According to a recent report, malicious hacking groups may abuse a deserialization vulnerability in Zend Framework to run remote code on PHP sites. Identified as CVE-2021-3007, this flaw could also occur in some Laminas Project implementations.
Ling Yizhou, a cybersecurity specialist, mentions in his report: “Zend Framework 3.0.0 is affected by a vulnerability that could lead to a remote code execution scenario if the content is controllable, related to the Zend-http-Response-Stream class __destruct method in Stream.php”.
These flaws occur when the encoded data that the application receives from the user or system is not properly validated before the application performs decoding. As a result, it can lead to a denial of service (DoS) condition in the vulnerable application.
In Zend’s case, the fault comes from the Stream class destructor; in objective-oriented programming, construction and destruction methods are called when a new class object is created and destroyed. When the target fulfills its purpose in the program, the PGO interpreter will call the target destructor and follow another script to free up memory. The Expert Advisor mentions that the unlink() method, called by the Stream destructor, will wait for a file name as a parameter, which is of the string data type.
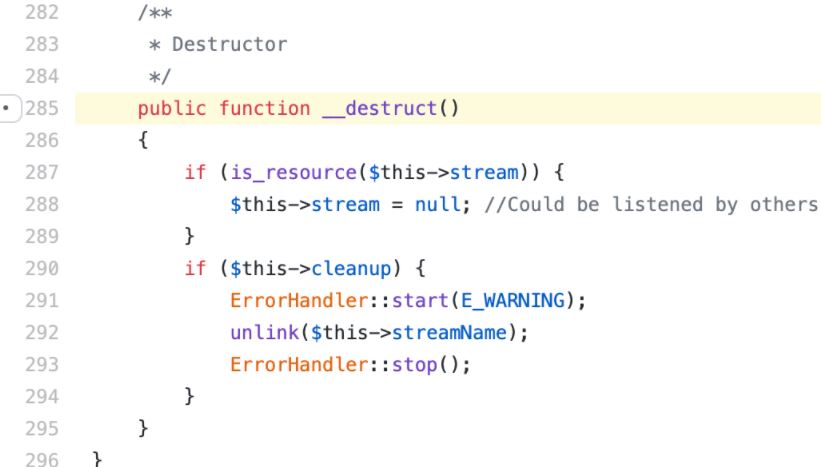
If the streamName object were of a different type, at the end of execution it would still be passed to the destructor; this in turn would attempt to call the method __toString to get its equivalent value to the string. This method could be easily modified by the goal creator.
The expert mentions that __toString in the Zend Framework Gravator class had been written by its programmers in such a way that it is possible to return values over which the attacker has direct control, which results in arbitrary code execution. If the Stream class receives a Gravator object where streamName is expected, under certain circumstances, a malicious hacker might execute arbitrary commands within vulnerable PHP applications created with Zend.
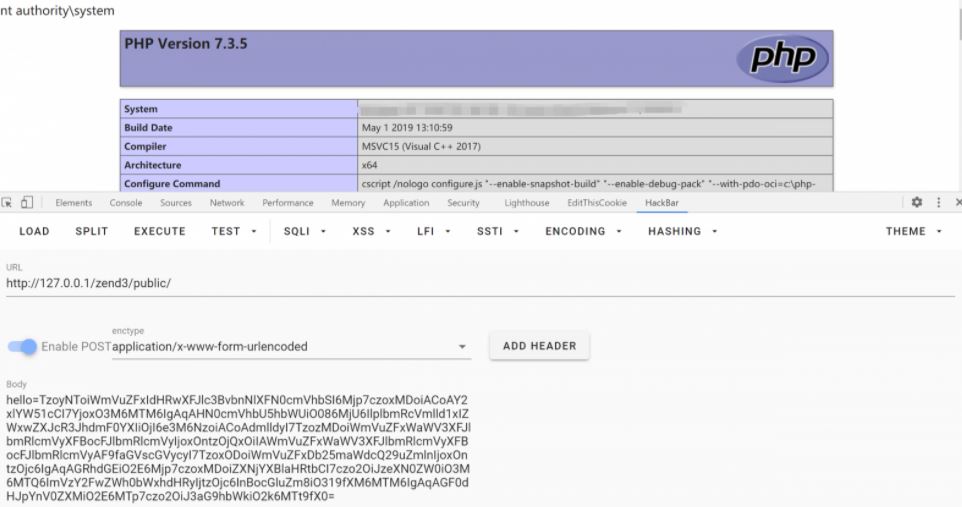
PHP operates on about 80% of active websites, not to mention the popularity of Zend Framework. System administrators are advised to check their web applications in detail to prevent the exploitation of the attack.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











