One of the fastest growing trends in the cybercrime world over the past two years is ransomware as a service. In this operating model, ransomware developers put their malicious creations for sale so that others can deploy encryption malware attacks against other users, as mentioned by experts in secure data erasure. The creators of the malware do not directly handle the attacks, but are only dedicated to selling and updating the code used to encrypt the files of the victims.
In early 2020, the firm Recorded Future detected Thanos, a new variant of ransomware developed by a self-named user “Nosophoros“. This malware is for sale on a malicious hacking platform known as Exploit Forum.
According to the experts in secure data erasure, Thanos is a ransomware generator tool (or builder) written in C# programming language very easy to understand and employ, able to create new clients based on 43 different configuration options. Below are the results of the analysis that Recorded Future researchers performed on this ransomware builder.
How does this builder work?
Thanos offers malicious hackers the ability to create new variants with multiple different options (such as the type of cryptocurrency in which the ransom has to be paid) based on some other options set by default.
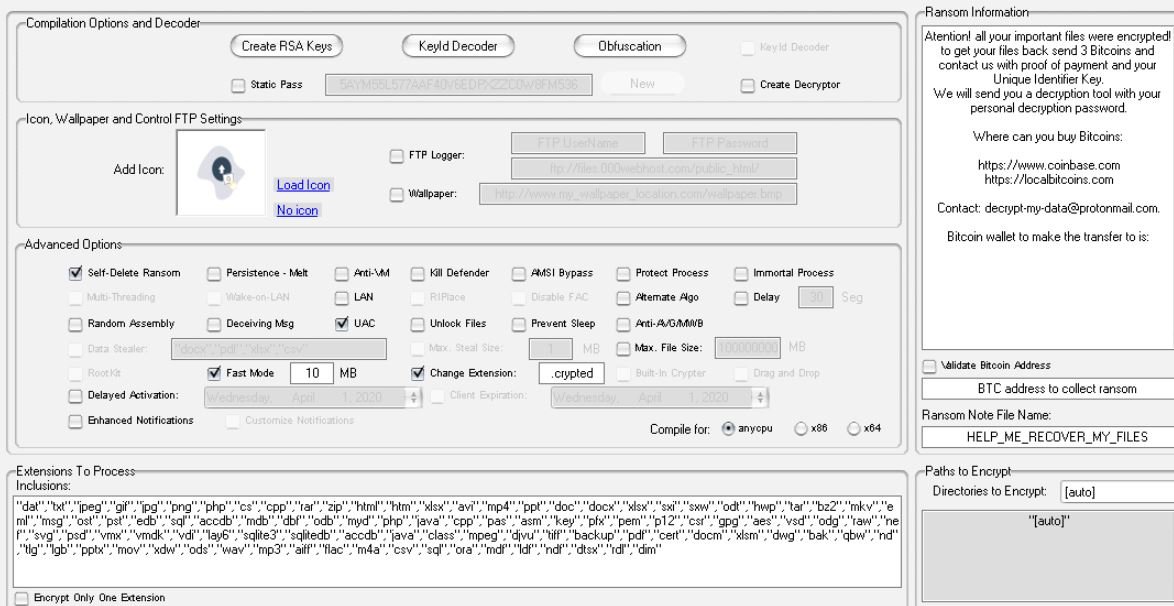
After the hackers configured the tool according to their plans, Thanos generates a .NET executable in a default directory. The generated binaries result from replacing strings in a base binary according to the options set by the hackers.

This builder also handles the obfuscation of the final binaries with two different methods. The main method is based on a decrypted version of SmartAssembly, a commercial tool. The secondary method is a configuration option that creates an Inno Setup installation file with the client as an embedded resource file.
Thanos Ransomware
The Thanos client is written in C# and all generated clients have random strings for method names, variable names, and class names, point to experts in secure data erasure. The client will contain 12 to 17 classes depending on the options and settings selected when creating the malware. Some of the classes, such as Program and Crypto, are included in each build, while others, such as NetworkSpreading and Wake on LAN, are only included in the final binary, if the respective option is selected.
The following is a table with the main classes resulting from this process:
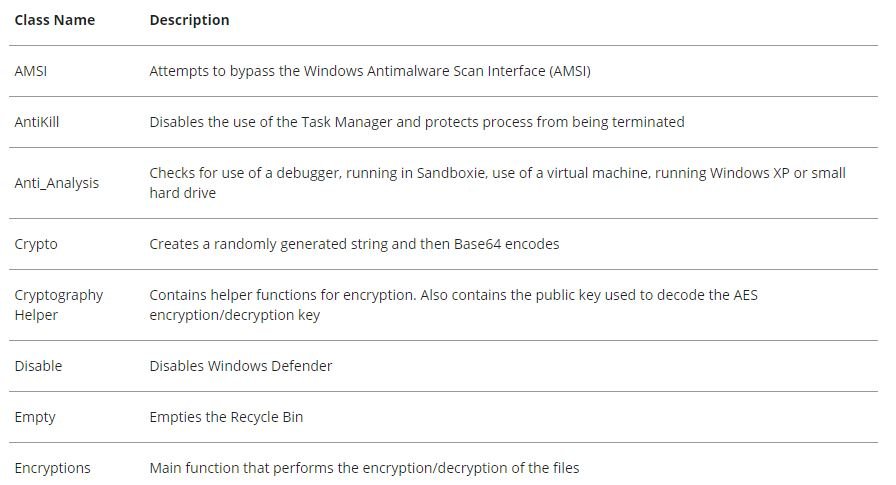
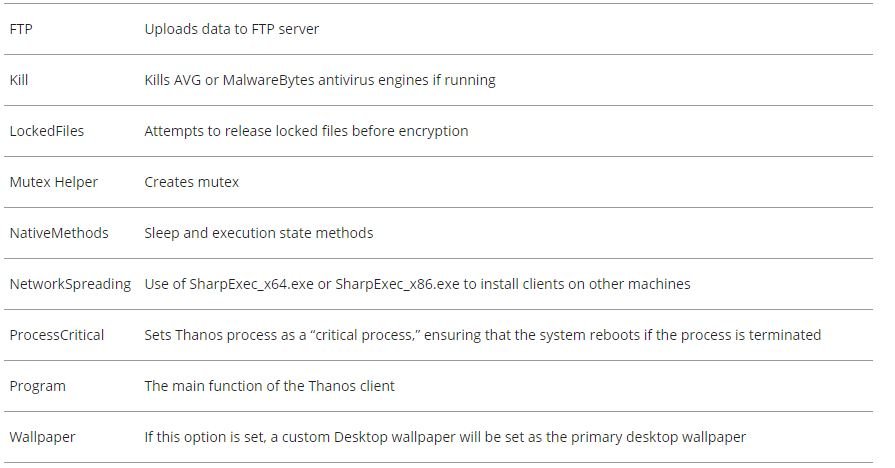
Thanos Client Execution Flow
The Thanos general execution flaw contains three main activities that are described below:
- Advanced options: To perform configuration-related actions
- Prevention and recovery: Stops services and processes that could prevent malware from running and looks for backups for removal
- Encryption and upload: Files are encrypted and uploaded to FTP if configured to do so during compilation and the ransom note is displayed to the victim
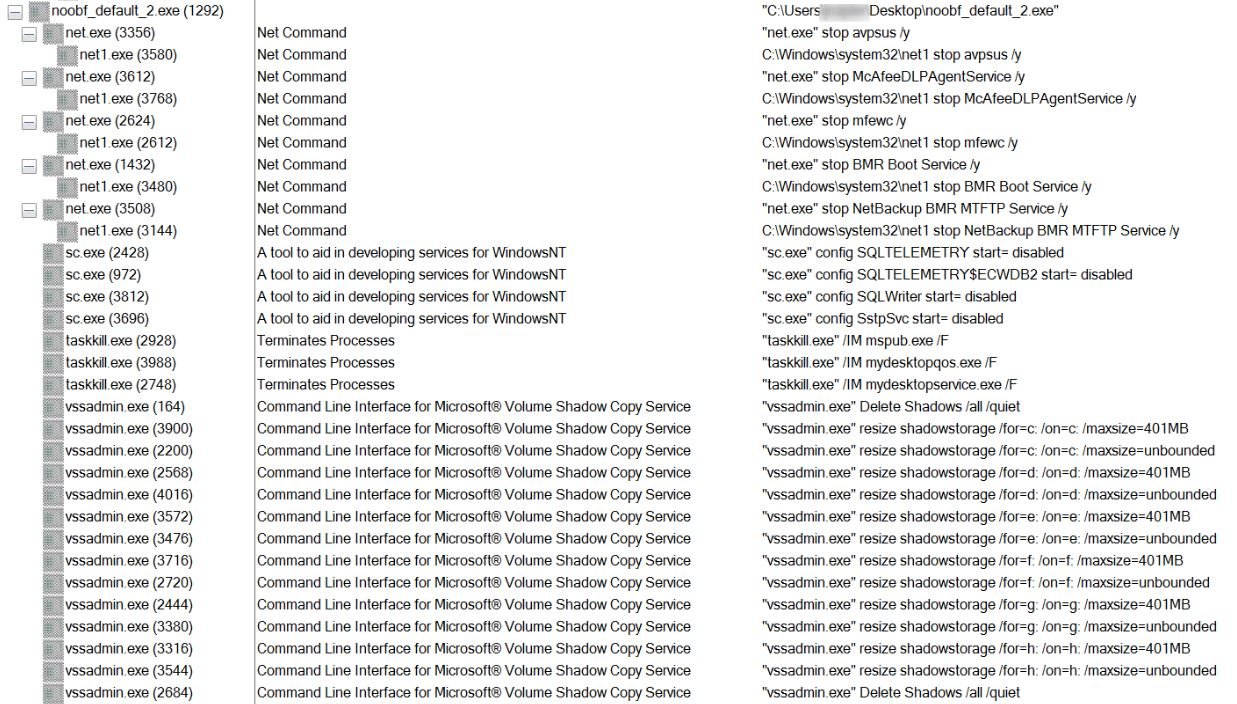
Hackers could also extract some files from victims and post them on some website as evidence of the attack.
Researchers say Thanos has received very positive reviews from the cybercriminal community, as it runs smoothly and is constantly updated. The hacking groups that use this tool could generate huge profits, which benefits the developers of Thanos and makes it difficult to create a decryption tool.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











