Cloudflare is a denial of service (DDoS) protection mechanism for your servers or, so to speak, it is a barrier between the user and the websites they visit. This tool functions as a proxy, providing additional services such as caching, attack protection and hiding the true IP address of the server hosting the user’s website.

According to the ethical hacking experts from the International Institute of Cyber Security (IICS), when Cloudflare is configured correctly, users’ site IP address will be completely secured from hackers. However, it’s worth asking: How common are configuration errors? This article focuses on CloudFail, a tool to look for flaws in Cloudflare installations that has gained great popularity in the hacking community.
What exactly is CloudFail?
To get started, let’s remember that each site can have subdomains, for example:
- www.site.ua
- kiev.site.ua
- forum.site.ua
- Among others
An important thing about these subdomains is that each of them can have its own IP address. Those names allow you to specify one IP (or multiple addresses at a time) for site.ua, another IP for www.site.ua, another IP for kiev.site.ua, and so on.
A situation can arise later. When DNS records in the site.ua domain registered the Cloudflare IP address, there are no DNS records for the www.site.ua subdomain pointing to another IP not protected by Cloudflare, as mentioned by ethical hacking experts. The final result will reveal an IP address that:
- May be the actual IP address of the site
- It may be the IP address of the subdomain only, but we can find information about the actual owner or some clue for further investigation
We can’t just take and get a list of all the subdomains. Therefore, we need to iterate over the different options. Here’s exactly what CloudFail does:
- Test multiple subdomains
- Check if there is a DNS record for a subdomain; if so, we get an IP for this subdomain
- It also verifies whether or not a received IP is protected by Cloudflare
As a result of these analyses it is possible to find IP addresses that are not protected by Cloudflare. Ethical hacking experts point to the importance of assuming that the IP addresses of the subdomains belong to the owner, although this is not always true because the owners of the primary domain can specify any IP address, even if it does not belong to them.
Installing CloudFail
To install on Ubuntu, Kali Linux, Debian, Linux Mint, etc., run the following commands:
- Update
sudo apt update
- Component installation
sudo apt install python3-pip git tor
- Cloning the tool from Git
git clone https://github.com/m0rtem/CloudFail
- Then go to the CloudFail/cd directory and install CloudFail using the following command
sudo pip3 install -r requirements.txt
- Check the status of the application using:
python3 cloudfail.py -h
- Before launching, update the app. The Cloudflare IP address list as well as the CrimeFlare database that contains the known IP addresses of some sites will be updated. Enter the following command
sudo python3 cloudfail.py –u
- If you want the program to work on the Tor network, you must start the Tor service using:
sudo systemctl start tor
- You can send Tor at startup, then you will not need to start this service after each computer restart:
sudo systemctl enable tor
How to use CloudFail
This program has only one required option (-t), after which you must specify the site name. Up next, the ethical hacking experts present additional information about all CloudFail options.
The program already comes with a list of words to list possible subdomains in a dictionary. If you want to use your own dictionary, specify it with the -s option. The dictionary file must be located in the data folder.
For example, if we want to get data for site.ua, the command we’ll use should look like this:
sudo python3 cloudfail.py -t site.ua
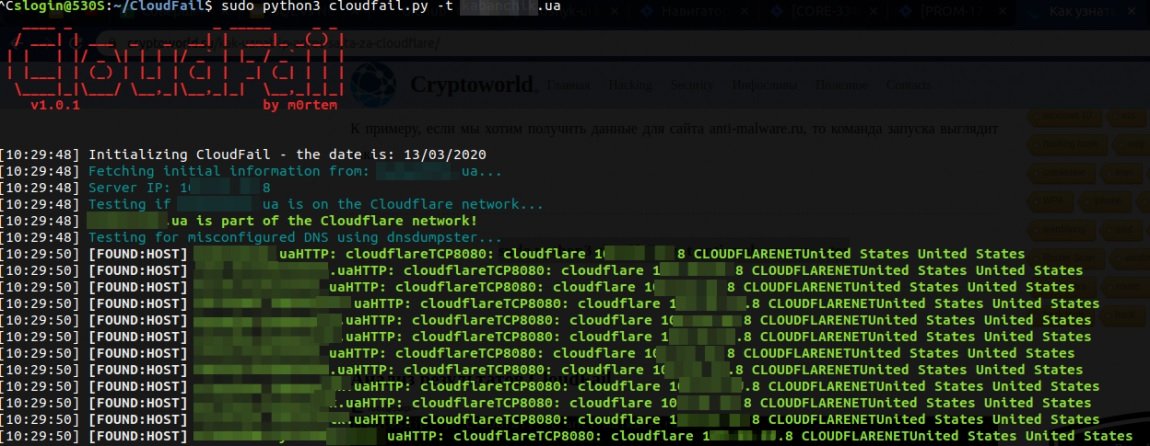
The chain is part of the Cloudflare network. This information tells us that the site is protected by Cloudflare. If this is not the case, then the scan will be interrupted at this point, as there is no point in moving forward.
The Misconfigured DNS Test line using dnsdumpster provides us with information about the enumeration of known hosts (subdomains) associated with the target site. This data comes from dnsdumpster.
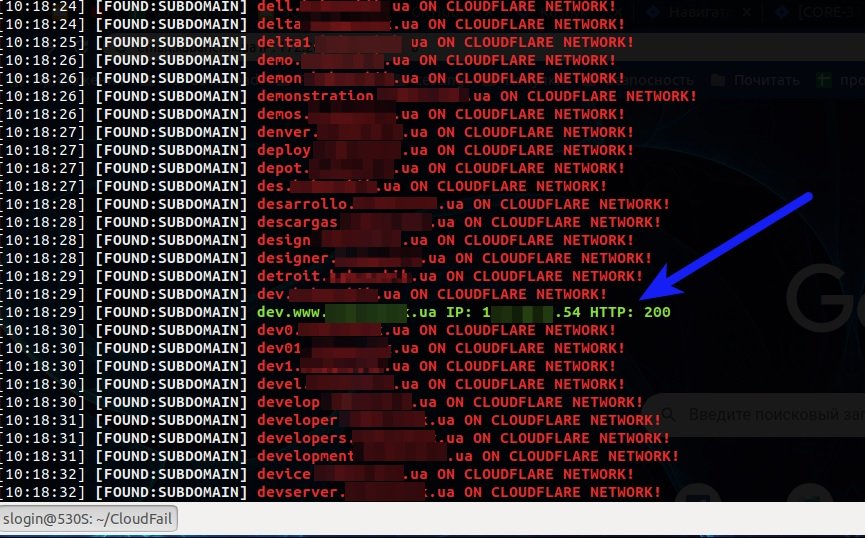
The red line refers to detected subdomains, but its IP is protected by Cloudflare; in other words, they are useless in determining the actual IP. On the other hand, the green line says that the IP of the host found is not protected by Cloudflare, so it could be the actual IP address of the site.
What can we do with these IP addresses? Here are some possible scenarios:
- Deploy DDoS attacks, as these IP addresses are not protected by Cloudflare
- Use nmap to know the weaknesses of the website
- Use Metasploit and, if possible, access the web app
With this article, IICS experts hope you understand how important it is to perform periodic verification on the protection of your websites, even if you use Cloudflare. As we’ve seen, threat actors can easily detect configuration errors and exploit them against us, so it’s best to be prepared against any attack.
Finally, you should remember that this content was made for entirely didactic purposes, so you should only try CloudFail and any other hacking tools in controlled environments with prior authorization.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











