Information security specialists consider the most dangerous security threats to be those that receive constant updates. An example of this is the Qbot banking Trojan (also known as Qakbot and Pinkslipbot), which has been wreaked havoc for more than ten years thanks to its developers continually updating it. Qbot has multiple malicious features, among which are:
- Theft of information from infected systems (email addresses, passwords, bank details, etc.)
- Installing other malware variants
- Connecting to malware drivers to bank transactions from the victim’s IP
- Hijacking legitimate email conversations to spread the infection to other users
Last March, Check Point Research specialists detected an attack campaign using Qbot that ran until June; as the experts anticipated, the operators of this campaign paused their activities (allegedly to carry out subsequent attacks), however, these hackers reappeared unexpectedly less than a month after the hiatus.
At the end of July, experts detected the return of Emotet, one of today’s most dangerous Trojans, with which they managed to infect about 5% of the companies worldwide. In some of these infections experts also detected an updated version of Qbot, which contained a new command and control infrastructure, as well as updated techniques for malware spreading. Most of these infections were detected in the United States and Europe, mainly affecting public organizations, militia, manufacturing, among others, mentioned Check Point Research experts.
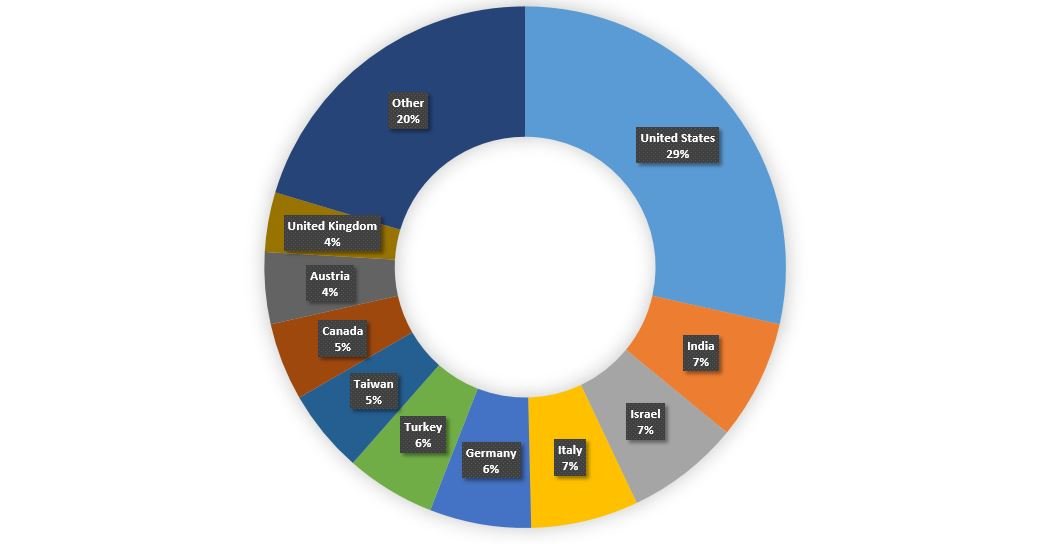
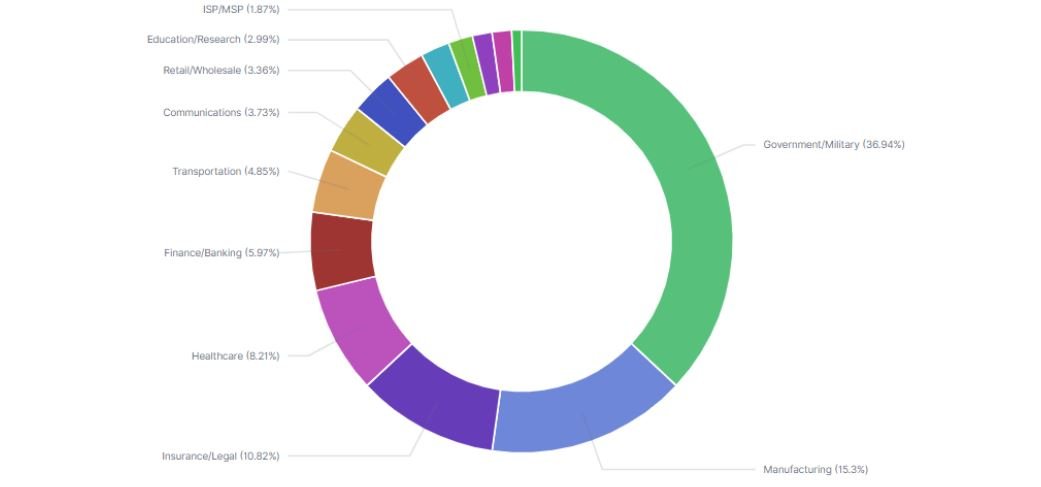
Despite the multiple updates received by this Trojan, specialists consider that the most important stage of the infection process remains the use of malicious emails. The following is a diagram describing the infection process detected on the new Qbot update:
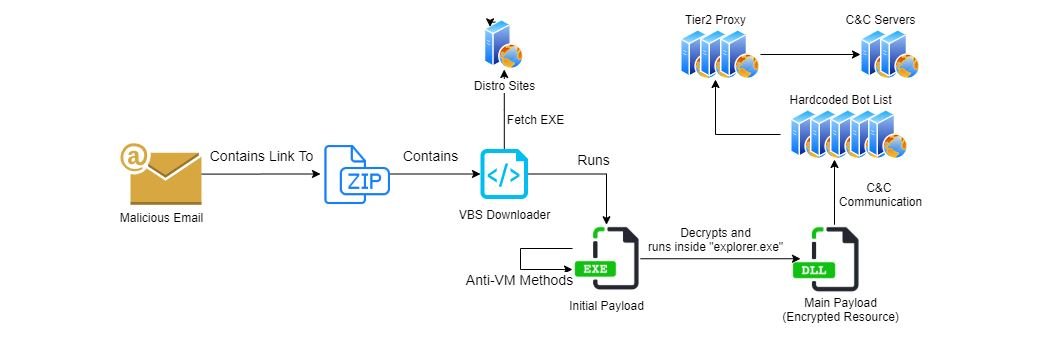
Although at first glance the use of malicious emails does not seem to show something innovative, experts detected that the operators of this campaign were able to hijack email conversations (as mentioned at the beginning). Apparently, conversations can be hijacked using “Email Collector“, a module recently added to Qbot. The following images show examples of malicious emails:
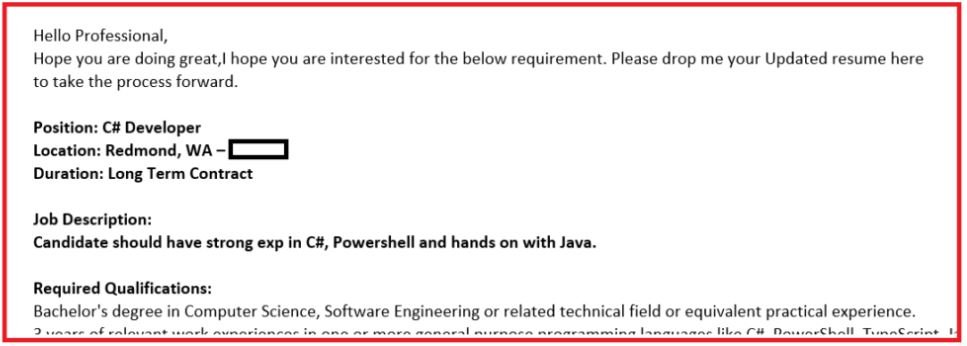
As you can see, these messages contain a URL that redirects users to a ZIP with a malicious Virtual Basics Script (VBS) file. Experts detected hundreds of different URLs used in this campaign, most of them redirecting to compromised WordPress sites or created specifically for these purposes.
Although it didn’t look like a sophisticated hacking campaign, the new version of Qbot has dangerous capabilities that could put any organization’s IT infrastructure at risk, so companies will have to remain alert to any attempted attack.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.













