Cyber criminals are compromising servers and individual machines by sending malicious files to victim’s. If these files are clicked by mistake, they can lead to complete compromise of system. Hackers always plant backdoor in compromised system to keep monitoring activities and steal confidential data slowly slowly.
Most of the people are not aware about any suspicious activity running in the background. Digital forensics specialist of International Institute of Cyber Security recommends few options to identify these types of breaches. Some of the very basics steps are also covered in part 1 of Windows incident response.
Login Activities
- After an incident, the first step is to verify the logged in users in our machine. Verify using this command line “net user”
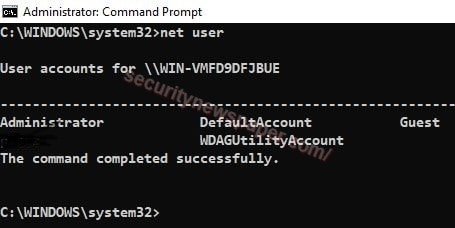
Windows information
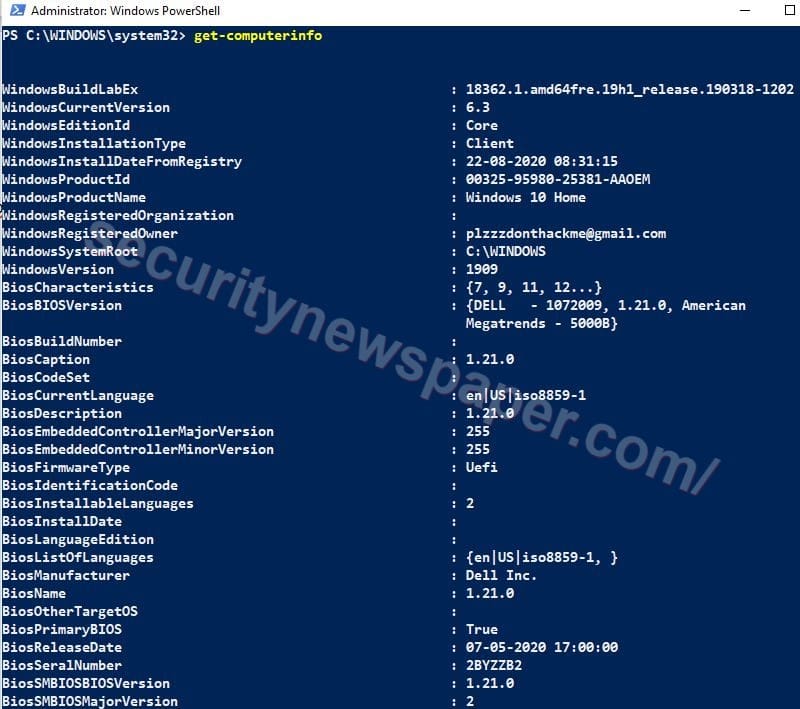
“get-computerinfo” is the command to view the complete information about the windows machine.
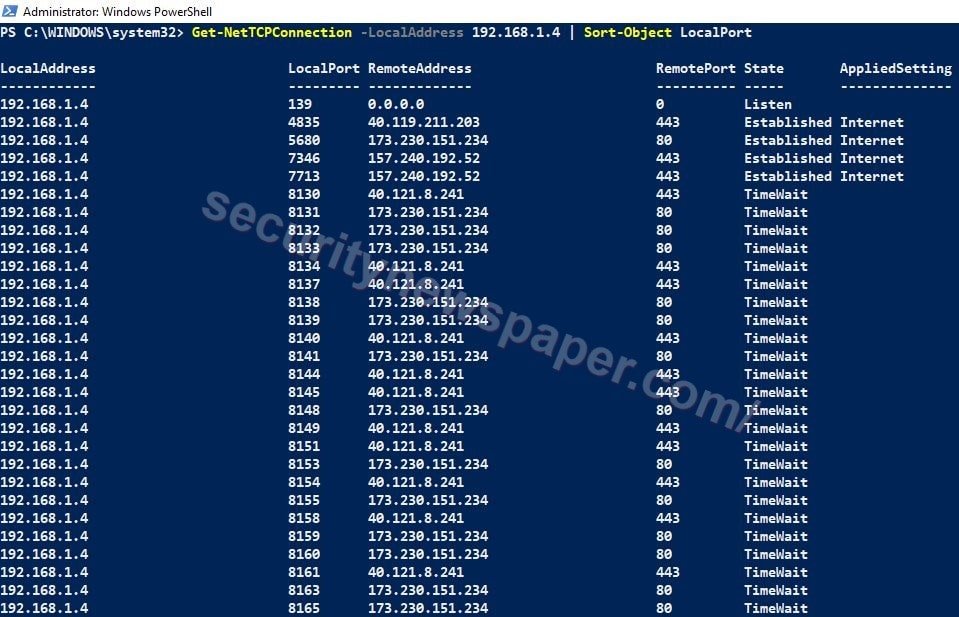
Active TCP & UDP ports
- Now, we can check the active TCP and UDP ports in our machine.
- Mostly we use “netstat” in our command prompt, the same process can be seen in powershell by using this command. “Get-NetTCPConnection -LocalAddress 192.168.0.110 | Sort-Object LocalPort”
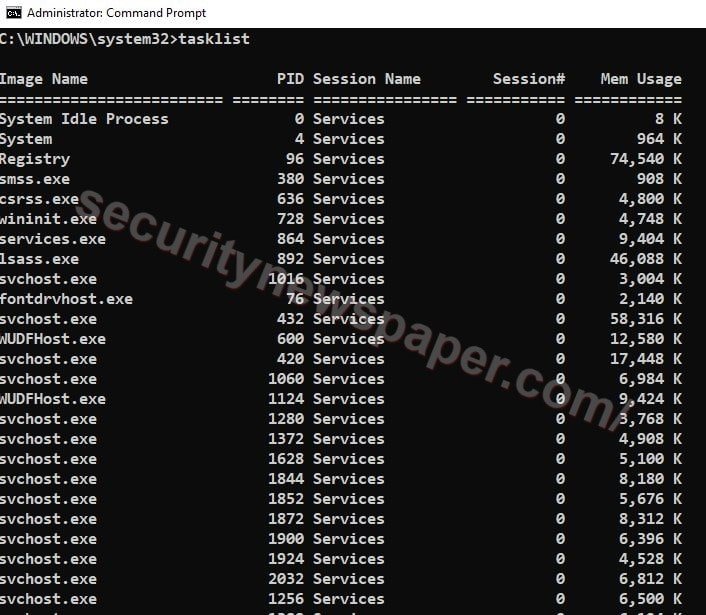
Tasklist
We can see all the running process with the process id and it also displays the amount space consumed. Use this command on command line. “tasklist”
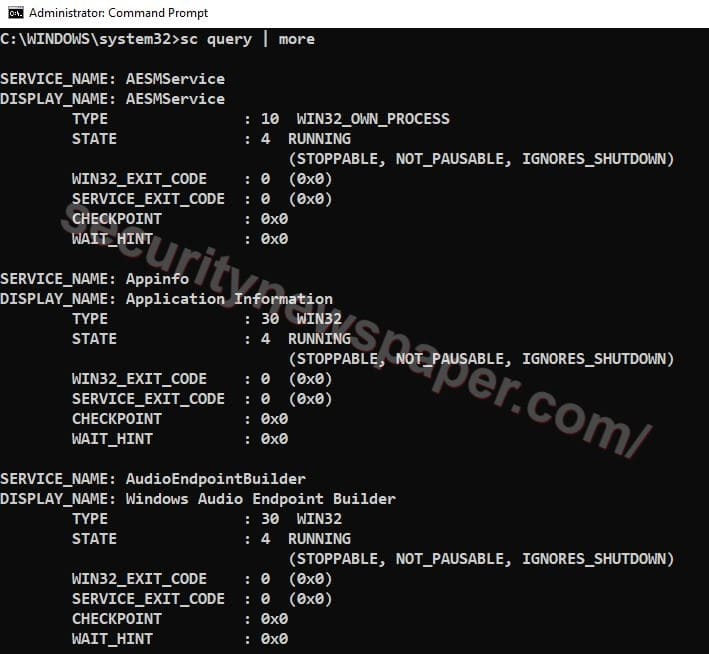
Services
- If we feel any abnormal services are still running in our machine, use these commands to verify the activities.
- ”net start” this command will display the current running activities or if we want more details about each and every services, use this command “sc query | more”
Autorunning
- If any malware or rootkit is installed in your machine, they install services/application in the background, which restart on every reboot.
- To check the auto running application in windows machine. “Get-CimInstance Win32_StartupCommand | Select-Object Name, command, Location, User | Format-List”
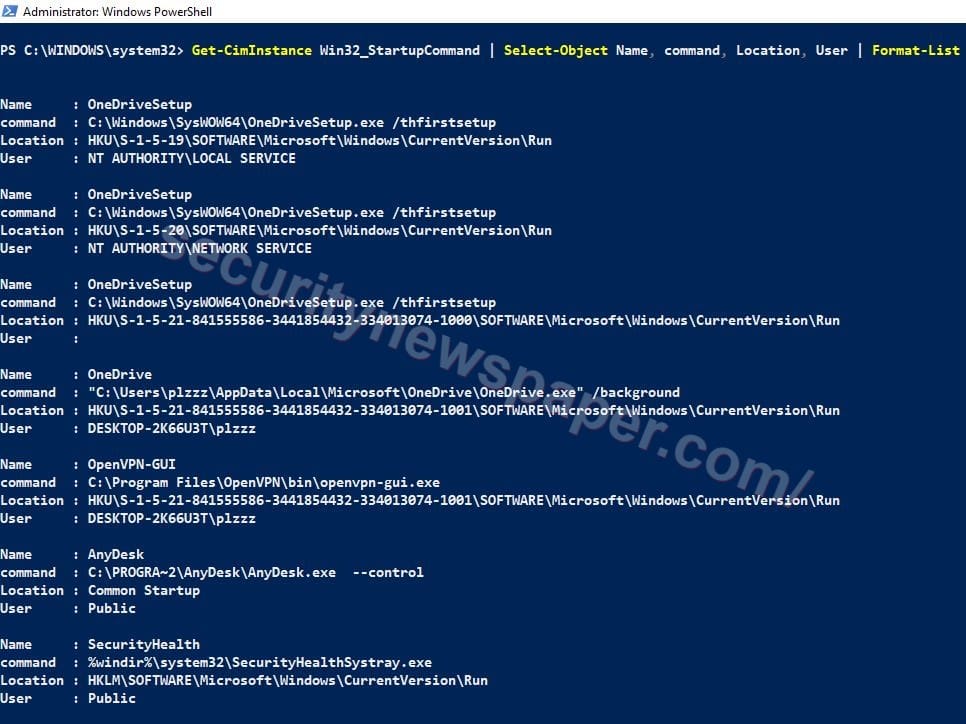
- Here, we have all auto running applications with the file path. We can verify by visiting each and every file.
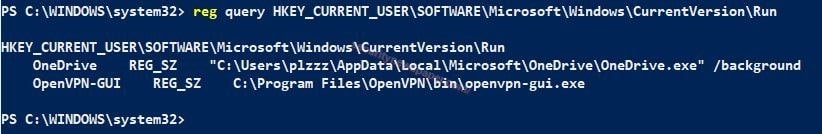
Registry Entries
- In most of the case malware makes a registry entry. To verify the activities in registry we can use reg query command.
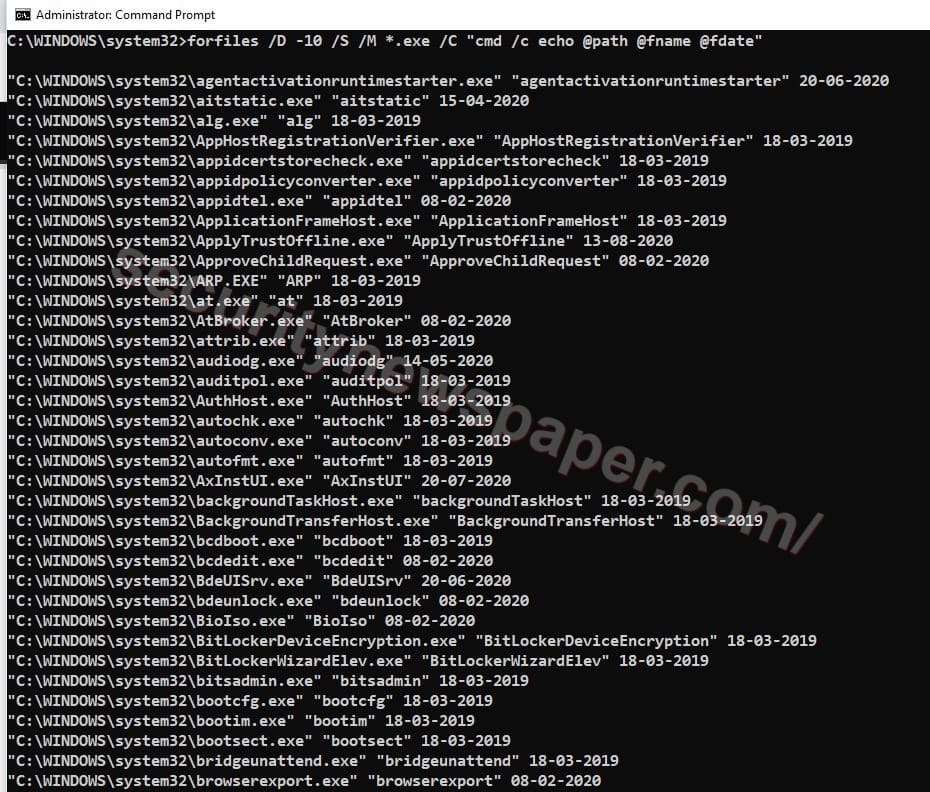
Find Files with Extension
- Now, we can view files which would be malicious and that ends with particular extension (.exe) and with modified dates.
- To view those particular files with file name\path\Modified data, use this command “forfiles /D -1 /S /M *.exe /C “cmd /c echo @path @fname @fdate”
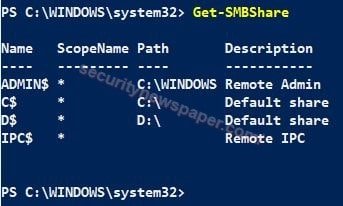
File Sharing
- After an incident, we should be aware on the file sharing in our machine.
- We “net view \\127.0.01” in command prompt and in the same way we can verify in power shell by using this command. “Get-SMBShare”
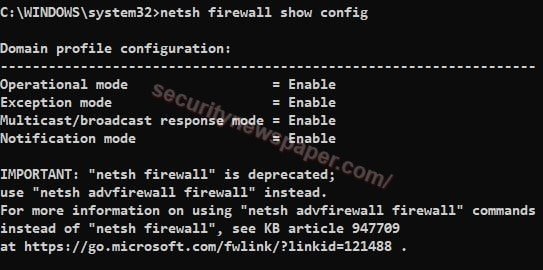
Firewall Settings
- Firewall is used to monitor and controls the incoming and outgoing traffic.
- So here, we have to verify the all traffic rules by using command line “netsh firewall show config”
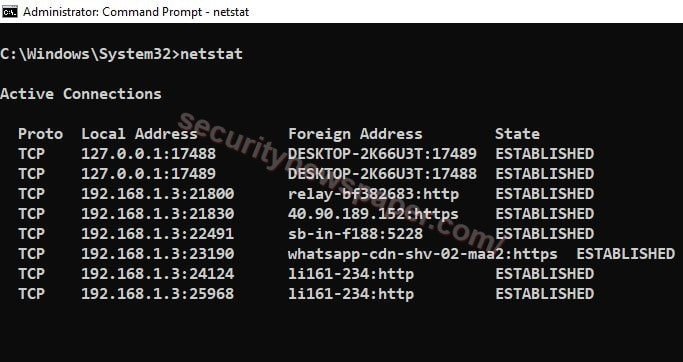
Netstat
- The netstat command used to display detailed information about how our computer is communicating with other computers on network and it is also displays that protocol, local address, foreign address and state.
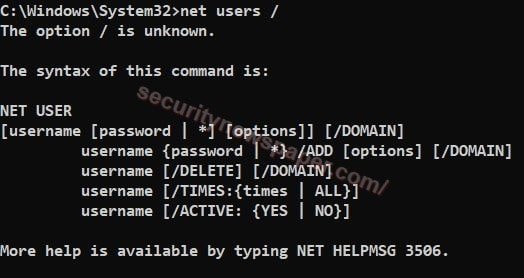
Net user
- The net user is a command used to add, remove and make any changes to any users account in the command prompt, by using this command line. This command in available in all windows versions.
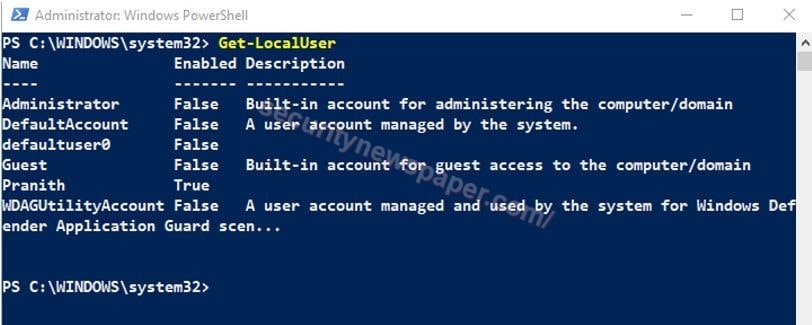
Get-LocalUser
- “Get-LocalUser” PowerShell cmdlet lists out the local users in our machine with the status. If any abnormal user as logged in, we can able to view the login details.
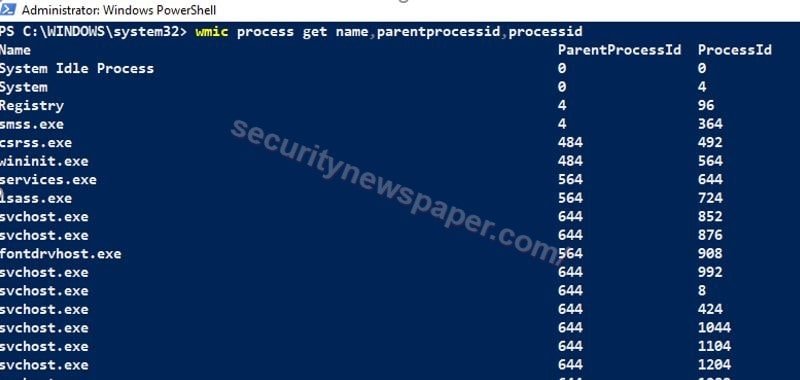
Process List
- We use this command to view any abnormal activities in our machine “wmic process get name,parentprocessid,processed”. This will displays the name with parent process id and process id
Process File Path
- This command will display the particular process with the file path. ” wmic process where ‘ProcessID=PID’ get CommandLine”
PS C:\WINDOWS\system32> wmic process where 'ProcessID=18372' get CommandLine CommandLine "C:\Program Files\WindowsApps\Microsoft.YourPhone_1.20071.95.0_x64__8wekyb3d8bbwe\YourPhone.exe" -ServerName:App.AppX9yct9q388jvt4h7y0gn06smzkxcsnt8m.mca
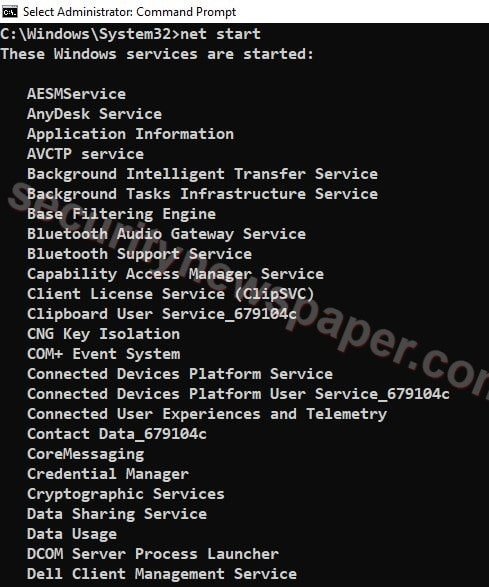
Net Start
- “net start” command is used to list out all the network running services. After the incident, we must also verify this activity.
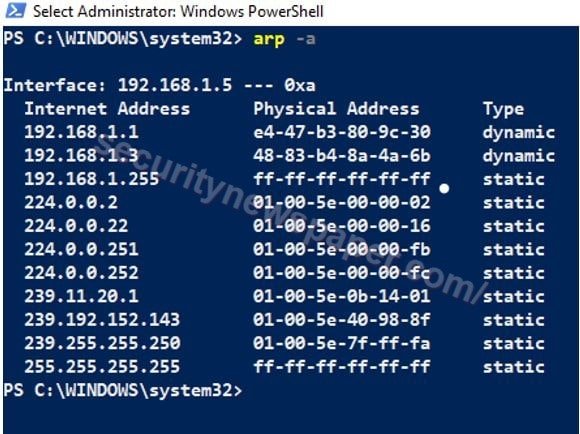
Address resolution protocol
- “arp -a” command used to display the current arp entries by collecting the current protocol data. This will displays the internet address and physical address.
Firewall Changes
- As we all know about firewall monitors incoming and outgoing traffic in our machine.
- Now, using this command we can verify the last modified firewall rules “Get-WinEvent -FilterHashtable @{LogName=’Microsoft-Windows-Windows Firewall With Advanced Security/Firewall’;} | FL TimeCreated, Message”
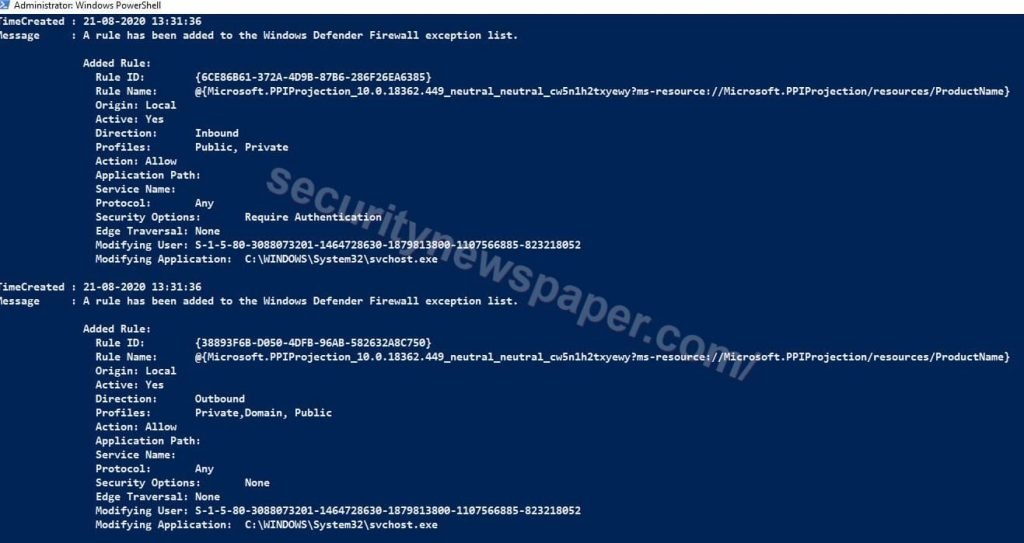
EventLog
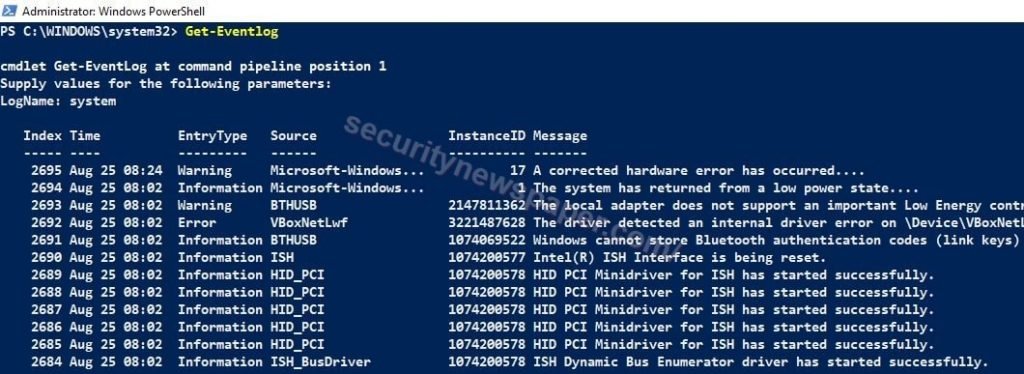
- As we all know in any windows machine, it store all the application and services logs. Now, we use this command to pull all the application and services logs list in our machine. Based on this list we can verify the activities after the incident. Researcher of International Institute of Cyber Security uses these commands to check event logs.
- Using this command we can search any logs “Get-EventLog”
Installed software/packages
- Now, we have to verify the any malicious application is installed by the cyber criminals in our machine. For this we use “wmic product get /ALL” command to check the installed application name with file path.


Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











