An ambitious hacking campaign was detected last weekend. Specialists from a malware analysis course detected an attack that would have compromised around 2,000 websites around the world operating with Magento, the popular open source software for e-commerce sites.
Preliminary reports indicate that the incident brings together all the characteristics of Magecart attacks, in which threat actors inject malicious code into a website to extract financial information from inadvertent users; this campaign has been identified as “CardBleed Attack”. It should be noted that the affected websites operated Magento 1, a version that stopped receiving updates for a few months now.

A Sansec report mentions that at least 1904 different e-commerce sites were infected with a sophisticated keylogger in their payment sections; the attack began this Friday with the infection of 10 websites, and spread throughout the weekend, infecting 1058 more websites on Saturday and 839 more between Sunday and Wednesday, mention specialists from the malware analysis course.
The security firm had detected a similar campaign in 2005, although on that occasion hackers only managed to attack 960 online stores, indicating that the operators of the attack have managed to advance the development of more sophisticated methods of skimming. This incident could have compromised the financial information of tens of thousands of people.
Another interesting fact about this incident is that many of the affected websites had not been attacked before, suggesting that a new method of attack was used to access the servers of the affected sites. Although the incident is still under investigation, experts from the malware analysis course mention that the campaign could be related to a zero-day exploit that was released a couple of weeks ago on a hacking forum.
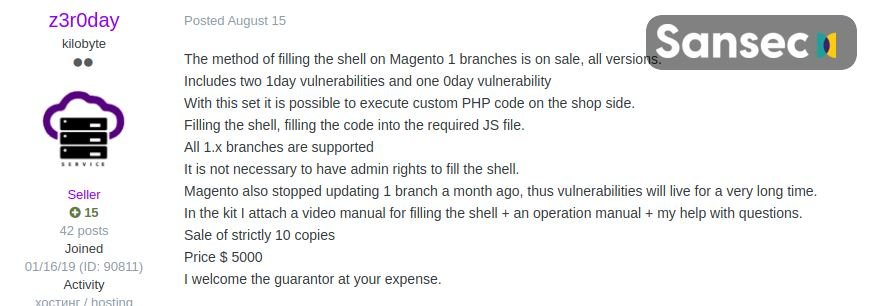
A seller on dark web, self-called z3r0day, announced the sale of a remote code execution exploit of functional code in Magento 1 for $5,000 USD, a payment that includes a manual to carry out the attack. In a video posted by the allegedly Russian hacker, it can be seen that a Magento administrator account is not even required to complete the attack.
Finally, Adobe disclosed that it does not plan to release fixes for these vulnerabilities since Magento 1 is in the final stretch of its lifetime, although this seems like an unreasonable decision due to the large number of e-commerce sites that still operate with this version of the software.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











