Computer forensics specialists have detected the presence of multiple apocryphal tools and websites for downloading browsers in multiple countries, used to deploy dangerous variants of malware that could record all the activities of victims through the webcam.
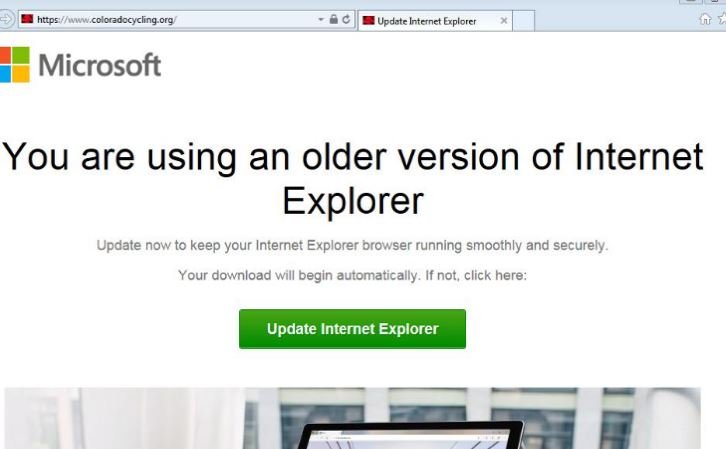
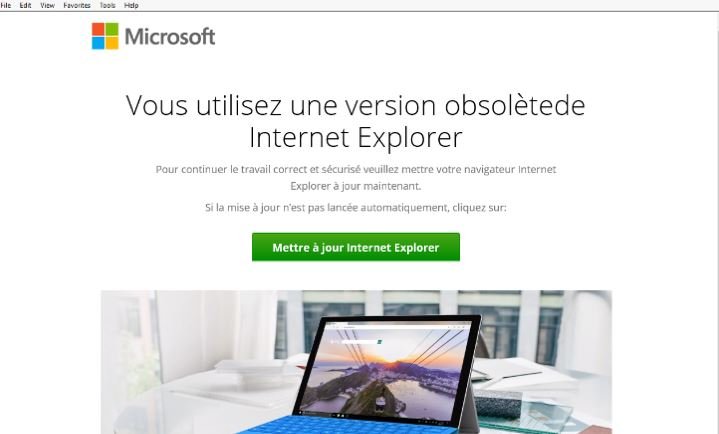
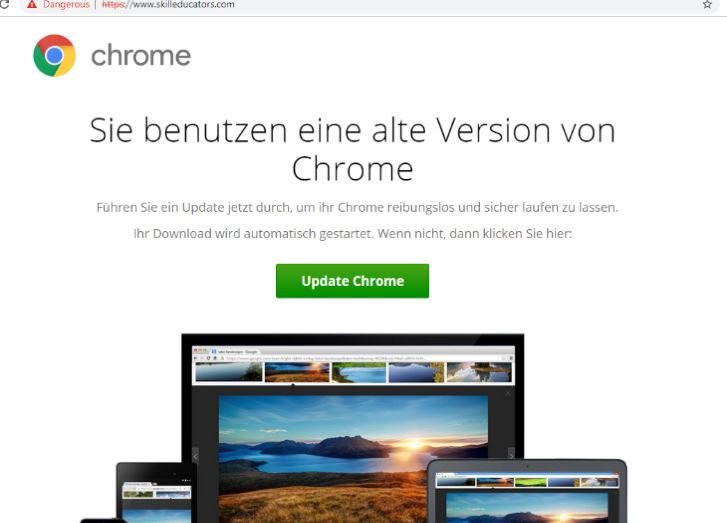
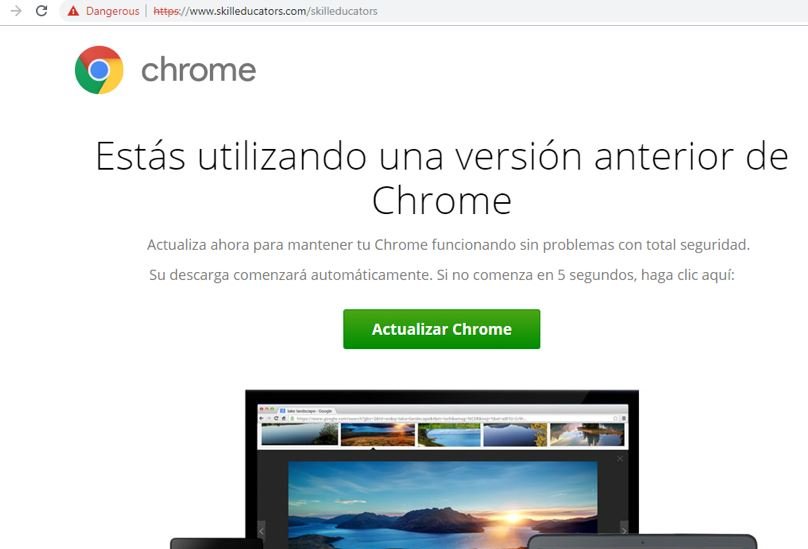
According to reports, the malware used by hackers is located in the links for downloading a browser update (Chrome, Internet Explorer, among others), although you can also find these links attached to emails. Although this technique, known as “fake downloader”, is not new, it is highly effective.
Researchers at Proofpoint recently detected a fake downloader campaign apparently perpetrated by threat actors from the TA569 group (also known as SocGholish).
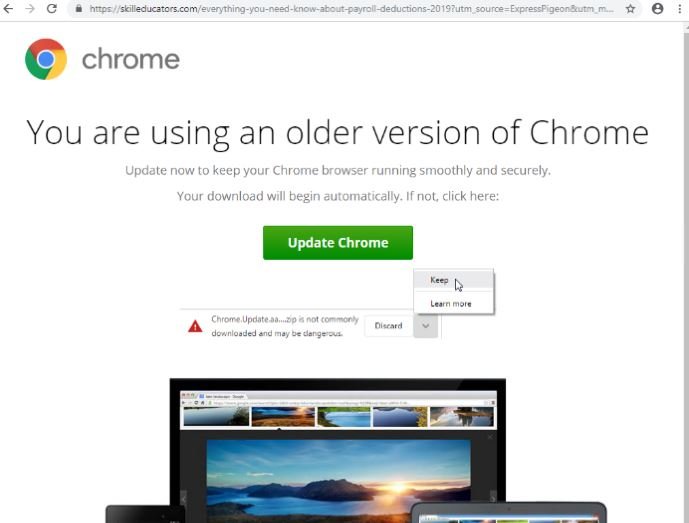
According to computer forensics specialists, the attack begins by analyzing the location, version of the operating system and browser used by potential victims. If their computer meets the ideal features for the attack, users start receiving emails or links to redirect them to the fake update page.
Once on the malicious website, the criminals try to convince users to click a button or download a JavaScript or HTA file to protect their computers. If the victims fall into the trap, a script is initiated that will record the affected system information and begin the second stage of the attack, which includes infection by a banking Trojan (Chthonic) and a remote access software known as NetSupport, a legitimate tool that is abused for malicious purposes.
Perpetrators attack all kinds of targets, whether individual users, organizations, public institutions, private companies, members of the academic sector, among others.
As mentioned above, this is not a new practice, and while it should be a widely known attack variant, millions of users are unaware that hackers can take advantage of updates from legitimate companies. In addition, computer forensics experts always recommend that users keep their software up to date, so this security measure is also affected by criminals.
For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.