Multiple government agencies in the US have issued separated data breach notifications regarding a ransomware attack targeting that resulted in information leaking from the Automatic Funds Transfer Service (AFTS), a payment processing and address verification platform widely used by government organizations.
AFTS manages a considerable amount of sensitive data, so this incident could have disastrous consequences equal for individuals and organizations.
According to these reports, the infection affected government systems in various cities in states of Washington and California, including vehicle departments and local government offices.
Because of the large amount of potentially sensitive data involved in this incident, affected local governments have implemented some security measures, starting with reporting the attack to federal authorities. These reports mention that the compromised information may include full names, addresses, email addresses, telephone numbers, license plate numbers and financial documents, among other information.
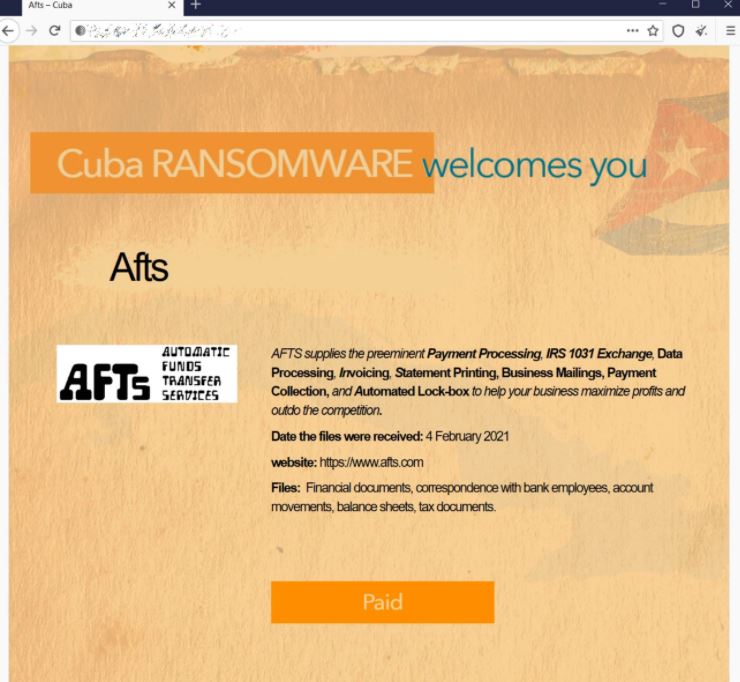
Everything indicates that the attacks occurred in early February, when a group of threat actors identified as “Cuba Ransomware” managed to infect the compromised networks to steal sensitive information and encrypt the affected systems.
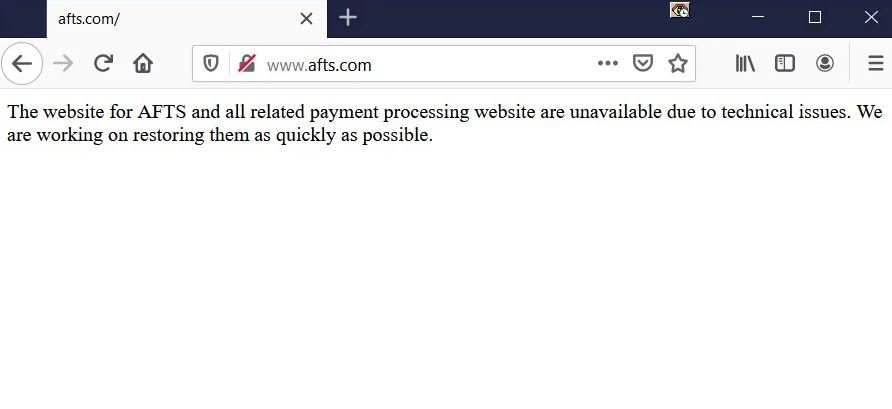
This attack caused a significant disruption to regular AFTS operations, so the AFTS website is temporarily down and payment management works at a slower pace: “The AFTS website and all payment processing-related services face technical issues,” an alert posted on the company’s website mentions.
Like other ransomware incidents, Cuba’s operators stole sensitive information before encrypting affected systems, probably with the intention of selling it in illegal forums. After an initial infection, Cuba begins to spread over the compromised network, stealing login credentials and triggering encryption of attacked systems. On their website, used to post threats to victims, hackers claim to have stolen financial documents, internal and external correspondence, and company balance sheets, among others.
In case affected organizations ignore the ransom demand, cybersecurity experts believe that hackers could post this information for free on various illegal platforms. Cuba ransomware operators could also deploy additional campaigns using compromised information, including complex phishing and social engineering campaigns.
To learn more about computer security risks, malware, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











