Tech support scams are one of the most common threats to technology users, as both legitimate service providers and end users are exposed and can suffer considerable consequences. Within this variant of fraud, browser locking has established itself as one of the most common and effective practices available to threat actors.
Within such campaigns, MalwareBytes specialists have noticed one with different behavior in which threat actors use Facebook for the distribution of malicious links that redirect victims to a browser-blocking website, employing hoax techniques such as cross-site scripting (XSS) attacks.
Needless to say, links posted on social media are one of the most effective ways to deploy malicious content, so users should be careful when interacting with these elements, as they could be used to start downloading spam or malware.
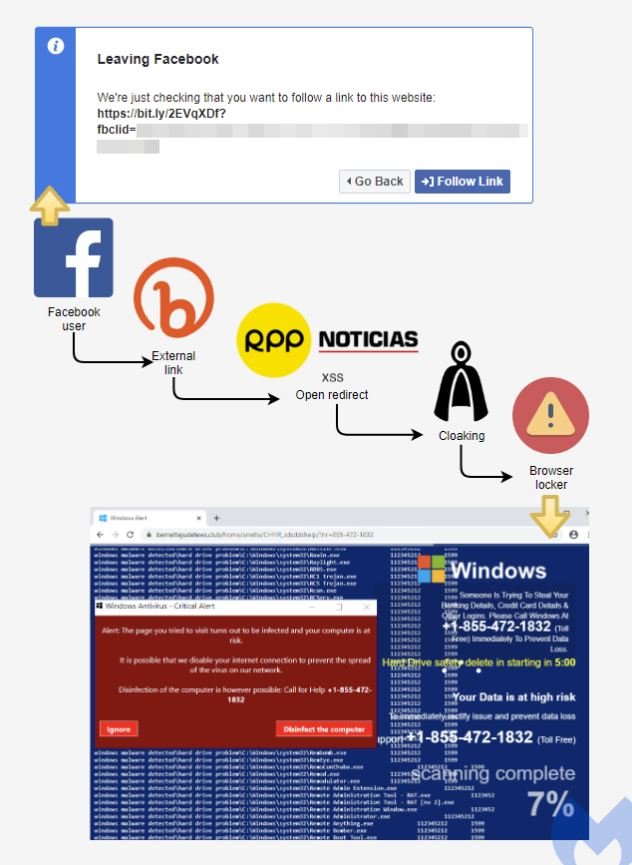
The campaign analyzed by specialists is somewhat unusual, as threat actors usually employ tech support scams through malicious advertising. Although Facebook displays a warning to ensure that the user wants to follow the link, the campaign appears to have a high degree of success, as hackers use the bit.ly service to shorten URLs in the first stage of redirection.
Specialists identified 50 different bit.ly links over a three-month period, which could be considered a sample of abnormal behavior from threat actors. While MalwareBytes has not confirmed why hackers use Facebook to deploy their attacks, it is true that this activity can progress at an accelerated pace using the apps on the social network.
Facebook has already received an alert, so the platform is expected to slow the progress of this campaign as soon as possible.
Returning to the bit.ly URL, it activates the second stage redirect involving a website operated from Peru, where the XSS attack that allows an open redirect is triggered. Threat actors love to abuse open redirects because it gives some legitimacy to the URL they send to victims. In this case, the victims are redirected to a news site with more than 20 million visitors per month.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











