Since the rise of streaming platforms millions of users consider it essential to have a smart TV in their homes. This trend has favored companies that were not previously widely popular, such as TCL, which has become the third largest manufacturer in this sector.
However, the popularity of these TVs has also made specialists pay more attention to the security of these devices, leading to the detection of some severe security vulnerabilities that could compromise user information.
A group of researchers performed a scan using Nmap with which various open TCP ports were detected that could be abused by groups of threat actors. In addition, using the IP addresses of the open ports specialists were able to access them through a conventional web browser.
Although some ports did not open or caused the browser to crash, some of them displayed interesting messages, such as the user not being able to access a particular file. When testing with another address (“http://10.0.0.117:7989/sdcard”), the search eventually threw the results into a directory served entirely over HTTP, something very little recommended by the cybersecurity community.
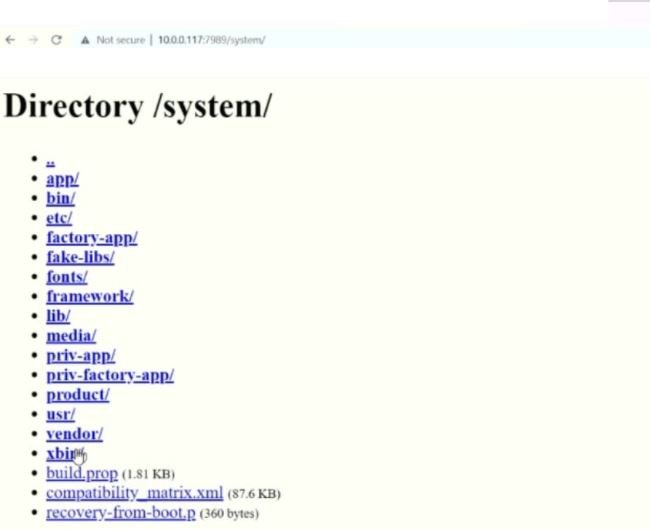
“Why would an Android device need a web server running on a non-standard port? What kind of manufacturer publishes the entire file system of a device?” the researchers mention.
This behavior has already been reported to TCL, to which the company responded by reporting that the vulnerabilities had already been corrected: “Exposed files should not be arbitrarily written by potentially malicious users or APKs,” the researchers conclude.
Although the company was informed in a timely way about these failures, it appears that the investigators in charge of the finding received no compensation. In addition, the company has not shared further reports on the process of correcting these failures. Many specialists consider such practices to be very common when it comes to devices that function as cheaper options, so for security reasons, users may need to reconsider their decision between cheaper or better security smart TVs.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











