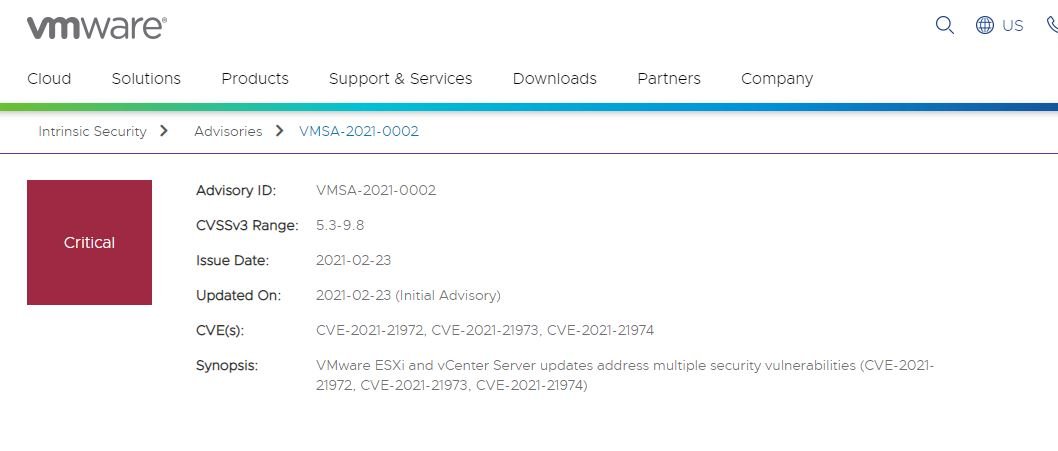
Cybersecurity specialists reported the finding of a critical vulnerability in VMware vCenter Server. Tracked as CVE-2021-21972, this is a Remote Code Execution (RCE) flaw that could be exploited by threat actors to take full control of affected systems. Fixes for this vulnerability are now available.
About the compromised solution, vCenter Server is a centralized management utility for VMware. This development is used for the management of virtual machines, ESXi hosts, and any dependent components from a single centralized location. It is important to mention that the vulnerability can be exploited by remote threat actors without requiring target user interaction.
The expert report mentions that the VSphere Client (HTML5) is affected by a remote code execution flaw in the mentioned plugin; the flaw would have received a score of 9.8/10 on the Common Vulnerability Scoring System (CVSS) scale, making it a critical vulnerability.
On exploitation, the researchers add: “Threat actors with network access to port 443 could abuse this condition by executing commands on the elevated compromised system.”
The flaw was initially reported by researcher Mikhail Klyuchnikov of Positive Technologies. In his report, the expert mentions that the failure affects the vCenter Server plug-in for vROP, available by default on all installations. VROPRs do not need to be present for this endpoint to be available. The virtualization solution provider has provided some solutions to disable it.
The company recommends upgrading vulnerable vCenter Server installations to U3n, 6.7 U3l, or 7.0 U1c versions as soon as possible to fully mitigate the risk of exploitation. VMware also provided some detailed instructions for implementing workarounds for CVE-2021-21972 and CVE-2021-21973, another recently fixed flaw. Eventually the company corrected an overflow failure identified as CVE-2021-21974, present in VMware ESXi. Threat actors could exploit this flaw to lead to arbitrary code execution on affected systems.
To learn more about information security risks, malware variants, vulnerabilities and information technology issues, feel free to access the International Institute of Cyber Security (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











