A few days ago, it was reported the discovery of a vulnerability in PAN-OS, the operating system used by Palo Alto Networks firewall and virtual private network (VPN) solutions. Today, security testing course experts and the U.S. Cyber Command mentioned that hacker groups sponsored by State actors are highly likely to exploit this flaw as part of high-profile attack campaigns.
Via Twitter, the Cyber Command urged users of this technology to install the updates: “Please apply the patches to all devices affected by CVE-2020-2021 immediately; ATP groups could exploit this vulnerability.” It should be remembered that Advanced Persistent Threat (APT) is a term used by the cybersecurity community to refer to hacking groups sponsored by other governments.
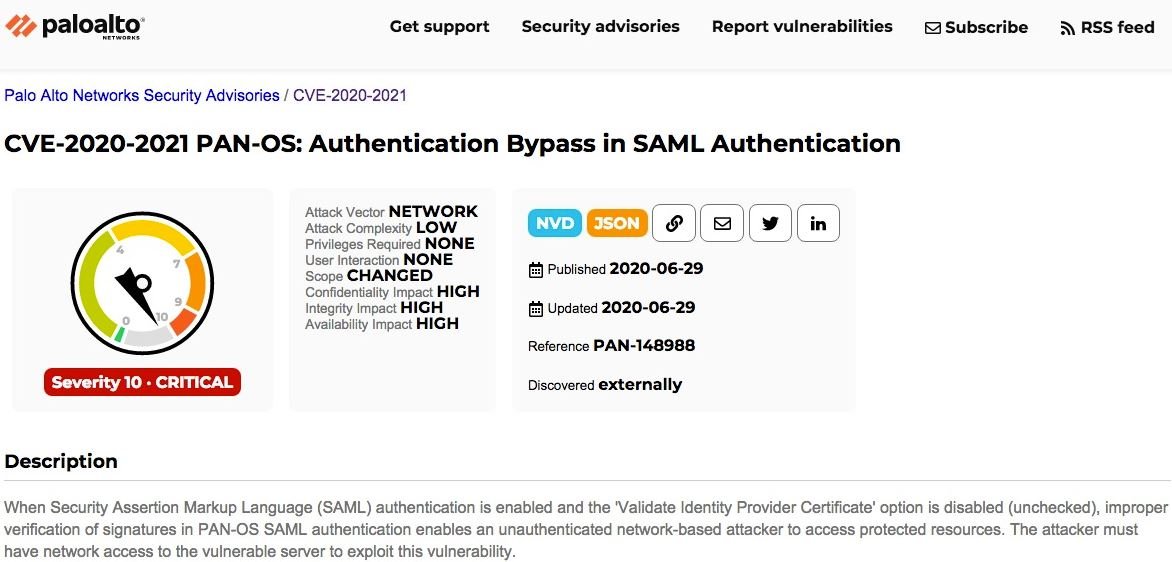
Security testing course experts believe this fear is completely justified, as this flaw received a score of 10/10 according to the Common Vulnerability Scoring System (CVSS), meaning it is easy to exploit and requires minimal victim interaction. The potential attacker doesn’t even require prior access to the affected device.
With regard to the technical aspects of the vulnerability, it allows hackers to bypass the authentication mechanisms of the affected systems, allowing threat actors to access vulnerable devices without the need for legitimate login credentials.
Thanks to this vulnerability, attackers could modify PAN-OS settings, allowing you to disable the firewall or modify VPN controls, exposing user information. For the attack to be successful PAN-OS must have specific configurations; for example, the flaw is exploitable only if the ‘Validate Identity Provider Certificate’ option is disabled and if the SAML (Security Assertion Markup Language) option is enabled, security testing course specialists mentioned.
Potentially vulnerable products include:
- GlobalProtect Gateway
- GlobalProtect Portal
- GlobalProtect Clientless VPN
- Authentication & Captive Portal
- Next-generation PAN-OS firewall
- Prisma Access Systems
Although the settings required by the attack are not enabled (or disabled, as the case may be) by default, some vendor manuals instruct PAN-OS owners to modify these settings in particular cases, which could increase the scope of the attack.
In addition to the Cyber Command, multiple members of the cybersecurity community have asked users of affected deployments to install updates to prevent a potential mass exploitation campaign.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











