Experts from Project Zero, Google’s main research team, discovered a sophisticated hacking campaign targeting users of Windows and Android systems. For the launch of an initiative dedicated to designing zero-day vulnerability detection techniques, experts discovered a complex hacking campaign deployed during the first months of 2020.
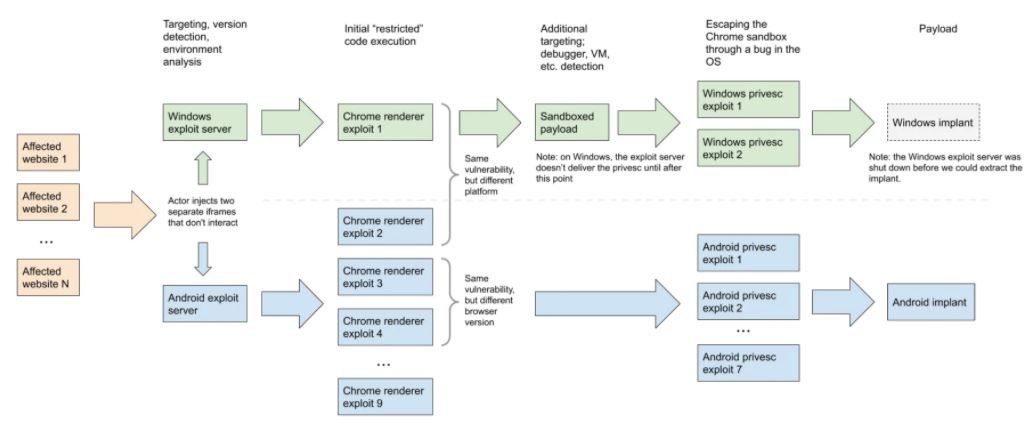
The attacks were specifically targeted at Android and Windows users, exploiting multiple vulnerabilities present in these systems and which in turn were chained to other faults in the Chrome browser: “We detected two servers that offer different chains of exploits through a variant known as ‘watering hole attack’. One server attacked Windows users, while the other was targeted at Android systems,” the specialists mention.
This is an attack variant in which malicious hackers inject malware into third-party websites widely used by individuals and organizations, infecting them indirectly. These attacks are highly effective, as infection from a single third-party site can compromise dozens or even hundreds of organizations.
As mentioned above, both exploit servers used vulnerabilities in Chrome for the initial execution of malicious code. The operators of this campaign used zero-day vulnerabilities in Windows and Chrome, while Android attacks exploited known flaws, however, attackers are not ruled out to have zero-day exploits for the mobile operating system.
According to the experts, the following codes were found on exploit servers:
- A renderer that exploits four vulnerabilities in Chrome (including a zero-day flaw)
- Two sandbox bypassing exploits for the affected systems. These exploits abused three zero-day vulnerabilities in Windows
- A privilege escalation kit, consisting of a number of known exploits present in some earlier versions of Android
Project Zero highlights the sophistication of this campaign, as operators seem to have all the inputs needed to deploy these complex attacks: “Attackers employ complex and well-designed code, as well as employing a wide variety of exploits and a rare attack vector,” adds the company report. It is not known whether this hacking group is sponsored by any nation state, although researchers have not ruled out this possibility.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











