A couple of malware reverse engineering teams have revealed multiple problems in the Android drone control app developed by Chinese manufacturer Da Jiang Innovations (DJI). It appears that exploiting these flaws can be used to bypass Google Play Store controls and install malicious content, as well as extract sensitive information to send to the company’s servers.
The reports, submitted by Synacktiv and GRIMM firms, mention that the Go 4 app requests overly invasive permissions and collects personal data such as IMSI, IMEI and SIM card number. In addition, the app contains anti-debug and encryption code, which prevents proper security analysis, similar to C&C servers in malware attacks.
“Thanks to the high permissions your app requests, the company has almost complete control over the affected devices,” the malware reverse engineering experts mention. It should be noted that these unsafe features are not present in the version of this app for iOS systems.
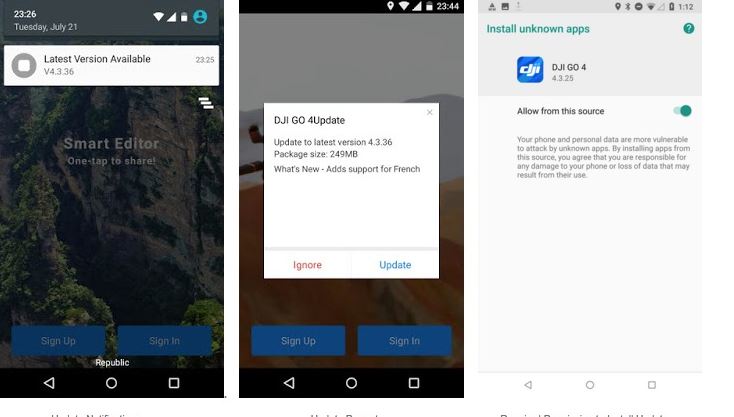
On the other hand, the second report mentions that, after reverse engineering the app, a URL (hxxps: //service-adhoc.dji.com/app/upgrade/public/check) used to download an update that allows unauthorized applications to be installed was discovered.
In the update, experts modified this request to trigger a forced update of an arbitrary application, allowing the installation of untrusted applications, and then block the use of the application until the update is installed.
This is not only a breach of Google Play Store policies, but also involves severe security issues, as threat actors could compromise update services to install malware on affected devices.
In addition to this, malware reverse engineering experts discovered that the app leverages the MobTech SDK to pass metadata over the phone, including screen size, brightness, WLAN address, MAC address, BSSIDs, Bluetooth addresses, among others.
DJI is the world’s largest manufacturer of commercial drones and has faced strict scrutiny from the U.S. Department of the Interior, in conjunction with other Chinese technology companies. For further reports on vulnerabilities, exploits, malware variants and computer security risks, it is recommended to enter the website of the International Institute of Cyber Security (IICS), as well as the official platforms of technology companies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











