Introduction
HoneyPot is always a great way to fool hackers. There are many types of HoneyPot system, some are used to detect, deflect, or even counteract the hackers. Today we will talk about cross platform honeypot which can be used for enterprise information security. HFish is such a HoneyPot tool, using this tool we can detect the attacks in our networks and further analyze them. Earlier researchers of International Institute of Cyber Security demonstrated other ways to setup your own HoneyPot.
When we use this honeypot tool, it fools hackers by creating lucrative system for attack. If an hacker tries to hack the target, this honeypot tool captures the behavior of the attack and we can keep an eye on how hackers are targeting network with a vulnerabilities. Most of the organizations can use this tool, to find out the vulnerabilities through hackers.
Environment
- OS: Kali Linux 2020 64 bit
- Kernel-Version: 5.6.0
Installation Steps
- Use this command to download the zip file.
- wget https://github.com/hacklcx/HFish/releases/download/0.6.2/HFish-0.6.2-linux-amd64.tar.gz
root@kali:/home/iicybersecurity# wget https://github.com/hacklcx/HFish/releases/download/0.6.2/HFish-0.6.2-linux-amd64.tar.gz --2020-08-10 11:56:57-- https://github.com/hacklcx/HFish/releases/download/0.6.2/HFish-0.6.2-linux-amd64.tar.gz Resolving github.com (github.com)... 13.234.176.1Connecting to github.com (github.com)|13.234.176.102|:443... connected. HTTP request sent, awaiting response... 302 Found Location: https://github-production-release-asset-2e65be.s3.amazonaws.com/200975456/9c185400-93c2-11ea-8dc1-d10d40722273?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20200810%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20200810T062807Z&X-Amz-Expires=300&X-Amz-Signature=dc78f11c2df45725666df3a72887142882746fd80e7660258ee9c4102f09adaa&X-Amz-SignedHeaders=host&actor_id=0&repo_id=200975456&response-content-disposition=attachment%3B%20filename%3DHFish-0.6.2-linux-amd64.tar.gz&response-content-type=application%2Foctet-stream [following] --2020-08-10 11:57:12-- https://github-production-release-asset-2e65be.s3.amazonaws.com/200975456/9c185400-93c2-11ea-8dc1-d10d40722273?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20200810%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20200810T062807Z&X-Amz-Expires=300&X-Amz-Signature=dc78f11c2df45725666df3a72887142882746fd80e7660258ee9c4102f09adaa&X-Amz-SignedHeaders=host&actor_id=0&repo_id=200975456&response-content-disposition=attachment%3B%20filename%3DHFish-0.6.2-linux-amd64.tar.gz&response-content-type=application%2Foctet-stream Resolving github-production-release-asset-2e65be.s3.amazonaws.com (github-production-release-asset-2e65be.s3.amazonaws.com)... 52.216.185.27 Connecting to github-production-release-asset-2e65be.s3.amazonaws.com (github-production-release-asset-2e65be.s3.amazonaws.com)|52.216.185.27|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 14575783 (14M) [application/octet-stream] Saving to: ‘HFish-0.6.2-linux-amd64.tar.gz’ HFish-0.6.2-linux-amd64.tar.gz 100%[========================================================================================>] 13.90M 3.64MB/s in 5.0s 2020-08-10 11:57:18 (2.78 MB/s) - ‘HFish-0.6.2-linux-amd64.tar.gz’ saved [14575783/14575783]
- Next, use this command to extract the zip file tar -zvfx <file name>
root@kali:/home/iicybersecurity# tar -zvxf HFish-0.6.2-linux-amd64.tar.gz HFish-0.6.2-linux-amd64/ HFish-0.6.2-linux-amd64/LICENSE HFish-0.6.2-linux-amd64/web/ HFish-0.6.2-linux-amd64/web/wordPress/ HFish-0.6.2-linux-amd64/web/wordPress/html/ HFish-0.6.2-linux-amd64/web/wordPress/html/index.html HFish-0.6.2-linux-amd64/web/wordPress/static/ HFish-0.6.2-linux-amd64/web/wordPress/static/forms.min.css HFish-0.6.2-linux-amd64/web/wordPress/static/buttons.min.css ==================================================================================================SNIP================================================================================================================================= HFish-0.6.2-linux-amd64/static/data/img/bg01.png HFish-0.6.2-linux-amd64/static/data/img/thumb.jpg HFish-0.6.2-linux-amd64/HFish HFish-0.6.2-linux-amd64/db/ HFish-0.6.2-linux-amd64/db/hfish.db HFish-0.6.2-linux-amd64/db/ipip.ipdb HFish-0.6.2-linux-amd64/db/sql/ HFish-0.6.2-linux-amd64/db/sql/hfish_db.sql
- Use cd command to enter into HFish directory.
root@kali:/home/iicybersecurity/HFish# cd .. root@kali:/home/iicybersecurity# cd HFish
- Now, use this command to run the tool, ./HFish run
root@kali:/home/iicybersecurity/HFish-0.6.2-linux-amd64# ./HFish run [GIN-debug] [WARNING] Running in "debug" mode. Switch to "release" mode in production. - using env: export GIN_MODE=release - using code: gin.SetMode(gin.ReleaseMode) [GIN-debug] Loaded HTML Templates (2): - - index.html =================================================================================================SNIP=============================================================================================================================== [GIN-debug] POST /post/setting/updateWhiteIp --> HFish/view/setting.UpdateWhiteIp (7 handlers) [GIN-debug] POST /post/setting/updatePasswdTM --> HFish/view/setting.UpdatePasswdTM (7 handlers) [GIN-debug] POST /post/setting/clearData --> HFish/view/setting.ClearData (7 handlers) [GIN-debug] GET /api/v1/get/ip --> HFish/view/api.GetIpList (7 handlers) [GIN-debug] GET /api/v1/get/fish_info --> HFish/view/api.GetFishInfo (7 handlers) [GIN-debug] GET /api/v1/get/passwd_list --> HFish/view/api.GetAccountPasswdInfo (7 handlers) pid is 32482020/08/10 11:58:16 Listening on [::]:5900
- Next open this URL in our browser <SERVER-IP:9001>
- Successfully we got the login page.
- Now, enter admin as username and password to login.
- HFish tool displays the attacks in two different ways
- Numbers
- Graph (Last 24 Hours)
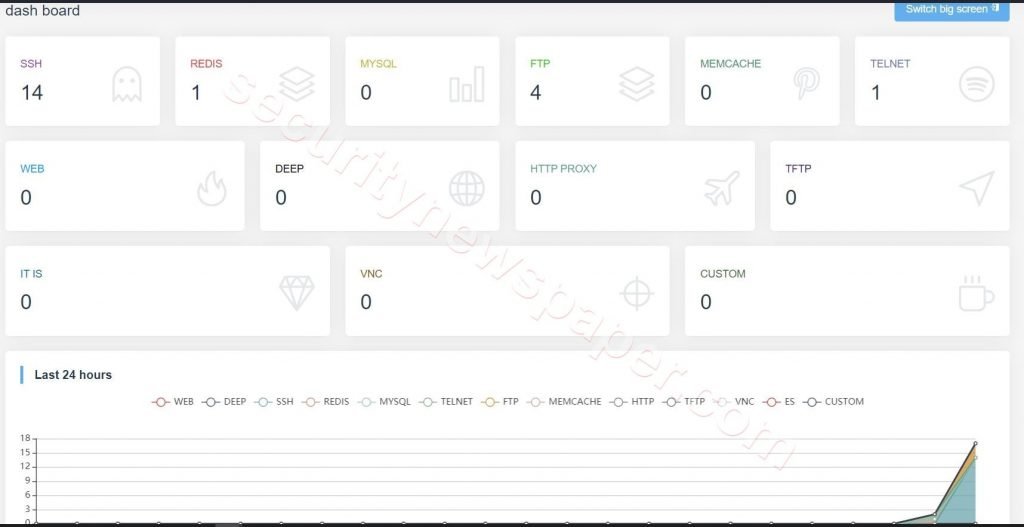
- As we can see some counters in services like SSH, Redis, Telnet. Here, all these counters incremented when somebody tries to hack into the HoneyPot system.
- Now lets try to replicate a scenario by trying to hack into HoneyPot server.
- Imagine a hacker who is tying to scan servers in your network, and finds a server with services like SSH, Telnet, FTP open. Hacker will first try to brute force the services running on server.
- To brute force we will simply do telnet, ftp to vulnerable/honeypot IP address. Open cmd in windows and run:
- telnet 192.168.1.5
- FTP 192.168.1.5
- Once somebody try to access open services, counter of the services on HoneyPot will increase.
- In the same way, we also get logs in the terminal.
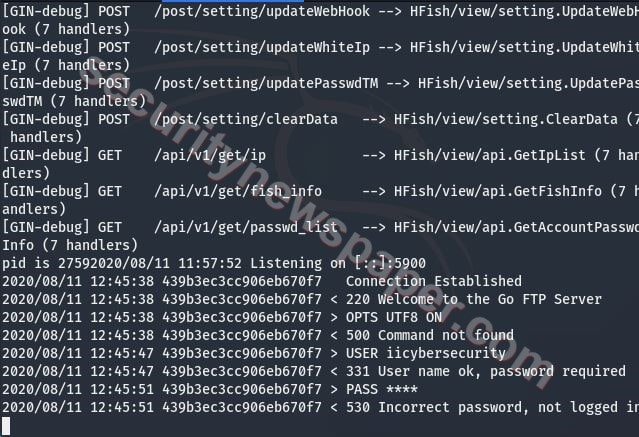
- Services status: Here, we can see the attack details
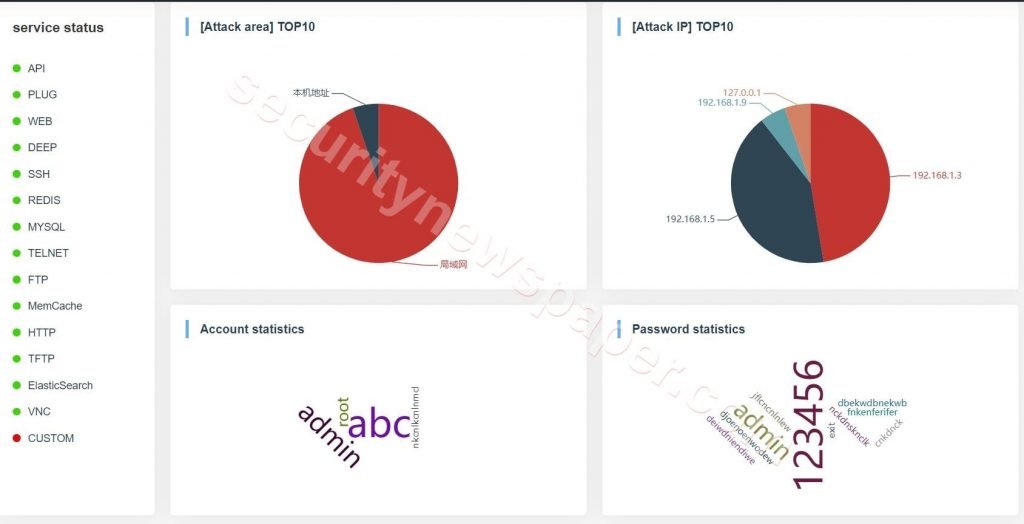
- In the status of the service, we have 4 different boxes
- Attack Area: Here, it displays the attack area. So we have to imagine there is a vulnerability
- Attack IP: Here, It shows the hacker’s IP address.
- Account Statistics: Here, it shows the account’s user name, which hackers used.
- Password Statistics: Here, it shows the passwords that hackers used.
- We can view this data in big screen also
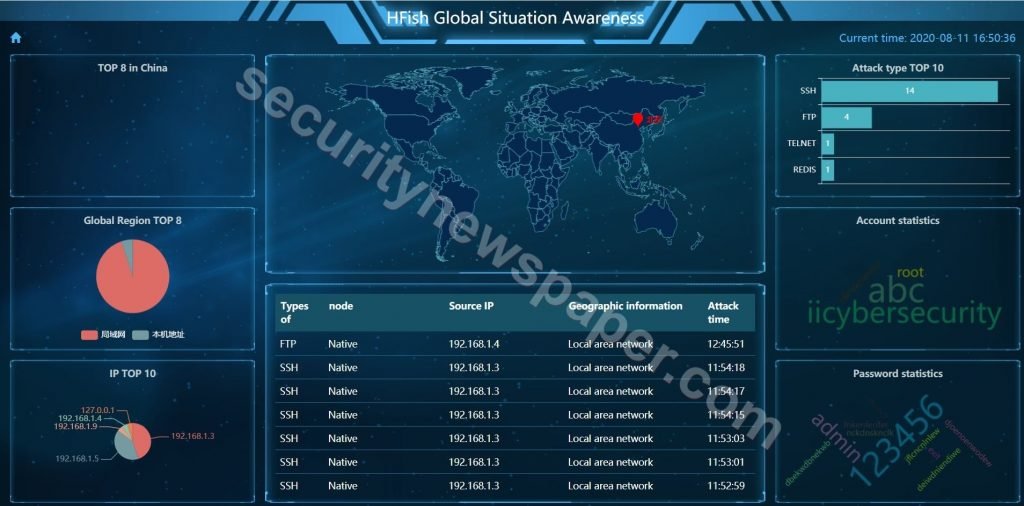
Conclusion
As we saw on how we can detected the attacks using HFish (Honeypot). Most of the organizations use this tool, to make hackers fool and find out vulnerabilities in the network.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











