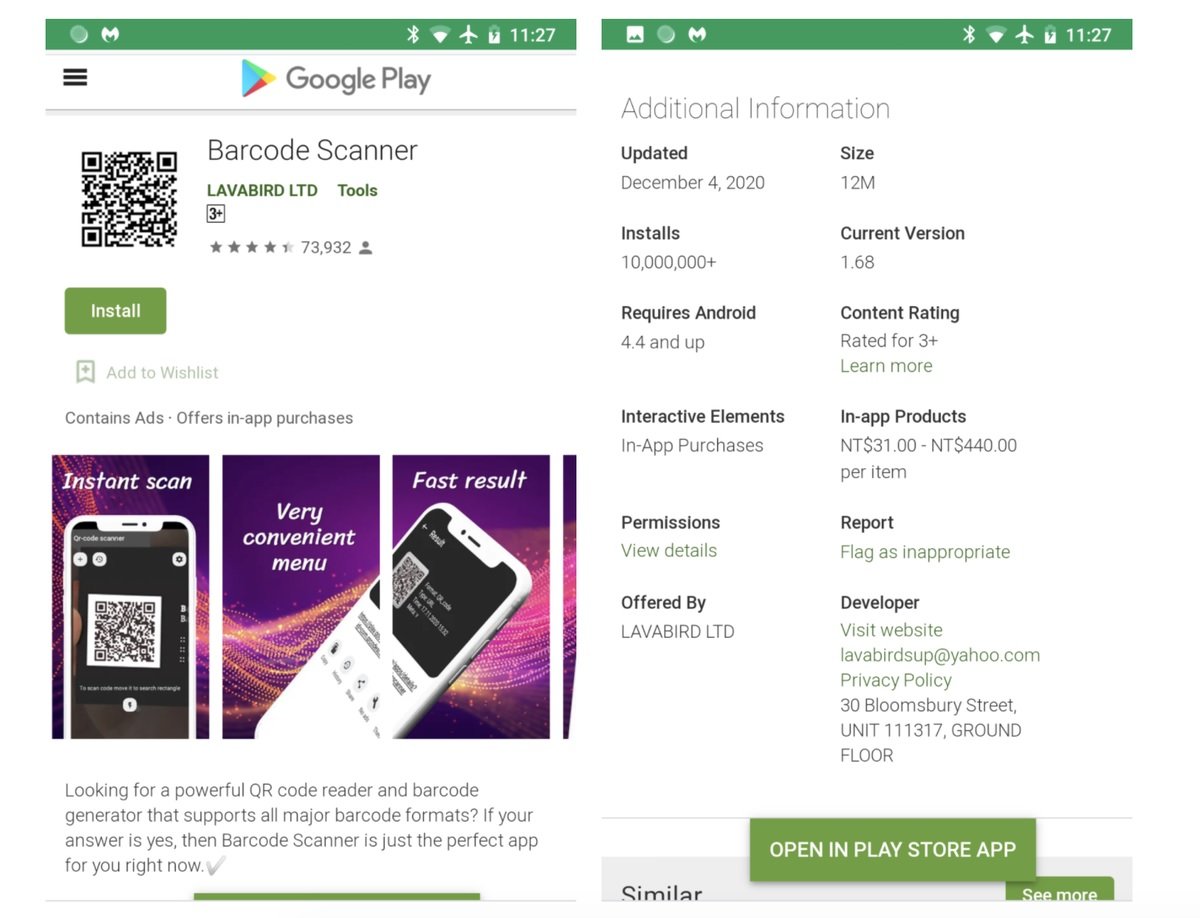
Approximately 10 million smart devices with Android system would have been exposed to cyberattacks after the Barcode Scanner app, a popular barcode scanning tool, received a malicious update that rendered it into a dangerous malware variant. The app, available on the official Google Play platform, offers a QR code reader and barcode generator, which made it a very popular tool.
According to a report prepared by security firm Malwarebytes, multiple users began reporting anomaly behavior in the application, which always gave the impression of being legitimate and secure software. Although in similar cases this behavior is related to unwanted advertisements and malicious advertising connected to new applications, users claimed not to have installed tools related to Barcode Scanner, developed by Lavabird Ltd. However, after a brief analysis experts discovered the problem with the app.
Issues started from the release of a software update that modified the feature to show ads without notice. Specialists mention that many developers decide to release unforeseen updates to turn their apps into overnight advertising machines, seeking higher advertising revenue or forcing their users to purchase a paid subscription.
“Users can access free versions of an app, allowing developers to earn advertising revenue. However, sometimes creators of software development kits (SDKs) for advertising can make highly aggressive modifications, affecting the user experience,” specialists say.
Although in most cases these changes are attributed to third parties, the Malwarebytes report mentions that the malicious code was included directly in the latest update of Barcode Scanner, intentionally hidden by the app’s developers. Researchers even detected the same security signature used in previous updates.
After receiving the report, Google decided to remove this app from its official store and begin research on the developers. It should be mentioned that the risk remains dormant for users who continue to use this app, so it is recommended to uninstall it from any device as soon as possible.
This is an attack vector used by malicious developers to try to evade security mechanisms in the Google Play Store, so specialists fear that more similar cases will appear shortly. Another similar method is the implementation of motion sensor checks, i.e. malware variants that are activated until the user physically interacts with their infected device, an attack primarily employed by bank Trojan operators a couple of years ago.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











