who revealed the finding say that no cases of exploitation have been presented in real-world scenarios so far. The real problem is the inability to detect an attack, as even users with greater technical knowledge could not be able to identify malicious activity.
In this regard, Google also states that no attempts at active exploitation have been detected: “We launched a solution for this flaw after receiving the report, which we appreciate,” a company spokesperson said. The Google Play Protect system is also of great help in combating such flaws, because it blocks applications that could be used for exploiting such errors, mentioned by experts in vulnerability assessment.
For further reports on vulnerabilities, exploits, malware variants and computer security risks you can access the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











