The most dangerous malware variants are those that receive constant updates, improving their capabilities to compromise attacked systems, as mentioned by experts from a computer security course. Mimikatz is an open source post-exploit tool used in Windows credential-based attacks. A couple of years ago its developers included DCShadow, a feature of the lsadump module that allows threat actors to gain persistent privileged access in Windows Server Active Directory (AD), as well as cover traces of the attack.
AD attacks are very common, as AD controls security on most systems where it is deployed. When malicious hackers gain privileged access to AD, they can also compromise servers and devices joined to the AD domain.
When it comes to DCShadow attacks, any Windows device joined to the AD domain is registered as a domain controller (DC) by creating two new objects in the domain configuration partition. This attack can be performed from Windows 10 and, although Windows 10 cannot be a DC, DCShadow tricks the AD implementation into thinking that Windows 10 is actually a DC, the experts of the computer security course mention.
While these attacks are a growing trend in the cybercrime world, it is possible to implement some measures to prevent them. Security firm Petri researchers mention that the best way to prevent these attacks is to prevent malicious hackers from gaining privileged access to the target system, which is possible by some methods described below.
Workstations with privileged access
It is highly recommended that you use only domain administrator credentials (and other high-privileged accounts) on workstations with the necessary security measures. These Privileged Access Workstations (PAWs) are isolated from the public Internet.
Delegation of privileges for minor tasks
User and group management can be easily performed by other users besides the administrator; the best thing is that it is not necessary to grant privileged access to the domain, according to experts in the IT security course.
Protecting accounts with Windows tools
Credential Guard, a Windows Defender tool, provides additional protection for domain accounts, isolating credentials in an area that the system kernel cannot access. Other tools such as Credential Guard require a device to support virtualization-based security (VBS).
Privileged identity
A privileged identity management (PIM) solution can help organizations monitor and control privileged access to AD. Windows Server 2016 Shadow Directors and short-lived AD groups help enterprises take control of Active Directory when used with a specially reinforced AD forest for management.
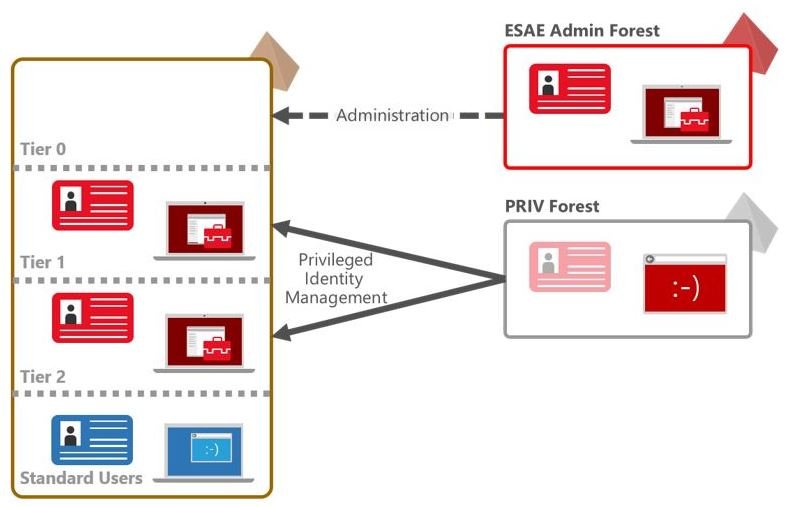
These mechanisms, in conjunction with activity logging and appropriate security monitoring, should allow domain administrators to mitigate the risk of attack.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











