Recent reports report multiple hacking incidents related to the exploitation of a zero-day failure on the Accellion FTA file transfer platform, although the latest may be the most devastating yet. This wave of attacks would have begun in December 2020, leading to the theft of multiple files stored by organizations using a vulnerable version of this protocol.
This malicious campaign was attributed to the Clop ransomware group, which has extorted dozens of victims demanding cryptocurrency transfers in exchange for not filtering compromised information. Accellion FTA operates as a set of servers independent of the main networks in organizations that use this platform, so these incidents do not necessarily involve the commitment of internal networks although data extraction cases do occur.
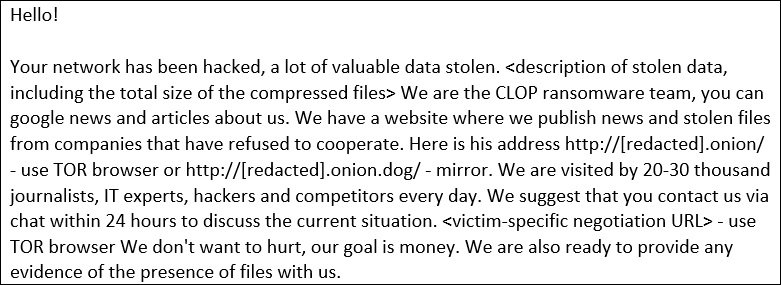
Victims of these threat actors include companies of all kinds, including renowned law firm Jones Day, technology developers Danaher, technical services company ABS Group, among many other organizations.
The cybersecurity community has confirmed that the latest victim of these hackers is the cybersecurity firm Qualys, as cybercriminals have posted multiple screenshots on their website demonstrating the commitment of this firm. Leaked information, extracted from your Accellion FTA implementation, includes invoices, purchase orders, financial reports, among other sensitive details.
The report mentions that the compromised Accellion implementation resides at fts-na.qualys, and its associated IP address was assigned to the company’s network. In response to fault detection, Qualys decided to close this deployment on February 18 last. So far it is unknown whether the cybersecurity firm received a ransom note from hackers, just as incidents previously linked to Clop. Although this appears to be a new Clop attack, experts do not rule out an attack in conjunction with other threat actors to share sensitive files and deploy subsequent attacks.
What are your thoughts about this security incident? Are they expecting to get a ransom? Are you willing to learn more about cybercrime? To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS).

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











