Introduction
Now you can create your own tunnel to hide your IP address. The gtunnel tool creates an exe file based on an operating system like Windows/Linux, this exe file creates a connection directly to the server by using the tunneling process. This tunnel is very secure to communicate between source and destination systems.
Environment
- OS: Kali Linux 2020 64 bit or it can be your public server to hide your IP.
- Kernel version: 5.6.0
Installation Steps
- Use this command to clone the project.
- git clone https://github.com/hotnops/gtunnel
root@kali:/home/iicybersecurity# git clone https://github.com/hotnops/gtunnel Cloning into 'gtunnel'... remote: Enumerating objects: 186, done. remote: Counting objects: 100% (186/186), done. remote: Compressing objects: 100% (104/104), done. remote: Total 186 (delta 85), reused 159 (delta 63), pack-reused 0 Receiving objects: 100% (186/186), 12.62 MiB | 2.19 MiB/s, done. Resolving deltas: 100% (85/85), done.
- Use the cd command to enter into gtunnel directory.
root@kali:/home/iicybersecurity# cd gtunnel/ root@kali:/home/iicybersecurity/gtunnel#
- Next, install docker in our machine by using this command sudo apt install docker.io
root@kali:/home/iicybersecurity/gtunnel# sudo apt install docker.io Reading package lists... Done Building dependency tree Reading state information... Done The following additional packages will be installed: cgroupfs-mount libintl-perl libintl-xs-perl libmodule-find-perl libmodule-scandeps-perl libproc-processtable-perl libsort-naturally-perl needrestart runc tini Suggested packages: ==================================================================================================SNIP================================================================================================================================ Created symlink /etc/systemd/system/sockets.target.wants/docker.socket → /lib/systemd/system/docker.socket. Setting up libintl-xs-perl (1.26-2+b5) ... Processing triggers for systemd (245.6-2) ... Processing triggers for man-db (2.9.3-2) ... Processing triggers for kali-menu (2020.3.2) ...
- After installing the docker, use this command to download the gtunnel image file using docker and start the server.
root@kali:/home/iicybersecurity/gtunnel# ./start_server.sh Sending build context to Docker daemon 13.36MB Step 1/20 : FROM golang:1.14 1.14: Pulling from library/golang d6ff36c9ec48: Pull complete c958d65b3090: Pull complete edaf0a6b092f: Pull complete 80931cf68816: Pull complete 813643441356: Pull complete a54c81388677: Pull complete 31748c757dd4: Pull complete ===================================================================================================SNIP================================================================================================================================ Removing intermediate container 923d00e6148a ---> 1a1372d230ae Step 20/20 : CMD ["go", "run", "gServer/gServer.go"] ---> Running in d2a945bbc462 Removing intermediate container d2a945bbc462 ---> acc9e3cb6086 Successfully built acc9e3cb6086 Successfully tagged gtunnel-server:latest
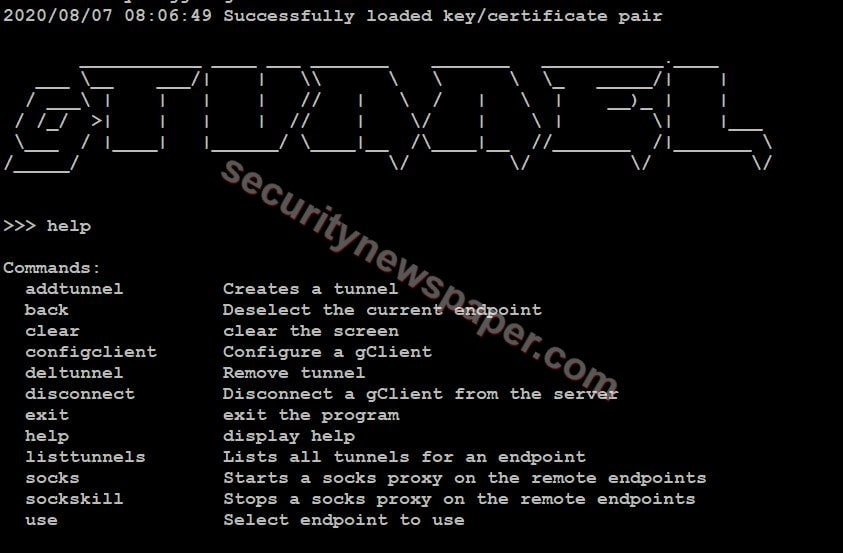
- Here, we have few help options.
- Now, use this command to configure the client configclient <OS> <server’s IP> <Port> <File name>
- configclient win 192.168.0.28 443 iics1
>>> configclient win 192.168.0.28 443 iics1 >>>
- Generated exe file will be stored in the configured directory. Use cd command to move into the configured directory and send the exe file to the client machine.
- When the client run’s the exe file tunnel will be established to the server machine.
>>> configclient win 192.168.0.28 443 iics1 >>> 2020/08/07 11:46:26 Endpoint connected: id: iics1
- Now, type “use” command to connect to the end point.
>>> use iics1 (iics1) >>>
- Now add tunnel to forward the traffic through server IP by using this command.
- addtunnel remote <listener Port> <destination IP> <destination port> <file name>
- Verify the tunnel added by using this command “listtunnels”
(iics1) >>> listtunnels Tunnel ID: iics
- Now, if we browser in our search engine, the traffic will travel from server IP. For this we can capture the traffic through Wireshark.
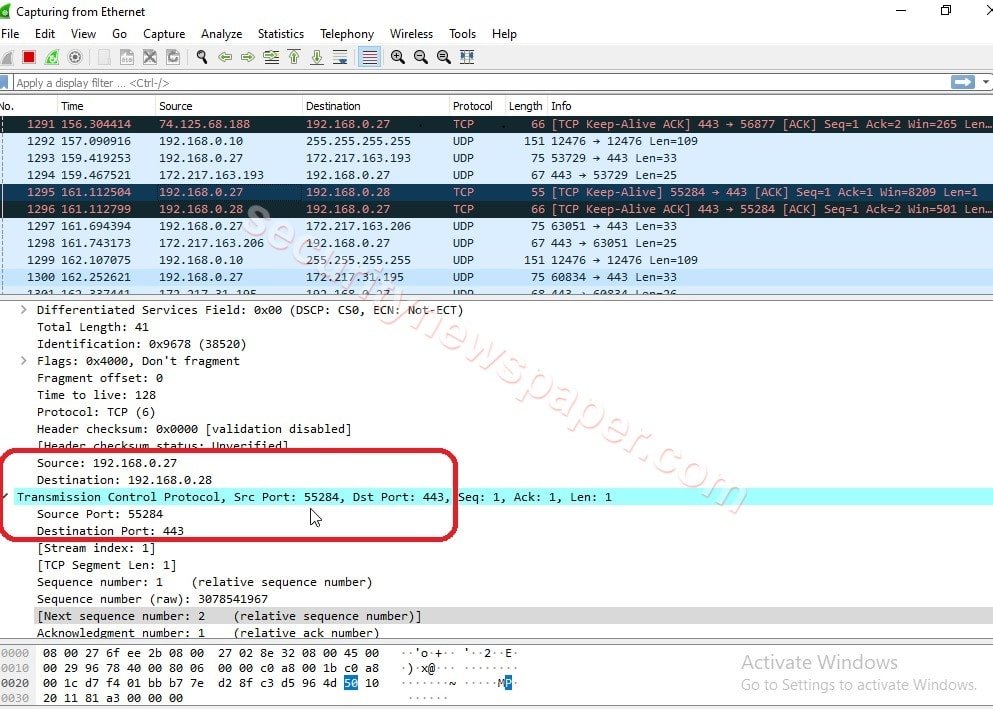
- In the above picture, we see the packet travelling through server IP Address.
Conclusion
We saw on how to make a secure connection between server and client for communicating with each other using tunneling process.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











