A recent report states that a group of nation state sponsored threat actors managed to compromise SolarWinds Orion IT management software to attack multiple organizations in the U.S., including government agencies such as the US Treasury and the National Telecommunications and Information Administration (NTIA).
Microsoft and FireEye experts claim that malicious hackers used a variant of malware known as SUNBURST or Solorigate.
The Cybersecurity and Infrastructure Security Agency (CISA) also issued an alert regarding the active exploitation of some Solaris implementations, used by threat actors to install a backdoor in vulnerable versions by abusing its update system: “This vulnerability is related to reports revealed between March and June 2020; the flaw could be the result of a sophisticated supply chain attack deployed by a state actor,” the Agency says.
The campaign has been active since the early 2020s, starting with data theft in vulnerable versions of SolarWinds Orion. Threat actors behind these attacks could have generated persistence in the affected systems, as the first compromised targets were detected in December 2019.
The hackers behind the supply chain attack are especially focused on government entities, technology firms, telecommunications companies and other services in North America, Europe and some Asian countries, FireEye specialists reported.
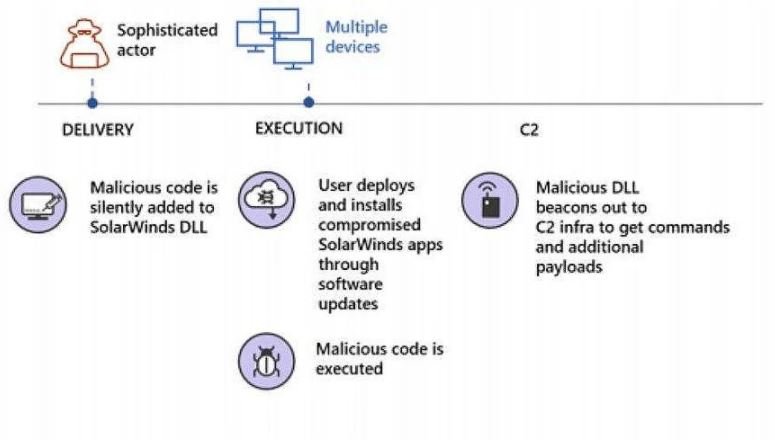
On the other hand, the Microsoft report contains a guide for users to implement some additional protection mechanisms to prevent these attacks. The company ensures that these incidents begin with a malicious code intrusion campaign in SolarWinds Orion after hacklers implement malicious with which they will try to implement the backdoor.
“Victims are tricked into believing that no signs of malicious activity have been detected and that the program is not behaving as planned, so cybercriminals can gain persistence relatively easily,” Microsoft’s report says.
In response to these reports, SolarWinds released Orion Platform version 2020.2.2 HF 1, which allows administrators to protect their systems running vulnerable versions: “We recommend upgrading as soon as possible to mitigate the risk of exploitation,” the company’s notice states.
Although these reports make no mention of the origin of the attacks, a Washington Post report linked these attacks to Russian State sponsored threat actors. In response, the Russian Embassy in the U.S. called these claiming as unfounded, ensuring that the activity described flagrantly violates Russian foreign policy. More details are expected to be revealed as soon as possible.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











