Cybersecurity experts revealed the finding of a third malware variant directly involved in the SolarWinds supply chain cyberattack. Identified as Sunspot, this variant was discovered after the Sunburst/Solorigate backdoor and Teardrop malware, however, this may have been the variant that triggered the entire attack.
CrowdStrike experts, responsible for the finding, have invested considerable efforts trying to track down the threat actors behind the SolarWinds attack, concluding that groups like StellarParticle participated in this incident. Everything indicates that hackers used Sunspot to inject the Sunburst backdoor into compromised updates.
Researchers note that Sunspot monitored linked running processes in Orion compilation and replaced one of the source files to include backdoor code in the update: “This malware had the necessary mechanisms to prevent compromised Orion builds from failing, as this could alert administrators to the presence of malicious code” , the experts mention.
When the malware detected a build command, the malicious code was inserted into the Orion application and created a corrupted version of the legitimate software. The attackers put a lot of effort into developing Sunspot code to ensure that the injection went unnoticed.
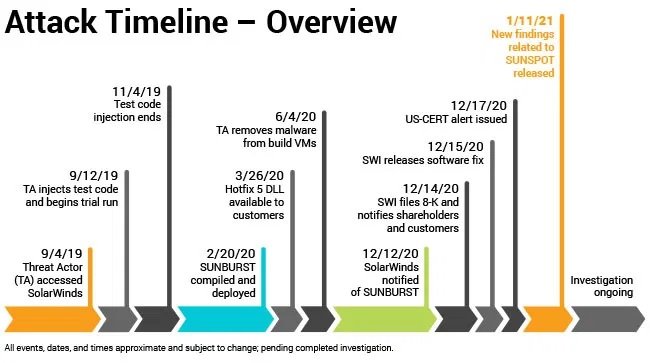
Experts included engagement indicators (IoCs) in the report to detect this new variant of malware. On the other hand, SolarWinds also published an update on the attack, adding that Sunspot was injected into vulnerable deployments between March and June 2020, although threat actors ran their first tests even months before the hacking campaign began.
“Our investigation concluded that the incident began as of September 2019, when we started detecting suspicious activity on our systems,” the SolarWinds report says. It appears that the Orion update for October 2019 already had samples of this malware.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











