Introduction
D-tect is an information gathering tool, we use this tool in first stage of penetration testing for web applications. Using this tool, we can fetch out web application username, sensitive data detection, sub-domain scanner, port scanning, wordpress scanner, vulnerabilities using XSS (Cross-site scripting), SQL injection and wordpress backup Grabber.
Installation
- Use this tutorial to install the complete hacking tool in your kali machine.
Execution Steps
- Use this command to launch the tool. python d-tect.py
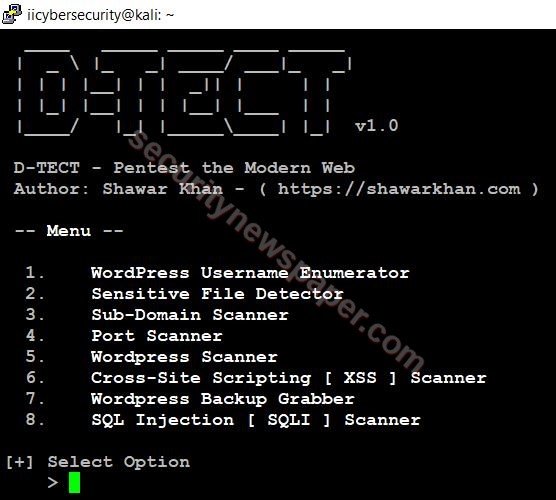
- Successfully launched the tool.
User Name Enumeration: Now, this option will find out valid username of wordpress for targeted website. In the same way it will identifies the IP address and the server name.
- Choose option 1 and enter the target website.
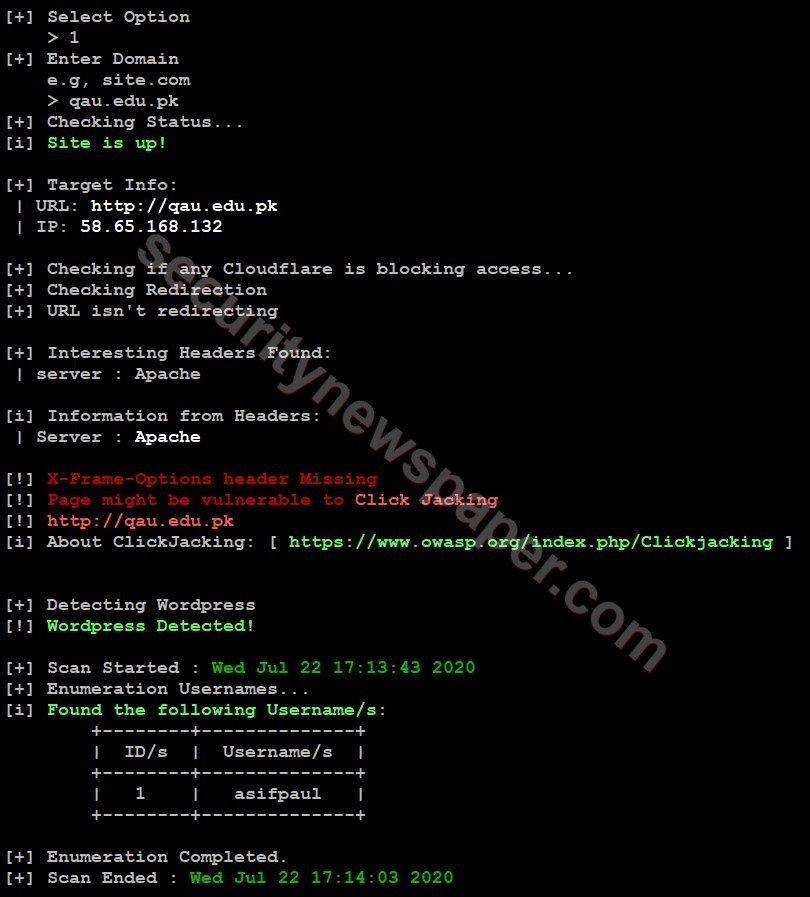
- Successfully got the username.
Sensitive File Detector: This option will find out the sensitive data on the targeted website.
- Choose option 2
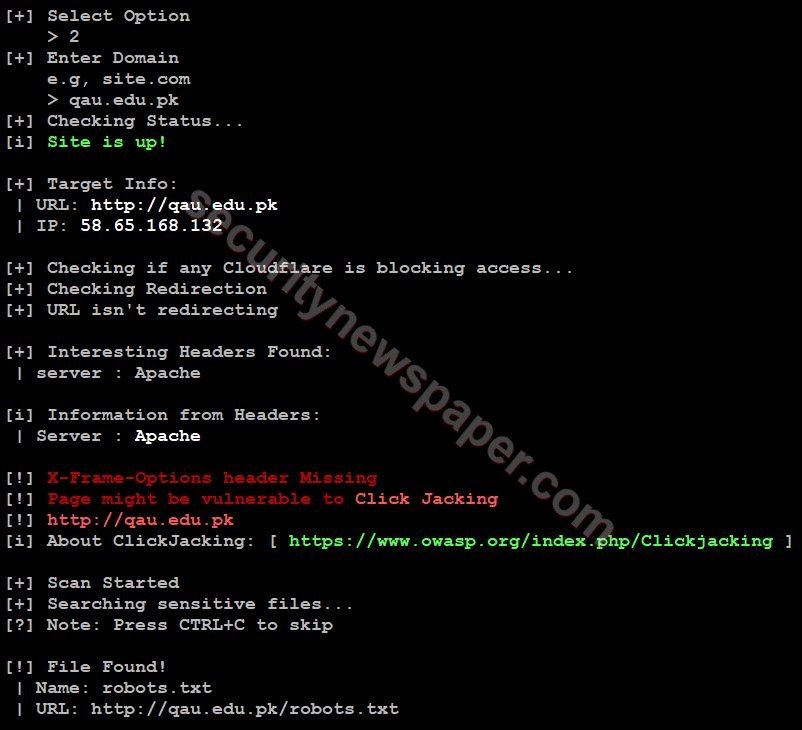
- Successfully got the sensitive file.
- Now, lets open this file in the browser. To view the data.
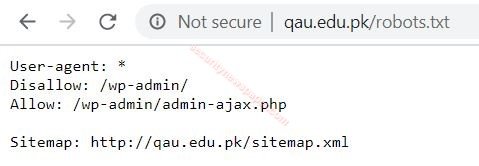
Open this sitemap URL in the browser to view the data.
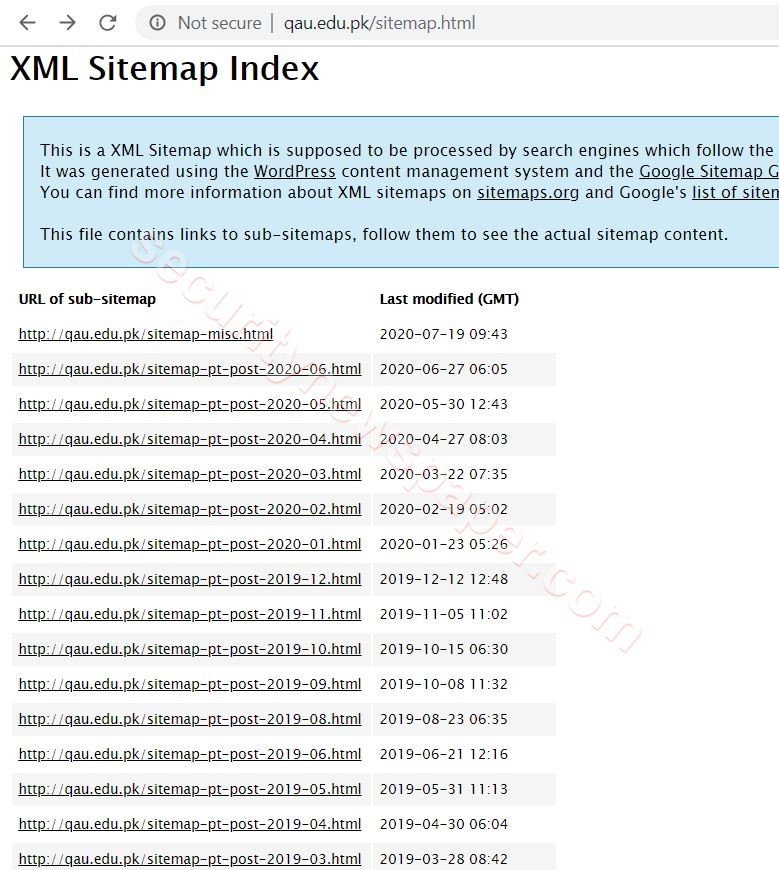
- Here, we got the HTML URLS of target website.
Sub-Domain Scanner: This option will list out all the subdomains with IP address and server name of the target website.
- Choose option 3
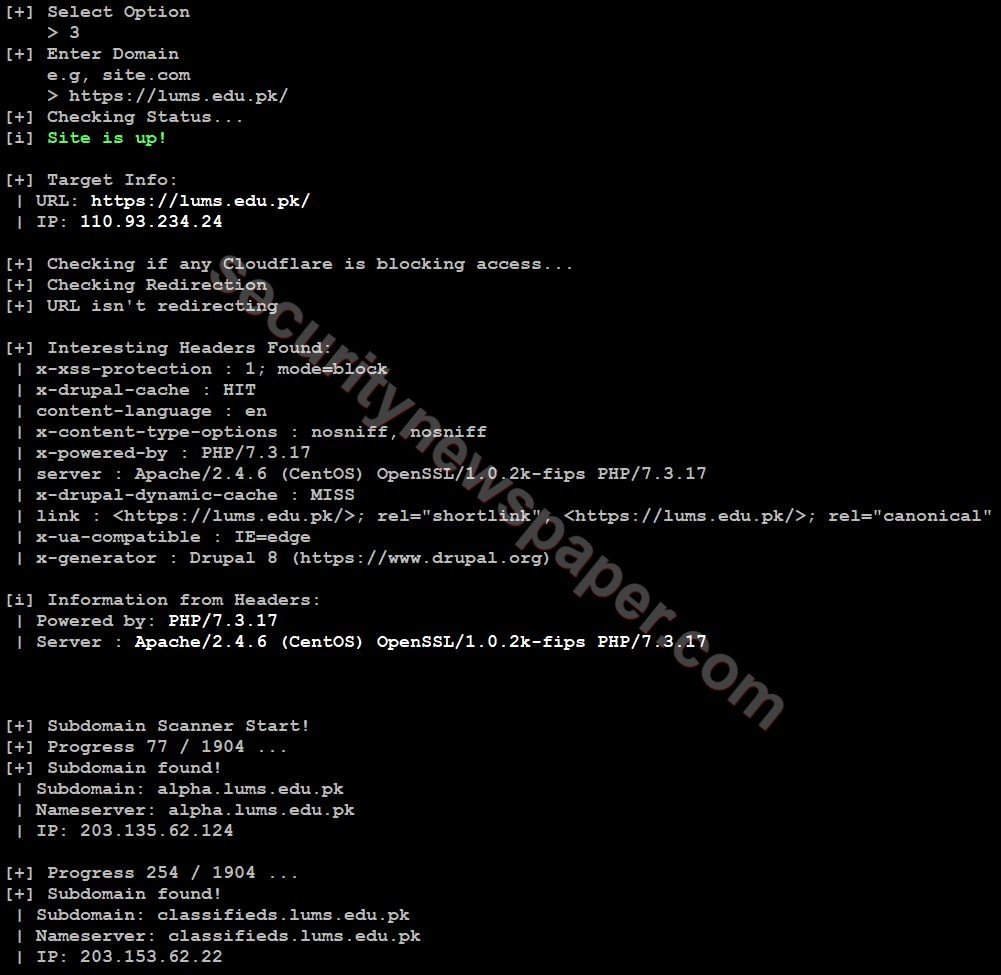
- Successfully we got the subdomain details.
Port Scanner: This option will list out the open ports on the target website.
- Enter the target website and port range.
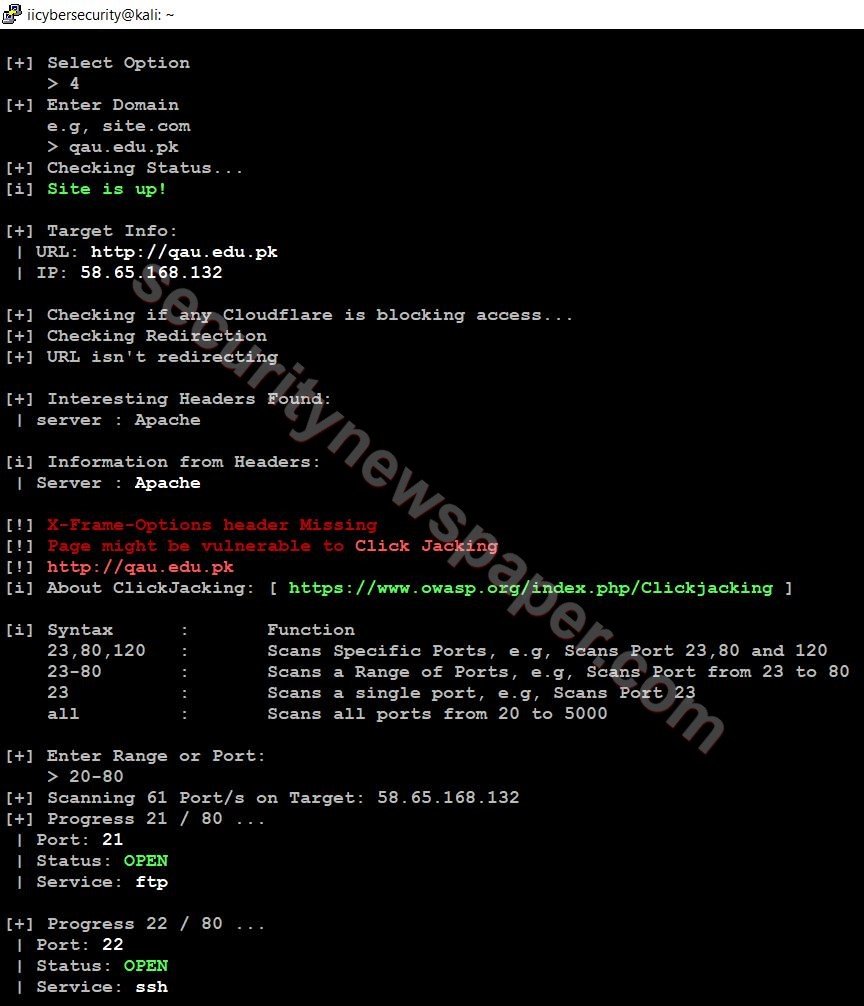
- Successfully got the open port and services.
Conclusion
As we saw D-tect tool can fetch out confidential details of the web application and help us find out the vulnerabilities on the target web application.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











