A malvertising campaign operator group known as ScamClub has long exploited an unpatched zero-day vulnerability in some WebKit-based web browsers in order to bypass security mechanisms and redirect unsuspecting users to malicious websites where gift card stays.
The term malvertising refers to injecting malware into online advertising in order to deploy subsequent attacks. Threat actors can take advantage of security flaws in legitimate advertiser software or place malware on their own platforms.
This fraudulent campaign was first detected in June 2020 and appears to remain active despite security updates released to fix the flaws exploited by hackers. According to the report, this is a typical ScamClub campaign, which employs a multi-layered payload, starting with an ad tag hosted on a malicious CDN. This report was prepared by security firm Confiant.
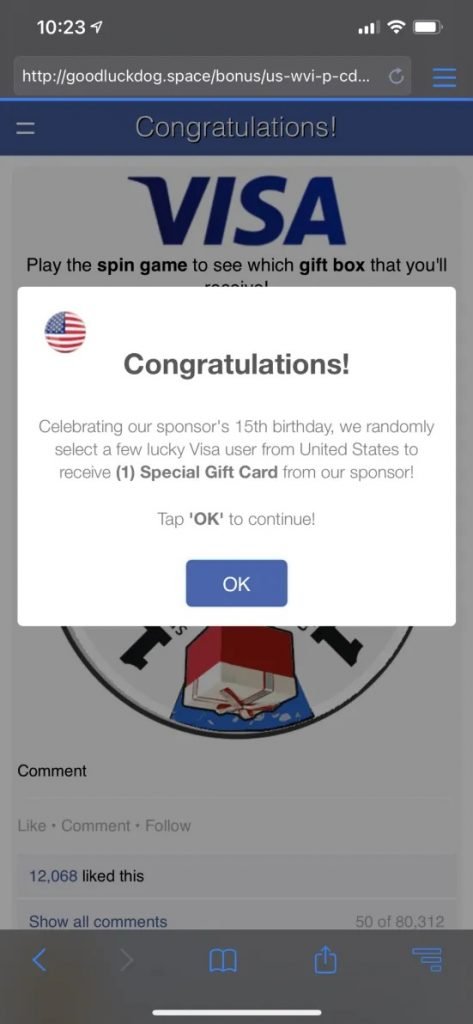
Experts mention that this group has been active for over a decade, primarily attacking users of iOS devices with online scams with which they seek to trick users into handing over their confidential information. In their most recent campaign, hackers use an advanced technique to bypass the isolated environment of iframe HTML, a sandbox whose main function is to prevent the website from interacting with malicious code.
ScamClub operators exploit an error in the way the WebKit engine handles event detection in JavaScript, redirecting users from legitimate sites to malicious web domains.
“The sandbox attribute ‘allow-top-navigation-by-user-activation’, considered to be one of the most important tools of anti-malvertising mechanisms, should prevent any redirection unless proper activation is performed. Activation in this context means a tap or click within the frame,” the experts mention. In other words, although redirection should not occur under any circumstances, errors in browsers like Safari allow the attack to complete successfully.
Experts emphasize the fact that the flaw exploited by hackers only works in webkit engine-based browsers, such as Safari and Google Chrome for iOS devices. The report mentions that at least 50 million malicious advertisements have been detected, reaching up to 15 million in a single day. Because the campaign is still active experts recommend ignoring any online ads asking users to deliver sensitive information, which is the clearest indication that this is a scam.
To learn more about information security risks, malware, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











