The Common Weakness Enumeration (CWE) vulnerability categorization system has released its TOP 25, where the most common and dangerous security flaws of the past two years meet. According to information security training specialists, CWE considers listed flaws to be highly dangerous due to their ease of operation, their ability to operate, and how often a related attack occurs.

For the creation of this list, CWE considered the information available on systems such as Common Vulnerabilities and Exposures (CVE), the Common Vulnerability Scoring System (CVSS), as well as the information available in the National Vulnerability Database (NVD).
Below is a brief description of the reported flaws, as mentioned by the information security training specialists:
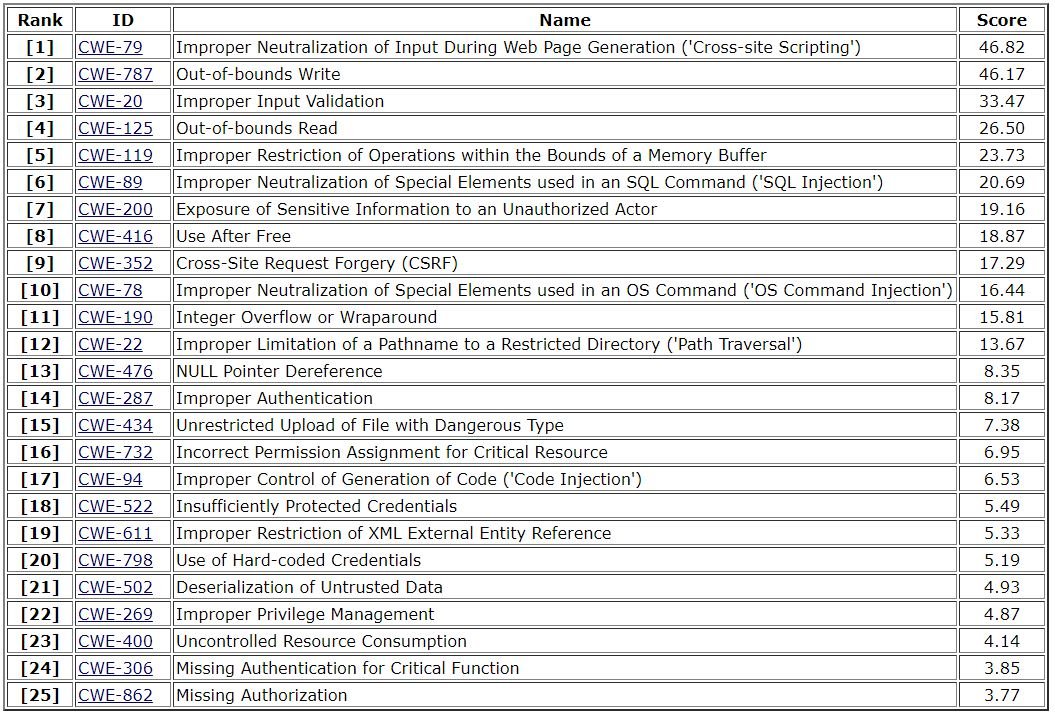
Experts mention that the main difference between this TOP 25 and the previous one is the move to exploiting specific flaws instead of class-level flaws. Although these class-level flaws can still be seen in the list, their rankings dropped considerably. Specialists believe that this trend will continue in the near future.
In the list, flaws at class level CWE-119 (inadequate restriction of operations within buffer limits), CWE-20 (incorrect input validation), and CWE-200 (sensitive information exposure) lowered some points. On the other hand, specific errors such as CWE-79 (incorrect disable entry in the generation of web pages) have shown a noticeable increase, as mentioned by the specialists of the information security training.
The flaws that increased your scores the most in the most recent list are:
- CWE-522 (Inadequately Protected Credentials): from #27 to #18
- CWE-306 (Lack of Critical Function Authentication): from #36 to #24
- CWE-862 (Lack of authorization mechanisms): from #34 to #25
- CWE-863 (Incorrect Authorization): from #33 to #29
As you can see, these flaws reside in some of the most difficult areas to analyze in a computer system. On the other hand, specialists believe that the user community has improved their analytics and protection capabilities, significantly reducing the incidence of multiple security flaws.
The flaws that lowered your chart scores the most are:
- CWE-426 (Unreliable Search Path): from #22 to #26
- CWE-295 (Incorrect Certificate Validation): from #25 to #28
- CWE-835 (Loop with unreachable output condition): from #26 to #36
- CWE-704 (Wrong type conversion): from #28 to #37
This TOP 25 can be very useful for developers, researchers and users, as it represents an ideal report of the most consistently encountered flaws, in other words, it is a representation of cybercriminal trends.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











