Introduction
All pentesters out there, always want a Framework that can give them access to all pentesting tools in one console. This makes their job easy. There are many pentesting framework available on internet today, but the ones which are modular in nature are the ones a good candidature.
Fsociety is a modular penetration testing tool, which has many modules like Information gathering, Password Attack, Networking, Web App, obfuscation, and Utilities. Under each module there are sub hacking tools in one place. Researcher of International institute of Cyber Security also uses such kind of Modular Pentesting Frameworks. Now no need to remember the command, we can simply execute by choosing the required options. Using this tool we can reduce time to execute the test with the best results.
Environment
- OS: Kali Linux 2019.3 64 bit
- Kernel version: 5.2.0
Installation Steps
- Use this command to install the tool pip install fsociety
Requirement already satisfied: fsociety in /usr/local/lib/python3.8/dist-packages (3.2.3) Requirement already satisfied: requests in /usr/local/lib/python3.8/dist-packages (from fsociety) (2.23.0) Requirement already satisfied: rich in /usr/local/lib/python3.8/dist-packages (from fsociety) (2.2.3) Requirement already satisfied: gitpython in /usr/local/lib/python3.8/dist-packages (from fsociety) (3.1.3) Requirement already satisfied: chardet<4,>=3.0.2 in /usr/lib/python3/dist-packages (from requests->fsociety) (3.0.4) Requirement already satisfied: urllib3!=1.25.0,!=1.25.1,<1.26,>=1.21.1 in /usr/local/lib/python3.8/dist-packages (from requests->fsociety) (1.25.8) Requirement already satisfied: idna<3,>=2.5 in /usr/local/lib/python3.8/dist-packages (from requests->fsociety) (2.9) Requirement already satisfied: certifi>=2017.4.17 in /usr/local/lib/python3.8/dist-packages (from requests->fsociety) (2019.11.28) Requirement already satisfied: colorama<0.5.0,>=0.4.0 in /usr/local/lib/python3.8/dist-packages (from rich->fsociety) (0.4.3) Requirement already satisfied: commonmark<0.10.0,>=0.9.0 in /usr/local/lib/python3.8/dist-packages (from rich->fsociety) (0.9.1) Requirement already satisfied: pygments<3.0.0,>=2.6.0 in /usr/local/lib/python3.8/dist-packages (from rich->fsociety) (2.6.1) Requirement already satisfied: typing-extensions<4.0.0,>=3.7.4 in /usr/local/lib/python3.8/dist-packages (from rich->fsociety) (3.7.4.2) Requirement already satisfied: pprintpp<0.5.0,>=0.4.0 in /usr/local/lib/python3.8/dist-packages (from rich->fsociety) (0.4.0) Requirement already satisfied: gitdb<5,>=4.0.1 in /usr/local/lib/python3.8/dist-packages (from gitpython->fsociety) (4.0.5) Requirement already satisfied: smmap<4,>=3.0.1 in /usr/local/lib/python3.8/dist-packages (from gitdb<5,>=4.0.1->gitpython->fsociety) (3.0.4)
- Next, use this command to upgrade the tool pip install –upgrade fsociety
- Now, simply use this command to launch the tool
- fsociety
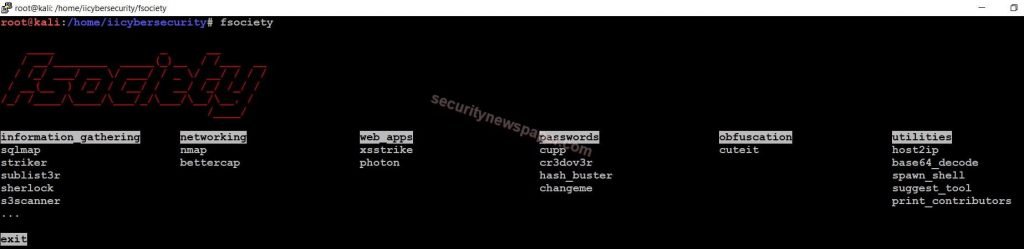
- Here, we successfully launched the tool
- In the above picture we see 6 modules with different 20 tools.
Information Gathering
Information gathering is also called as footprinting. We use this module in the first stage of penetration testing, for collecting the required details about the target to perform an attack or to secure the device, that no hacker can compromise the device.
- Now, type information_gathering to view it’s tools
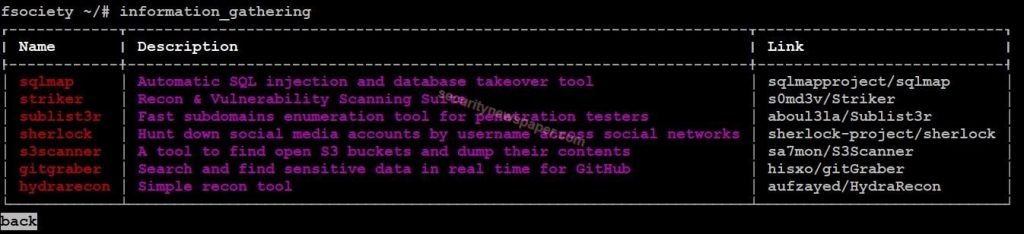
- In this module we have 7 different tools
- SQLMap: SQLMap is an automatic SQL injection tool. We use this tool to find out vulnerabilities on a website and stealing the confidential data from the database server. This is an open-source and penetration testing tool.
- Striker: Striker is an information gathering and vulnerability scanning tool for the websites. This tool will collect Open ports, Email Addresses, DNS records, IP addresses, servers, and Operating systems.
- Sublist3r: Sublist3r is a subdomain enumeration tool. This will collect all the subdomains from different search engines like Bing, Google, Yahoo. This tool builds on the python language. We can use this tool for OSINT (Open sources investigation)
- Now, Lets take one tool to understand its working.
- Type sublist3r to launch the tool.
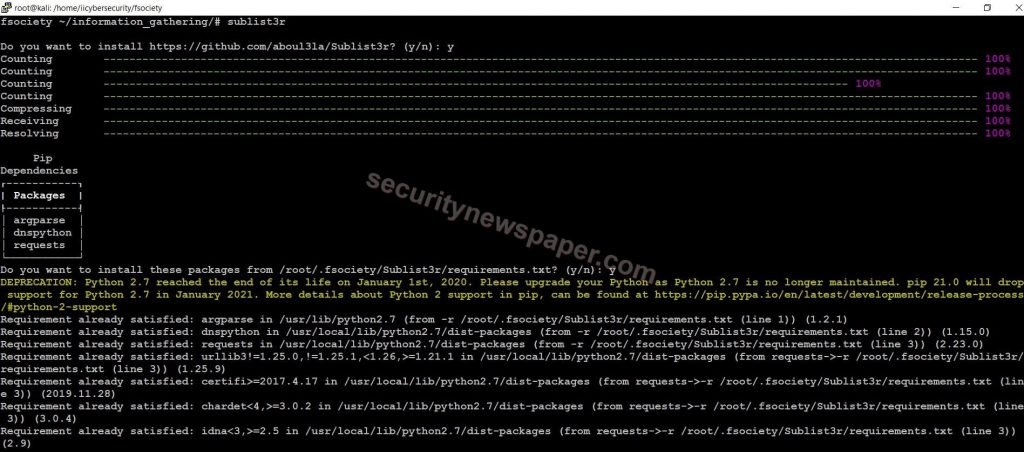
- After typing the command, this will download and install the dependencies of the tool.
- Then it will launches the tool.
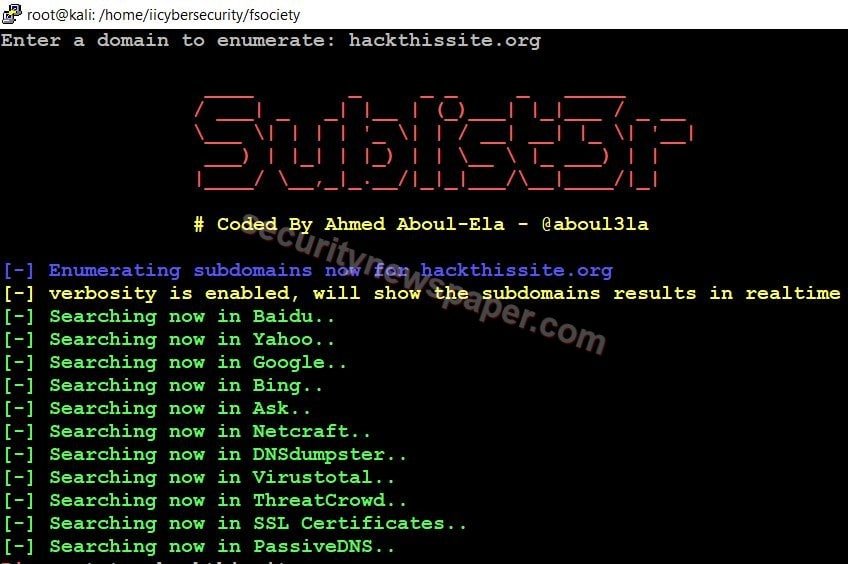
- Here, enter the domain name.
- Tool will start searching the subdomains using search engines and at last, the tool will display the results.
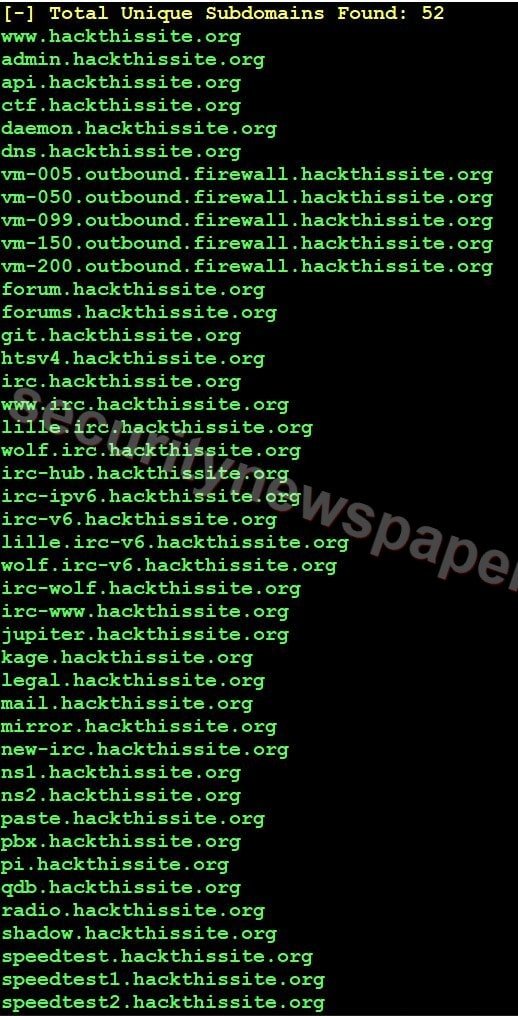
- Here, we got the 52 unique sub domains.
- Sherlock: Sherlock is an information-gathering tool, we use this tool for collecting Username from the different social media websites. We can also perform social engineering attacks using this.
- S3scanner: S3scanner is used to collect the data from Amazon s3 by simply specifying the domain name. After completing the scanning, it stores the results in a text file.
- Gitgraber: Gitgraber is used to collect sensitive information from the different websites/online services like Google, Amazon, Paypal, Github, Facebook, Twitter. We use this tool in time environment
- Hydrarecon: Hydrarecon is a simple recon tool. We use this to collect the live domain, sub-domains, open port scan.
Networking
- In this module, we have 2 different tools.
- Type networking to use the module.
- Then type Nmap to launch the tool
- Here, we have to enter the host address on which IP we want to scan
- The Nmap tool displays few options, related to scanning.
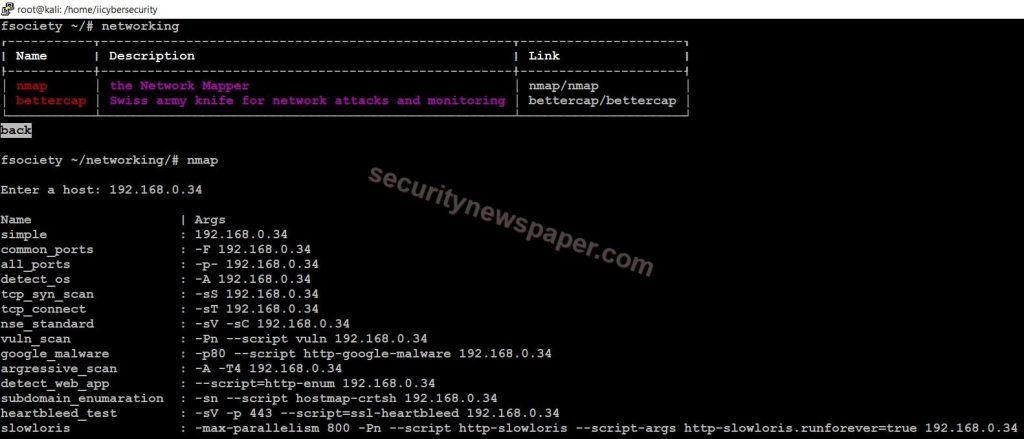
- Here, we have to select the option for scanning the target.
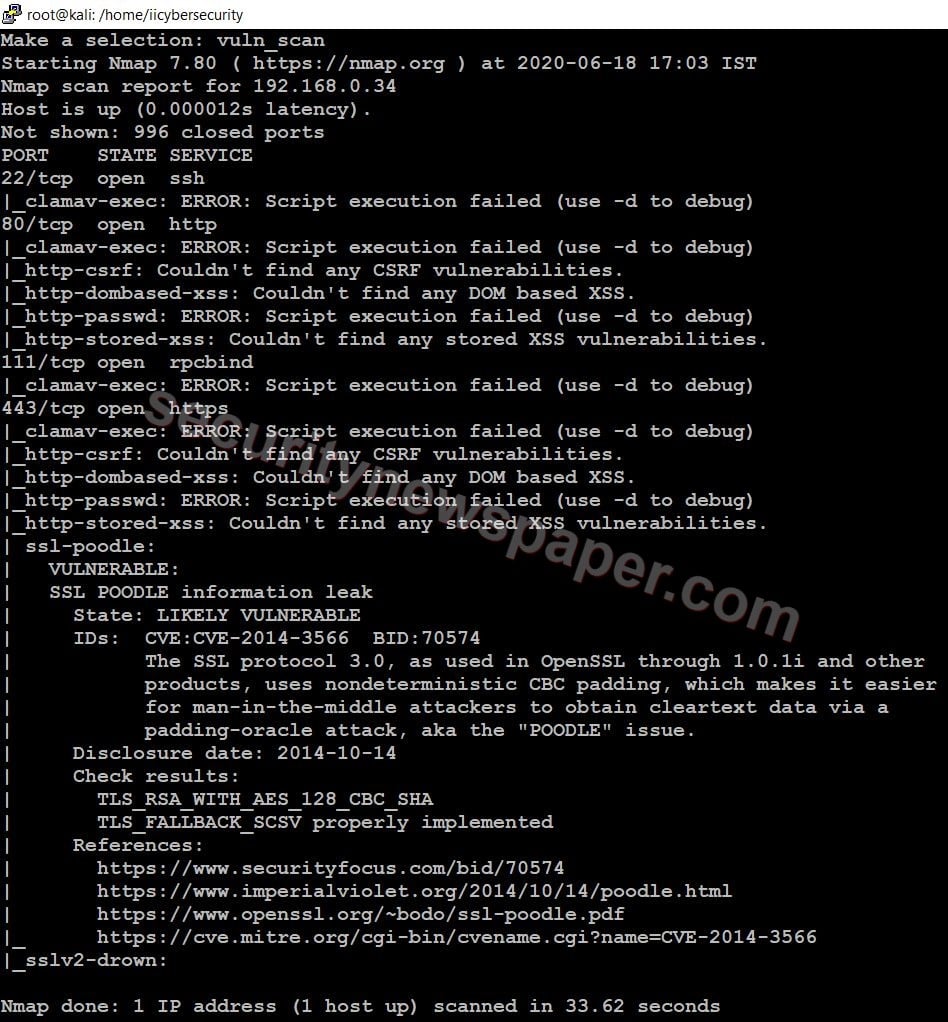
- In the results, we found open ports and vulnerability on the target machine.
- CVE-2014-3566: The OpenSSL uses SSL Protocol 3.0 through 1.0.1i and other products use nondeterministic CBC padding, so this make it easy to perform a man in the middle attack. Using a padding-oracle attack, hackers can gain plain text data.
- As Nmap is very noisy, you can also create your custom scripts like ethical hacking researchers of International Institute of Cyber Security to perform initial level of Pentesting.
Bettercap: Bettercap is a powerful hacking tool. using this we can perform a man in the middle attack via HTTP, HTTPS, and TCP. Through this hacker can monitor the real-time traffic and can steal any login credentials & other sensitive data.
Web Apps
- XSStrike: We use this for information gathering and it can also find vulnerabilities like DOM and XSS on the webpage.
- Photon: Photon is used to crawl the website and it can collect the URLs with the parameters. This tool is completely built on python language.
Passwords
Cupp: Cupp hacking tool is used to crack the username and password of any webpage using a wordlist.
- Next, use this command cupp to launch the tool
- Now, enter the details about the victim to create a password list.
- After providing the details, the tool will generate the password list
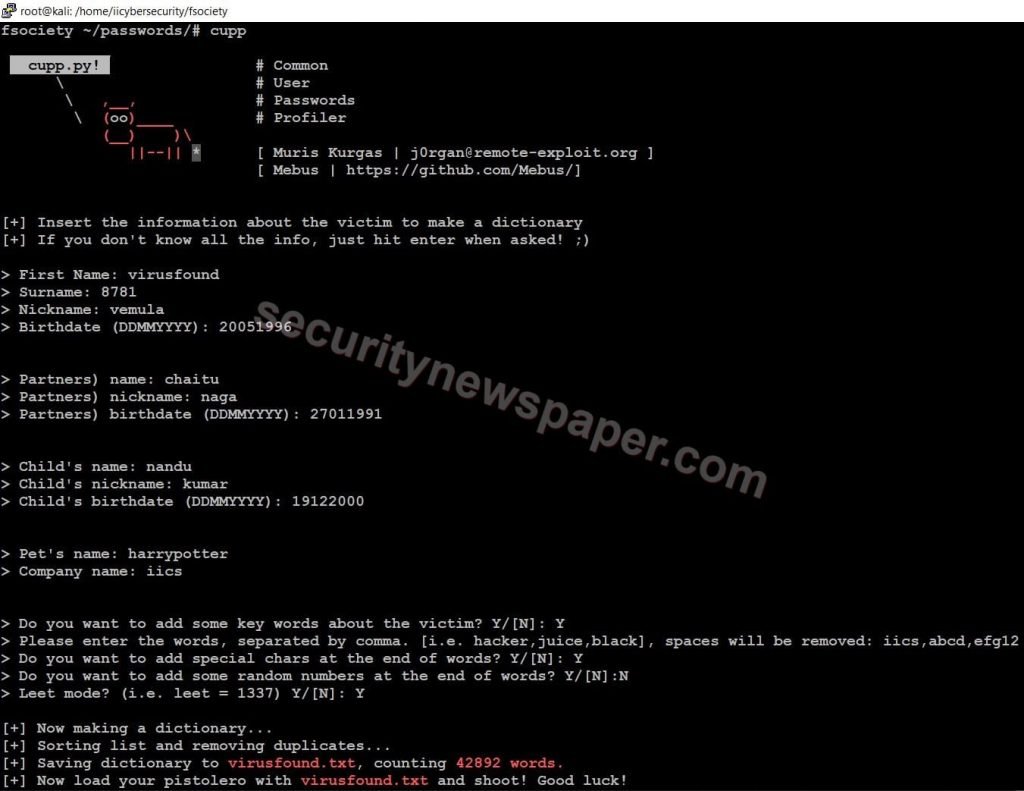
- Here, we go 42892 word and as virusfound.txt
- cr3dov3r: cr3dov3r is an open-source tool. we use this tool, to finding the login credential of a specific email address. cr3dov3r uses haveibeenpwned API key to check the leaks of the provided email address. This try’s login attempts to some websites like google, Github, eBay, Facebook, Twitter, etc.
- Hash Buster: Hash Buster is used to converting hash function to plain text.
obfuscation
Cuteit: The main aim of this tool is to make malicious IP address into URL. This tool builds on the python language.
- Type this command obfuscation to select the module and type cuteit to launch the tool.
- After using cuteit command, choose option y (YES) to clone the tool.
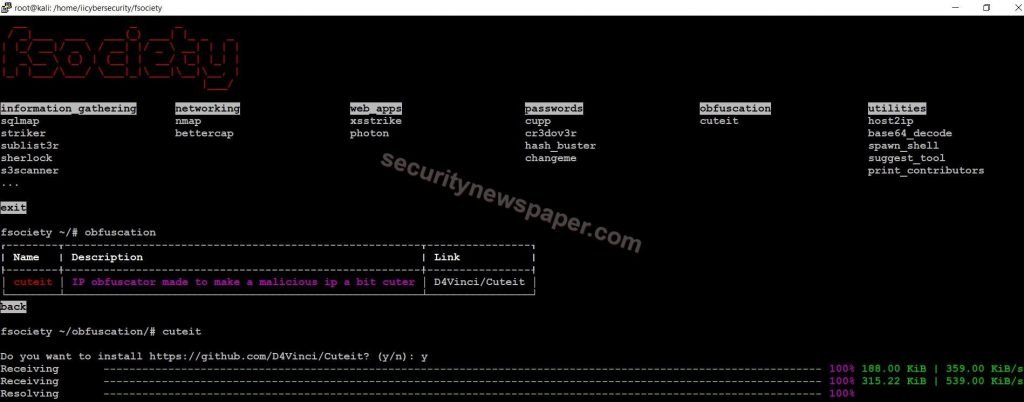
- Here, the tool is successfully installed. Then we have to enter the Malicious IP address to convert into URLs
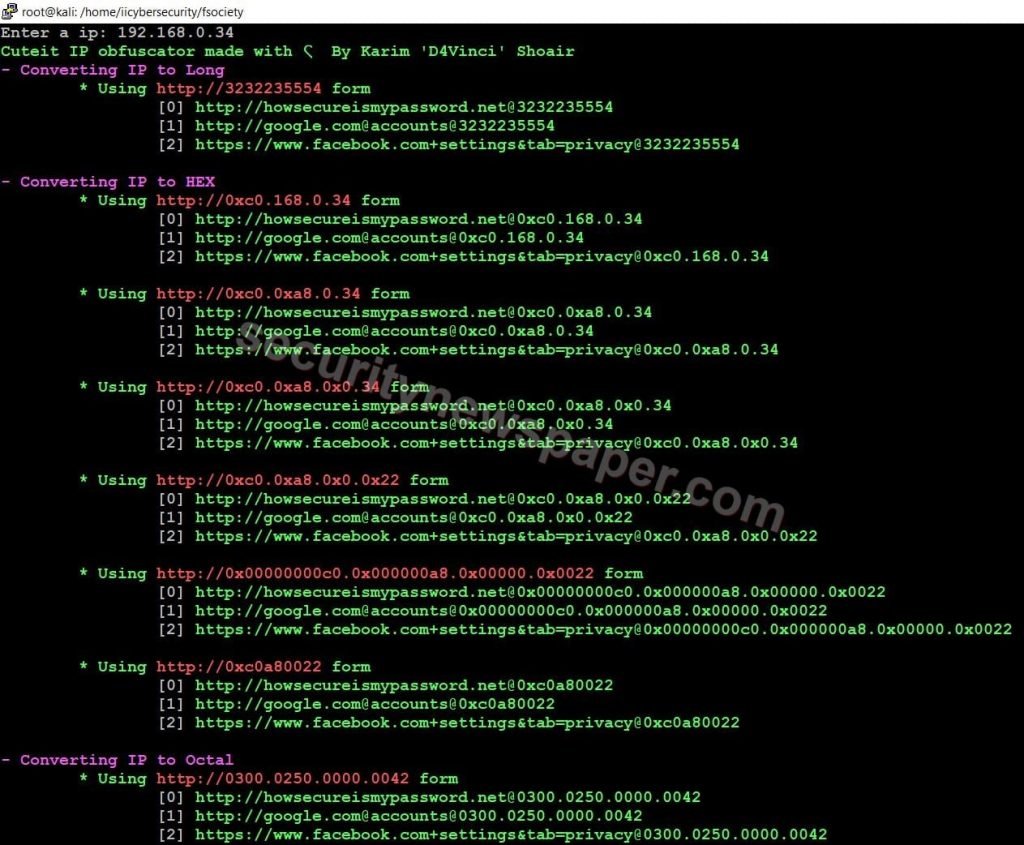
- Successfully we got the URLs
Utilities
Host To IP: As we know every website has an IP address. This tool displays the Host’s IP address by specifying the hostname.
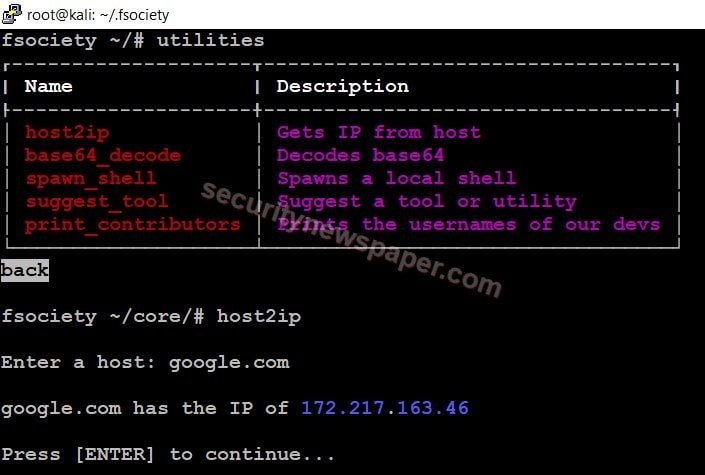
- Here, we got google’s IP address.
- Base64 Becode: It decode’s base64
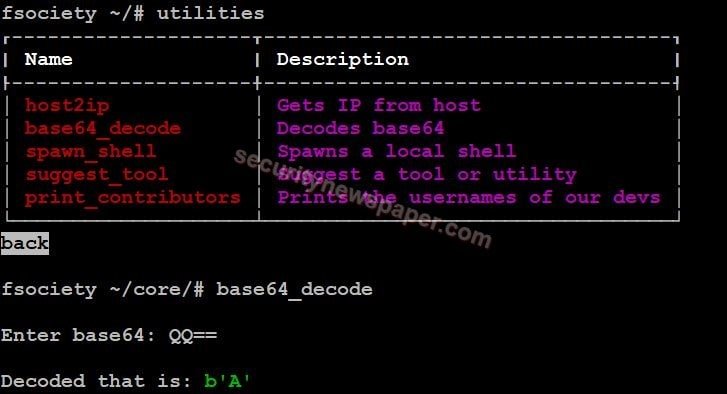
- Successfully we decoded it.
Conclusion
Here, we saw all the penetration testing module with different tool. Its easy for pentesters to perform their job with ease.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











