Facebook is the most widely used social network in the world, which also makes it a frequent target for attacks. A security testing course specialist originally from India discovered and reported multiple flaws in the platform and on a third-party business intelligence portal; thanks to his report, the researcher received a $31K USD bug bounty.
Bipin Jitiya published her research on Medium a couple of days ago, in which he mentions that the error was discovered by combining secure code reviews, enumeration, and extensive scripting knowledge.
The researcher, specializing in application development and pentesting, found a server-side request forgery (SSRF) flaw in the source code of a publicly accessible endpoint built with MicroStrategy tools, which performed custom data collection and content generation. According to security testing course experts, MicroStrategy has acted as Facebook partner in various data analytics projects.
In addition, Jitiya found another SSRF vulnerability in MicroStrategy Software Development Kit (SDK) code that could be exploited by threat actors to send GET requests to internal and external systems. “This vulnerability has a medium severity impact on the affected system,” the researcher says.
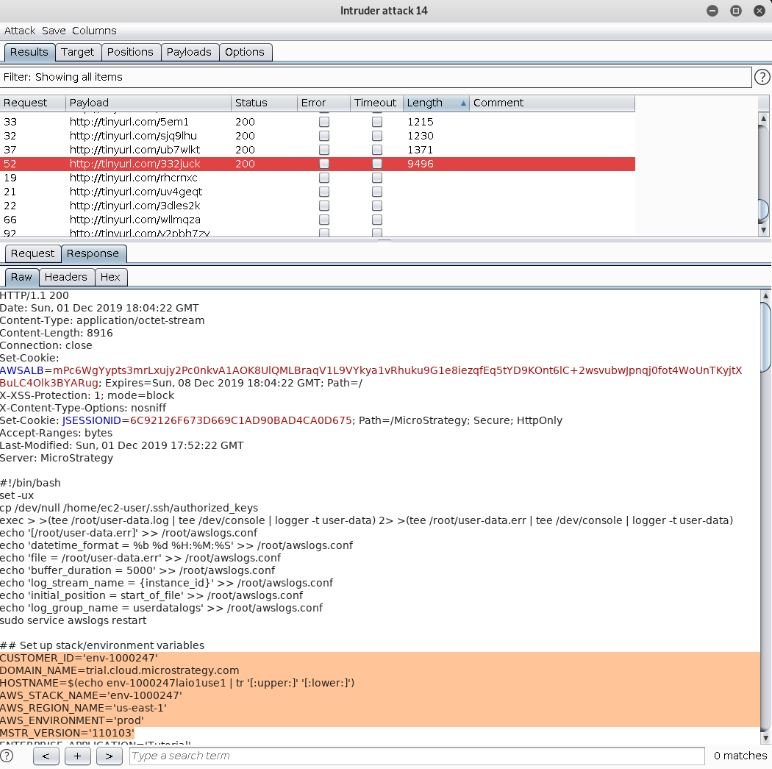
However, the impact of this vulnerability increases considerably if it is chained to a data leaking scenario. The researcher found that a URL shortening tool used by Facebook employees and some external users could filter sensitive information about the server.
Among the data exposed by this flaw experts could found information about the internal path to the logs folder, system queries, internal IP addresses, internal user names, data related to the system configuration, among others: “Exploiting this fault, malicious hackers could list valid internal URLs in the system”. Security testing course experts mention that malicious actors could use these flaws to perform path traversal and SSRF attacks.
“Attackers could find an internal URL used to update or delete files from the server and use it for malicious purposes,” Jitiya added in statements for a specialized platform. The researcher concluded by mentioning that there is also the possibility to delete any confidential files or even delete driver files, such as login.php, profile.php, among others.
Although at the beginning Facebook refused to acknowledge the report due to the absence of proof of concept, Jitiya eventually received the reward. For further reports on vulnerabilities, exploits, malware variants, and computer security risks, cybersecurity awareness experts recommend entering the International Institute of Cyber Security (IICS) website, as well as official technology company platforms.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











