The information stored on a computer does not always end up on permanent storage drives (hard drives, solid-state drives, removable storage, among others), but is also stored in RAM, as mentioned by secure data destruction experts from the International Institute of Cyber Security (IICS).
However, it should be noted that the information available in RAM and the data stored on a hard drive may vary. Depending on each case, the following situations may occur:
- The data may be encrypted on the hard drive, but not in RAM (for example, a password text file is stored on an encrypted VeraCrypt disk, which is opened in a text editor; in this case, the passwords of this file will be in RAM as plain text)
- The information can be created in the calculation process or receive data from the network (in this case, the original information is absent in permanent storages)
Experts in secure data destruction mention that analysis of the content (dump) of a running process is often used in reverse engineering when the source file is encrypted. For its running, the file must still be decrypted in RAM, so analyzing the running process facilitates reverse engineering.
You can think of other ways to analyze and search for information in a device’s memory:
- Identify apps that scan the clipboard
- Evaluation of the quality of password storage programs: If they contain passwords in RAM in the form of plain text when running these programs, it is strongly discouraged to use such programs
- Search for an application that contains certain strings or connects to a specific host
Then data secure destruction experts will demonstrate how to use mXtract, a pentesting tool to scan a device’s RAM for private keys, IP addresses, and exposed passwords.
This program can be used both as a post-exploitation tool and for security analysis, helping researchers evaluate the security of applications on a given system. Its main features include:
- Searching for running process strings using regular expressions
- Search for one process or all running processes at once
- Exposure of the results found in a completely understandable way
Installation
- To install mXtract, run the following commands on your Kali Linux terminal:
git clone https://github.com/rek7/mXtract
cd mXtract && sh compile.sh
sudo mv bin/mxtract /usr/bin/
sudo mkdir -p /usr/share/doc/mxtract/
mv example_regexes.db /usr/share/doc/mxtract/
- To install mXtract on BlackArch, you must use the following command:
sudo pacman -S mxtract
The tool has multiple options, although to begin with we will address the two main ones: -r and -wm. If you want to search for certain threads in RAM, secure data destruction experts recommend the -r option; users must then specify the path to a file that contains one or more regular expressions.
On the other hand, if you want to record all the information that the process has in RAM, you must use the -wm option. These options can be used at the same time, then a search will be performed and dumps from all processes will be stored.
Let’s start looking for threads in the processes. Experts in secure data destruction mention that the file is example_regexes.db the following regular expression:
(\d{1,3}(\.\d{1,3}){3})
It corresponds approximately to IPv4 addresses. Now you can start the search:
sudo mxtract -wr -e -i -d=/tmp/output/ -r=/usr/share/doc/mxtract/example_regexes.db
Below is the meaning of these options:
- -r=/usr/share/doc/mxtract/example_regexes.db: Path to file with regular expressions
- -e: Scanning files in the process environment
- -i: It should be indicated for detailed information about the process/user
- -d=/tmp/output/: Custom output directory. When you use the -wm option, process dumps are saved in this option. A file with the results is also stored if the –wr option is used
- -wr: This option is required to write matches found in a file (it will appear in the output directory)
The following is an example of the output when the program is running:
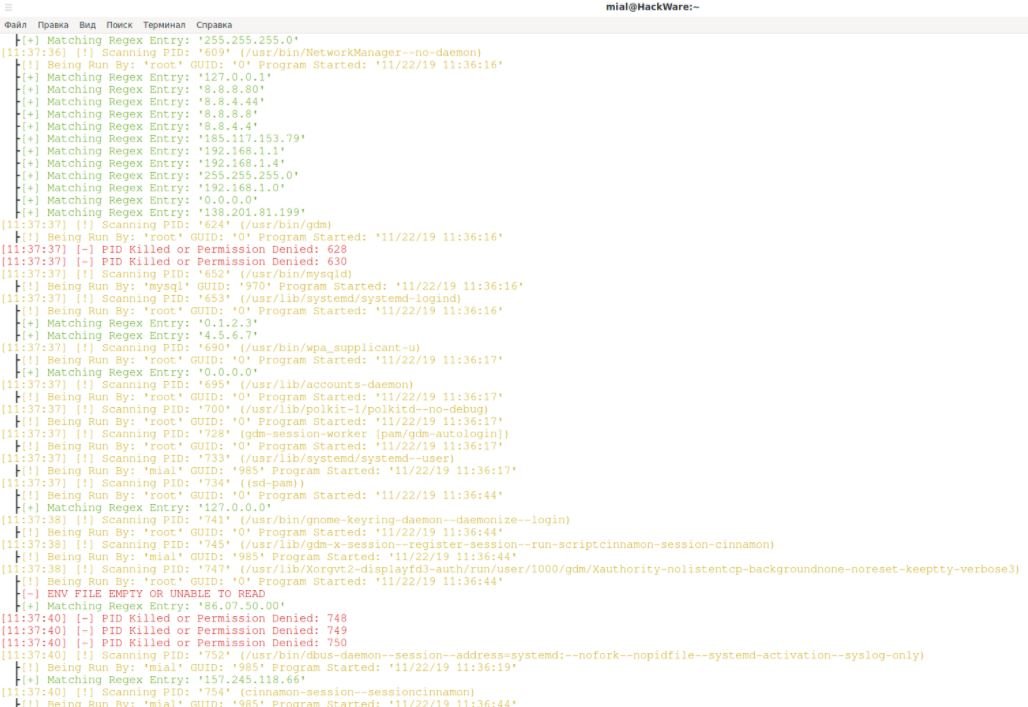
These are the IP addresses contained in the NetworkManager process:
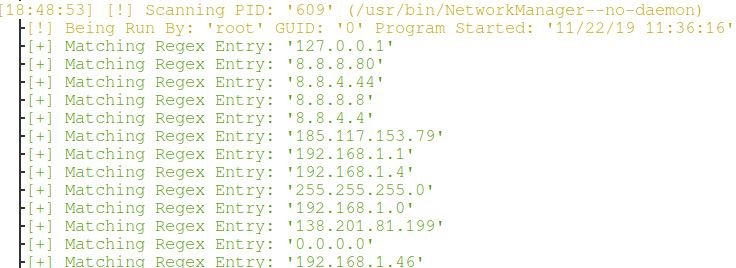
These are the IPs of the LibreOffice Writer process (although this does not mean that the program is connected to at least one of them, according to the secure data destruction experts):
As a result of running the previous command, the /tmp/output/regex_results.txt file will be created, besides the matches. The secure data destruction experts will then review some of the scenarios to use RAM search. You can also use your own ideas in this tool.
Assessing the quality of password storage programs
There are some programs to store passwords (password managers). You can also try different ways to store passwords, for example, in a plain text file on an encrypted disk.
You can specify literal search strings instead of regular expressions, according to the secure data destruction experts. You can enter multiple passwords for these lines; each regular expression must be on separate lines. For example, you can create a passwords.db file and write something like in the following example:
password1
password2
password3
As per the letters of the alphabet, they are most likely processed into another encoding, so it is unlikely that it will be possible to find a literal match in the strings. Therefore, you must first type the strings as a sequence of characters in the desired encoding.
After that, you can search for the contents of the processes in RAM:
sudo mxtract -wr -e -i -d=/tmp/output/ -r=passwords.db
For example, you can find passwords in a plain text file using this method, even if you are in an encrypted section of the target system.
Find programs that have access to the clipboard
Experts in secure data destruction mention that information that is copied to the clipboard is usually available in plain text (this depends on each program). In addition, in this way the user will be able to find any spying/monitoring program of the clipboard.
- Create a clipboard.db and type a unique string into it, for example:
fghfgjhgfhkgjlbnmnvbregfghdgfjgch
- Next, let’s copy to the clipboard and start scanning the processes:
sudo mxtract -wm -wr -e -i -d=/tmp/output/ -r=clipboard.db
- You can find programs that contain this line:
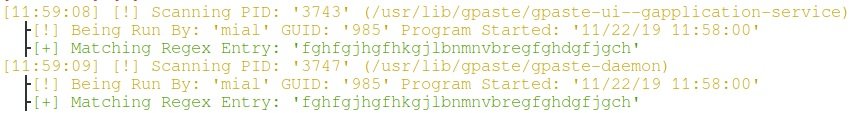
Search for passwords and keys in running processes
Below we will look for those lines that have high entropy and can therefore be passwords, keys and other sensitive data.
You can combine the work of these two programs. Let’s have mXtract extract almost all strings by creating a strings.db file and copying something like the following into it:
[ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=]{30,}
The characters in square brackets are those that can appear in the string, and between the braces is the minimum size of the string. Run the following command:
sudo mxtract -wr -e -i -d=/tmp/output/ -r=strings.db
Subsequently, using DumpsterDiver you will be able to search for lines with the required entropy, as mentioned by experts in secure data destruction:
python3 DumpsterDiver.py -p /tmp/output/ --entropy 5.3
This is a very crude concept, so in real scenarios you will need a more detailed adjustment of DumpsterDriver.
How to detect which programs are connected to a specific host
What can we do if we find a suspicious connection to a specific host after its completion? Experts in secure data destruction mention that on closed ports, if the process is still running, there is a possibility to detect it. To do this, specify the host name or IP address of interest as a search string.
Find a program that contains certain data
The above technique can be used not only for network addresses, but also for any string. Thus, it is possible to find a program that saves certain files or displays windows with certain lines.
Extract the contents of the clipboard
Depending on the software used, you can find a program that stores the clipboard in plain text. With the -p option, you can specify the identifier (PID) of a process to scan the target. If you configure regular expressions correctly, you can extract the contents of the clipboard.
For detailed analysis of the contents of a process you can use the -wm option; when specified, the raw data will be saved to the full content of each process.
How to find the ID of the analyzed process
Remember that if you want to scan a specific process, you can find its number with commands like the ones shown below:
ps a | grep -E 'cli(p)board'
ps a | grep -E 'libre(o)ffice'
Pay attention to parentheses: although they do not change the essence of the analysis, thanks to the use of these characters the process with grep does not end up in the output list.
To get only the number, you can run the following command:
ps a | grep -E 'cli(p)board' | awk '{print $1}'
CONCLUSION
A detailed description of all mXtract functions is available in https://kali.tools/?p=5147. When you start a process scan, experts mention that mXtract sometimes stops working suddenly until the system restarts. When using regular expressions, you might encounter a segmentation error message.
Find more material like this on the official platforms of the International Institute of Cyber Security (IICS).

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











