Cybersecurity specialists published a report regarding the finding of at least 7 vulnerabilities detected in a popular DNS software package deployed on routers and access points in all kinds of organizations. This set of flaws, dubbed DNSpooq, resides in Dnsmasq, the DNS forwarding client for *NIX-based operating systems.
Dnsmasq is included in the firmware of multiple network devices to provide DNS forwarding capabilities when taking DNS requests made by local users, forwarding the request to an upstream DNS server, and caching the results, so the same results are available to other clients without the need for a new upstream DNS query. This software is found on signature devices such as Cisco, ZTE, Huawei, D-Link, among others.
The detected flaws are considered dangerous because they can be exploited in combination to poison DNS cache entries registered by Dnsmasq servers. This is a serious problem for developers as it would allow threat actors to redirect vulnerable users to malicious websites. For example, if hackers manage to abuse a DNSpooq attack to poison DNS cache entries for gmail.com on the Cisco router of a target organization, they could redirect all connected employees to a fake Gmail page while the browser displays the legitimate address (gmail.com) in their browsers.
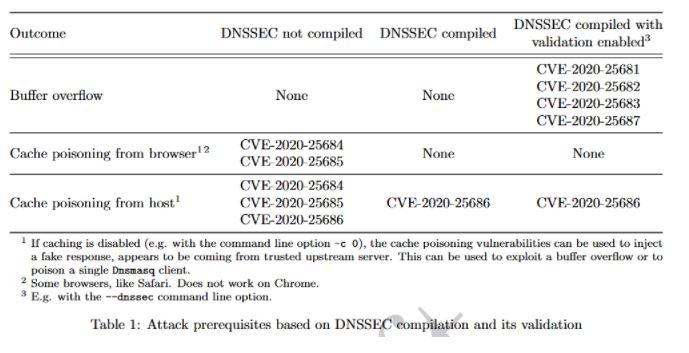
As mentioned above, seven DNSooq vulnerabilities were detected; four of these flaws are buffer overflows that could lead to remote code execution; the remaining three flaws allow DNS cache poisoning.
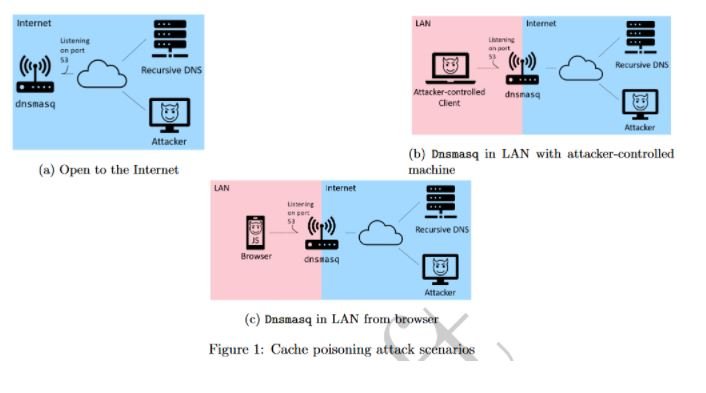
While it is relatively easy to exploit these vulnerabilities altogether over the Internet, experts point out that it is also possible to attack these devices on internal networks by abusing compromised computers connected to the same network.
JSOF specialist Shlomi Oberman says these flaws are more common than they seem: “DNS poisoning flaws are not difficult to eliminate, although their exploitation can be easily automated for the use of botnets, phishing programs, among other malicious campaigns,” Oberman says.
The required updates will be released earlier this week, so developers are advised to use Dnsmasq to install the patches as soon as possible.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











