In a recently detected campaign, a hacker group has been resetting administrator passwords on WordPress sites by exploiting a critical zero-day vulnerability in Easy WP SMTP, a plugin with over 500,000 active installations. The flaw was corrected this Monday.
This tool allows website administrators to modify SMTP settings for outgoing emails from their users’ platforms.
According to the report, version 1.4.2 and earlier of the plugin contain a function to create debug logs of emails sent from the user’s website. Because the plugin folder does not contain any index.html files, servers have directory list enabled; in turn, threat actors could find these records with ease.
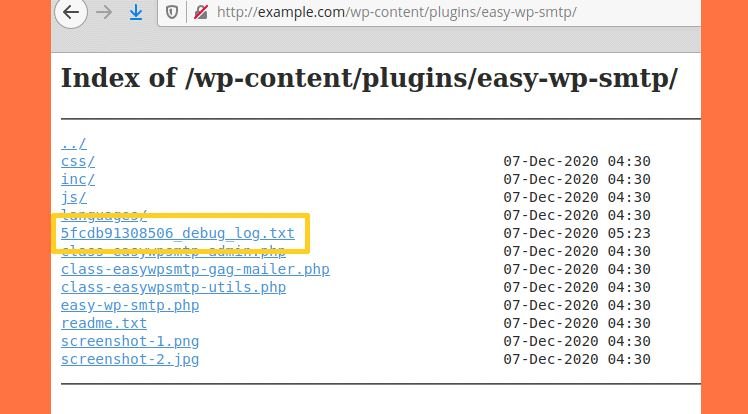
Cybercriminals who managed to exploit this flaw in vulnerable sites have been deploying automated attacks to identify administrator accounts and force a password reset. All attackers have to do is access the debug log after resetting the password, taking the reset link and taking control of the target website.
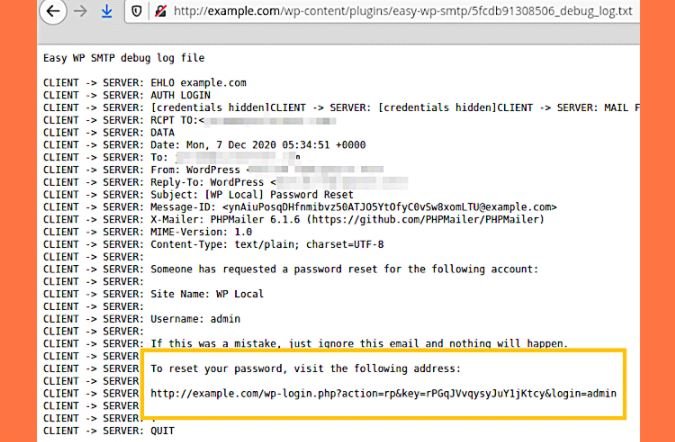
The developers fixed this flaw by simply moving the plugin debug log to the WordPress logs folder to ensure its protection. This is the second time a zero-day vulnerability has been detected in this plugin; in March 2019, a group of researchers discovered that unidentified threat actors were exploiting a flaw in Easy WP SMTP to enable user registration and create administrator accounts as a backdoor.
Fortunately, it’s not all bad news. Unlike the 2019 landscape, the current version of the CMS features a built-in auto-update feature for themes and add-ons. Added in August 2020, with the release of WordPress 5.5, if enabled, this feature will allow plugins to always run in the latest available version without having to update them manually.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











