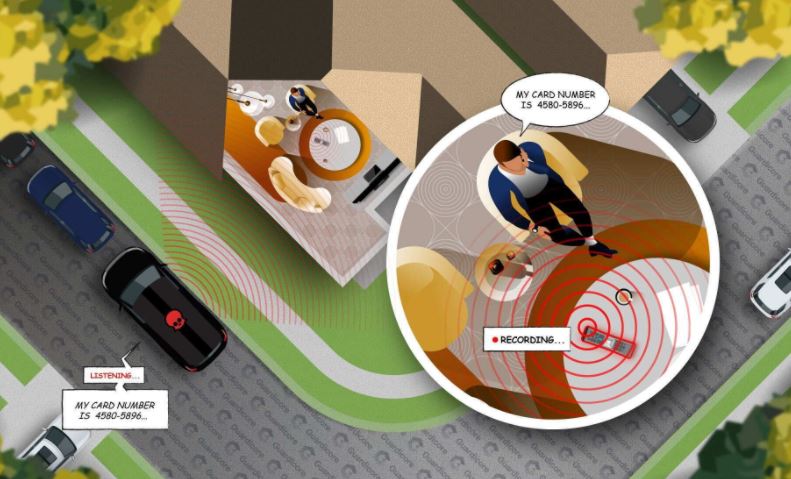
A group of cybersecurity experts has found a way to turn a Comcast remote control into a device capable of capturing audio without the need for physical access or target user interaction. The attack, dubbed “WarezThe Remote”, allows threat actors to take control of the device to spy on victims’ conversations within 20 a yards range.
The exploited device for the attack is a Comcast XR11 remote control, which unlike other similar devices relies on radio frequency for communication with the cable decoder, plus it has a built-in microphone to capture voice commands. Guardicore experts examined the device’s firmware and discovered how communication between the remote control and the set-top box is presented.
During the investigation, experts encountered a security flaw in the implementation of the Consumer Electronics Radio Frequency Protocol (RF4CE), which is responsible for encrypting transmitted information: “RF4CE security is established packet by packet; when sending the information, if a bit of these packets is not set correctly, the packet is sent in plain text,” the report mentions.
XR11 firmware accepted plain text responses to encrypted requests from the remote control, allowing threat actors to guess the contents of a request by creating a malicious response that was passed through a decoder.
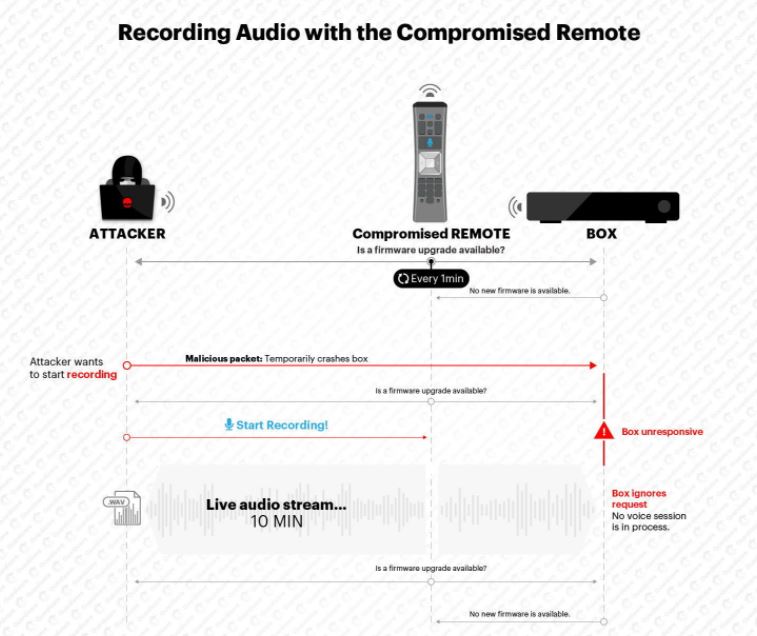
In addition, experts applied reverse engineering to the firmware of the remote control in order to activate the microphone, altering the software so that recording requests were activated every minute automatically. Researchers were able to record up to 10 minutes of audio.
Deploying this attack is complex, plus advanced hacking skills are required to correctly reverse engineer the firmware, create the required patches, and upgrade the XR11 remote control, complicating an attack in real-world scenarios, not to mention that the success of the attack would also depend on other variables such as the capacity and cost of the required devices.
Comcast received the report and has already solved the problems reported by the researchers. On September 24, the company reported that its XR11 devices were fully protected from the attack described by Guardicore.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










